[ad_1]
Howdy folks,
In 2020, we made a recommendation to developers to use the Microsoft Authentication Library (MSAL) and the Microsoft Graph API when developing applications. Since then, we’ve continued to add capabilities to both MSAL and Microsoft Graph, including improvements in performance, security, and reliability. We’ve also added hundreds of new APIs, including Continuous Access Evaluation-enabled APIs and Conditional Access authentication context to Microsoft Graph. These are now available for developers using MSAL and allow them to build Zero Trust-ready applications.
Since we’re ending support for Active Directory Auth Library (ADAL) and Azure Active Directory Graph on June 30, 2022, this is a reminder to update your apps to use MSAL and Microsoft Graph. We’ve also made it easier for you to find all the apps that are still using ADAL.
Find the apps still using ADAL and Azure AD Graph
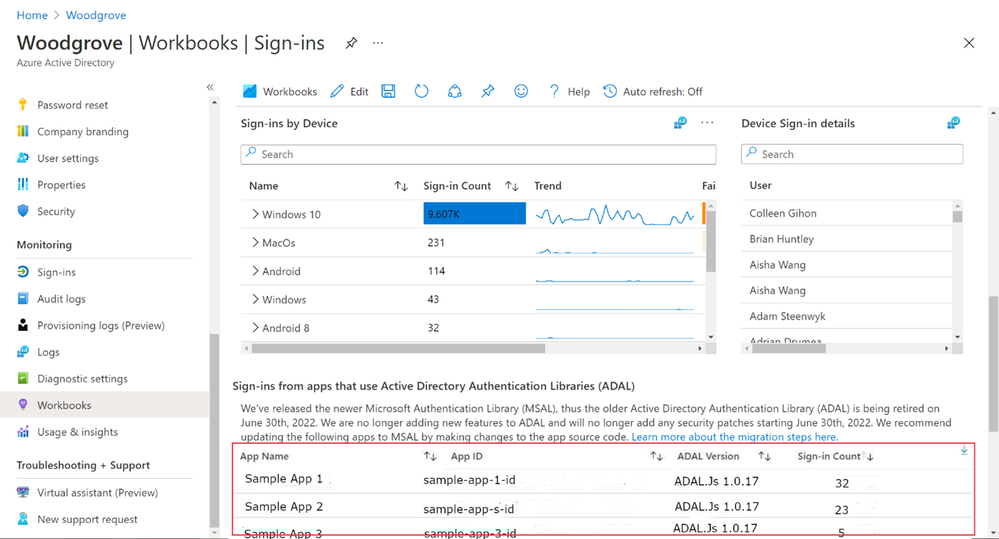
The Azure AD monitoring workbook can help you find applications that use ADAL. This uses a set of queries that collect and visualize information available in Azure AD sign-in logs. You can also use the sign-in logs directly using the sign-in logs schema here.
To access the workbook:
- Sign into the Azure portal
- Navigate to Azure Active Directory > Monitoring > Workbooks
- In the Usage section, open the Sign-ins workbook
The Sign-ins workbook has a new table at the bottom of the page that shows you which recently used apps are using ADAL. You can also export a list of these apps.
Once you’ve identified the apps that are using ADAL, you can use the MSAL migration guide. To find apps that use Azure AD Graph, search your code for the string “graph.windows.net” and then use the Microsoft Graph migration guide.
Send your questions, open issues, and feature requests through Microsoft Q&A by using the tag azure-ad-adal-deprecation or azure-ad-graph-deprecation.
As always, we’d love to hear your feedback or suggestions. Let us know what you think in the comments below or on the Azure AD feedback forum.
Best regards,
Alex Simons (Twitter: @Alex_A_Simons)
Corporate Vice President of Program Management
Microsoft Identity Division
Learn more about Microsoft identity:
[ad_2]
Source link