[ad_1]
Hey there! We are delighted to announce the general availability of four new detections in Azure Active Directory (Azure AD) Identity Protection, further expanding our identity threat detection surface area in cloud applications and at endpoints to enhance our comprehensive identity risk signal.
We have four new partner detections:
- Unusual Additional of Credentials to an OAuth App
- Mass Access to Sensitive Files
- Possible Attempt to Access Primary Refresh Token (PRT)
- Workload Identities Leaked Credentials
These are all great examples of how Identity Protection integrates threat intelligence from Microsoft Defender for Cloud Apps, Microsoft Defender for Endpoint, and GitHub to protect all your identities – both workload and user identities.
With these new detections, we’ve expanded the surface area where Identity Protection can detect identity compromise and seamlessly kick off remediation. As the persistence of attacks continues to increase and their novelty amplifies, every minute of detection and remediation counts. With Azure AD Conditional Access user or service principal risk policies, you can automatically remediate your user accounts or block the service principals when they’re at risk. These new detections significantly enhance Identity Protection’s ability to detect identity compromise and seamlessly kick off remediation using diverse signals.
Understanding Microsoft’s Identity Threat Intel Ecosystem
Integrating threat intelligence from Microsoft’s internal threat detection ecosystem and outside researchers, law enforcement, and partners is a core component of the Identity Protection risk engine. As the security products across Microsoft detect new attack techniques and refine existing detections, we are committed to integrating detections that will be most impactful for our customers in identifying credential compromise. The detections we announced today bring the signal from Microsoft Defender for Endpoint, Microsoft Defender for Cloud Apps, and public GitHub repositories as Identity Protection risk detections that influence identity risk for users and workloads. New reporting and remediation options from within Identity Protection simplify the work of your Identity admins.
And work is already in progress to integrate even more diverse signals into Identity Protection. Additionally, we welcome the increasing number of third-party ISVs and threat detection providers that are integrated into Identity Protection via our riskyUsers API. This enables any third party whose customers have Azure AD Identity Protection to configure the ability to confirm users as compromised based on their threat intelligence.
Gaining value from the new detections
Getting started with these new Microsoft detections couldn’t be easier – because if you’re already using Microsoft Defender for Endpoint and Microsoft Defender for Cloud Apps, these premium detections will automatically be integrated into Identity Protection. You can find these detections in the “Risk detections” report and in the user or workload identity user risk history. For Mass Access to Sensitive Files, you can also see it in the Risky Sign-ins report, since we’re able to match that anomalous activity to a specific authentication request and show you the sign-in details.
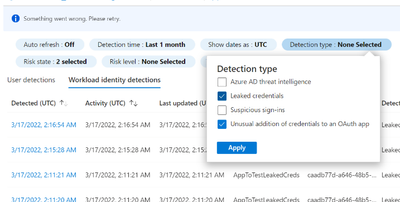

The integration with GitHub for Leaked Credentials is similarly seamless. Organizations have struggled with the issue of explicit credentials-in-code for a long time. To address that, we are extending our coverage of these leaked credentials in Identity Protection to cover public code artifacts in GitHub and flag valid app secrets in Identity Protection for Workload Identities experience. GitHub scans for secrets across public code artifacts and sends them to Azure AD for validation—no configuration necessary in your tenant. If valid, Identity Protection generates a risk detection for the account and flags the Key ID for the secret, which you can see in the Risk detections report. Using the link in the Additional info property, you will be taken to the GitHub file with the suspected Leaked Credentials. To remediate, remove the secret that Identity Protection flagged as compromised.
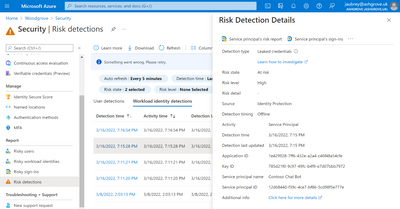
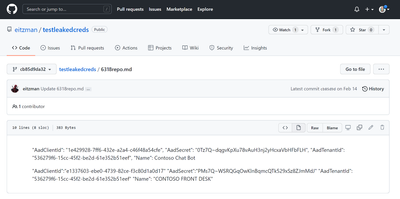
We know some of you prefer to programmatically access Identity Protection risk data or export it to your own SIEM so we’ve made both of these actions easy. You can also query all four of these detections using our APIs for service principal risk and user risk detections APIs. With only a handful of clicks, you can configure Azure AD diagnostic settings to send risk data to a Log Analytics workspace, archive it to a storage account, stream it to an event hub, or send it to a SIEM solution.
What’s next?
We know that having the most comprehensive identity compromise signal is critical to keeping you and your organization safe. To best leverage these new signals and the other wealth of identity threat intelligence in Identity Protection, we recommend configuring risky service principal, risky user, and risky sign-in policies for automatic remediation. Identity Protection will continue to integrate signals from security products across Microsoft and from our partners to have the most precise and relevant identity risk engine.
Stay tuned for new signals and for greater convergence across the security products—we can’t wait to share what’s next with you! And as always, I’d love to hear from you! (Twitter:@alex_t_weinert)
Learn more about Microsoft identity:
Source link