[ad_1]
Howdy folks,
I’m happy to announce the general availability of Temporary Access Pass (TAP). We’ve made a lot of progress since we announced the public preview of TAP.
“…We use the MS Authenticator for passwordless sign in. That is the only way employees can access resources.
Enrollment is based on TAP, and we do not hand over a traditional password to the users…” – Global Toy Manufacturer, EU
I’ve asked Tim Larson, one of the Product Managers behind this release, to give you the low down on all these updates, and explain how you can start using TAP to address many of your passwordless account onboarding and recovery scenarios. You’ll find Tim’s blog post below.
Best regards,
Alex Simons (Twitter: @alex_a_simons)
Corporate Vice President, Product Management
Microsoft Identity Division
—————-
Hi everyone,
I am excited to share with you the changes and improvements we’ve made and how you can start using TAP to progress on your passwordless journey!
What is TAP?
TAP is a time-limited passcode that allows users to register passwordless authentication methods and recover access to their account without needing a password. You can also use a TAP to set up Windows devices, whether your users are directly setting up their own devices or they’re using Windows AutoPilot, joining devices to Azure AD, or even setting up Windows Hello for Business.
Admin experience
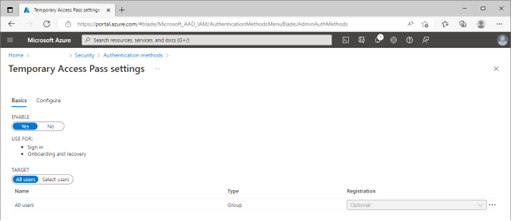
You can set up and configure TAP for your organization with the authentication methods policy. For example, you can limit TAP assignment to specific users and groups, limit the use for a short period, or set it for one-time use.

Once the authentication method is enabled by policy, a privileged authentication administrator or an authentication administrator can create a TAP for the user either by visiting the user’s authentication methods blade or accessing via an API. We’ve also added the ability for admins to override existing TAPs. If a user forgets or loses a TAP that was previously created, just follow the same process to add a TAP to the user’s account, and we’ll handle the deletion of the old one.
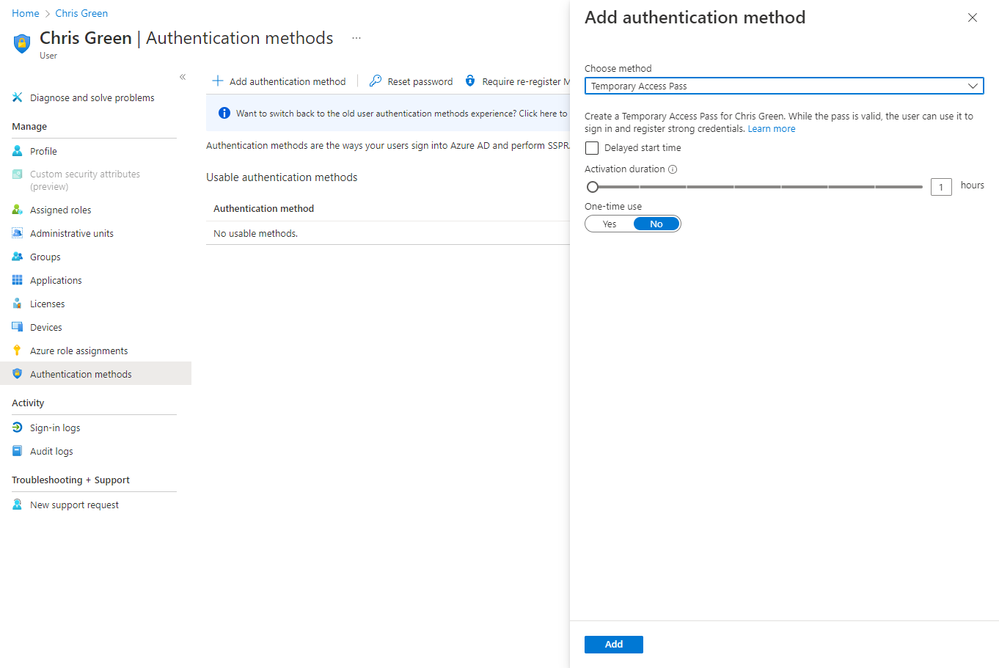
End user experience
Once a user has a valid TAP, they can use it to sign in and register security information, such as passwordless phone signin directly from the Authenticator app, to add a FIDO2 key from the My Security Info page, or even to set up Windows Hello for Business on Azure AD Joined and Hybrid Azure AD Joined machines. In scenarios where MFA is required, TAP can also be used as an additional factor.

Learn more
You can learn how to configure TAP in our documentation.
New employee onboarding experiences can vary for every organization. TAP is available through the Microsoft Graph APIs, so you can incorporate it into your existing applications or your HR driven provisioning process. Learn more about policy APIs to configure TAP to suit your needs.
Tell us what you think
We hope TAP helps you on your passwordless journey—give it a try and let us know if you have questions or feedback.
Tim Larson (@tim_c_larson)
Senior Product Manager
Microsoft Identity Division
Learn more about Microsoft identity:
[ad_2]
Source link