[ad_1]
Microsoft 365 supports Information Rights Management (IRM) encryption and sensitivity labels with IRM encryption to provide permission control of sensitive content. While this supports most use cases, using encrypted content in delegation and shared mailbox scenarios has some inconsistencies across clients.
Current behavior
Delegate access: when delegates are granted FullAcccess to the owner’s mailbox, their access to encrypted mail varies depending on the Outlook client they are using:
- Delegated access of encrypted mail is supported using Outlook on the web (OWA), Outlook for Mac, Outlook for iOS, Outlook for Android and Mail app on Windows
- Outlook for Windows client does not support delegate access of encrypted messages and delegates are blocked from reading encrypted messages if they are not on the recipient list (To, Cc or Bcc).
Based on this behavior, users can simply access the encrypted message via OWA or one of the other clients delegates are not blocked.
Shared mailbox access: for shared mailboxes, the challenge is slightly different. By design, users can open encrypted messages for a shared mailbox when they meet the following conditions:
- For Outlook for Windows, when the user is assigned “FullAccess” rights to the shared mailbox, and the AutoMapping parameter of Set-MailboxPermission is set to $true.
- For other Outlook clients, when the user is assigned “FullAccess” rights to the shared mailbox.
- Known client limitations can be found here.
This means that once a user or group is granted “FullAccess” to a shared mailbox, they have access to all shared mailbox content from Outlook (OWA, iOS, Android, Mac, and Mail app on Windows). This is often unacceptable in scenarios where a shared mailbox contains encrypted content that is appropriate only for a subset of the users who have been granted “FullAccess.”
For more information, see Manage permissions for recipients in Exchange Online, which tenant admins could use to limit delegate access to encrypted.
New behavior: Mailbox Encrypted Message Access
Based on customer feedback, we are introducing new Get/Set/Remove-MailboxIRMAcess cmdlets that provide admins with more granular access control of encrypted content, including in scenarios where delegates or shared mailbox members have FullAccess to the shared mailbox.
Check who is blocked from accessing mailbox owner’s encrypted messages:
Get-MailboxIRMAccess -Identity <MailboxIdParameter> -User <SecurityPrincipalIdParameter>
Blocked a user from reading encrypted messages in a shared or delegated mailbox:
Set-MailboxIRMAccess -Identity <MalboxIdParameter> -User <SecurityPrincipalIdParameter> -AccessLevel <Block>
Remove a user from the block list and allowing them to read encrypted mail:
Remove-MailboxIRMAccess -Identity <MalboxIdParameter> -User <SecurityPrincipalIdParameter>
After any of the above mailbox settings are changed, the Outlook client must be restarted.
Parameter definitions:
- -Identity: The target mailbox. You can use any value that uniquely identifies the mailbox.
- -AccessLevel: Specifies what delegates can do with IRM-protected messages in the specified mailbox. Currently we only support “Block.”
- -User: Specifies the delegate or shared mailbox member who is blocked from reading IRM-protected messages in the mailbox or shared mailbox. The user’s login ID must be used.
Let’s cover some scenarios!
Scenario 1 – Delegate top secret conversation (total block)
Ashima is a VP of Finance at Contoso. Katie is Ashima’s Administrative Assistant, who has full access to Ashima’s inbox. Ashima has been involved in discussions to purchase another company with the CEO. This could have a high impact on the stock price if this information is leaked. Later, Ashima receives an email from the CEO that is only for the senior leadership team and protected by a Top-Secret label. Although Katie has access to Ashima’s mailbox, she should not be able to see this email, as it’s meant only for members of the senior leadership team.
With the new behavior, the admin can use the following cmdlet to block Katie’s access to encrypted messages in Ashima’s mailbox while still allowing Katie full access to non-encrypted messages:
Set-MailboxIRMAccess -Identity "Ashima@contoso.com" -User "Katie@contoso.com" -AccessLevel Block
Scenario 2: Shared mailbox select access to encrypted messages (only a subset of users can access encrypted content)
Contoso has a shared mailbox (CustomerData@contoso.com) that is used to receive encrypted emails containing customer data from the company’s customer portal. Every day, several employees check the mailbox and route emails to the right departments or contacts. This mailbox also receives notifications or wrongly delivered emails. The admin wants to assign a few employees to clean up the mailbox but does not want them to be able to read encrypted messages sent from the company customer portal. To do this, the admin runs:
Set-MailboxIRMAccess -Identity "customerdata@contoso.com" -User "cleaner@contoso.com” -Accesslevel Block
Blocked user experience
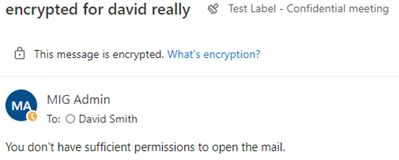
Once a delegate is blocked from viewing a mailbox owner’s protected messages, the delegate will see the following when they try to open protected emails:
If a shared mailbox member is blocked from viewing protected email in the mailbox, the user will see the following when they try to open protected emails:
When will this feature be available?
The new cmdlets are rolling out to tenants right now, and Outlook clients (OWA, Mac, iOS, Android, Mail app on Windows) will support the new setting by the end of June 2022.
What about Outlook for Windows?
The new block setting does not affect Outlook for Windows, which already has the ability to block access today, as described above.
We hope you find the new behavior useful!
Source link