[ad_1]
I’m excited to announce the general availability of provisioning to on-premises applications using Microsoft Entra Identity Governance. You can now automate provisioning and manage the lifecycle of users in on-premises applications, without requiring any custom code.
Many of you are already using Microsoft Entra Identity Governance to easily provision identities into hundreds of SaaS applications using the built-in connectors. You can now provision identities from Azure Active Directory (Azure AD) directly into on-premises applications that rely on user identities stored in a SQL database, LDAP directory (other than Active Directory Domain Services) or support the SCIM standard for provisioning. This means you can use Microsoft Entra Identity Governance to govern access to on-premises applications with out-of-the-box on-premises connectors and no custom coding required!
Let’s walk through an example of how an organization, Contoso, uses Microsoft Entra Identity Governance to provide access to an on-prem application that manages critical manufacturing processes. The application is deeply embedded in the organization and has been around for years. It doesn’t support modern SCIM APIs for user management, but it does rely on an OpenLDAP server to manage user access. With Microsoft Entra Identity Governance, Contoso can:
- Increase employee productivity by automating application access.
- Manage costs by deploying a cloud-based provisioning solution.
- Manage risk by periodically reviewing and revoking access.
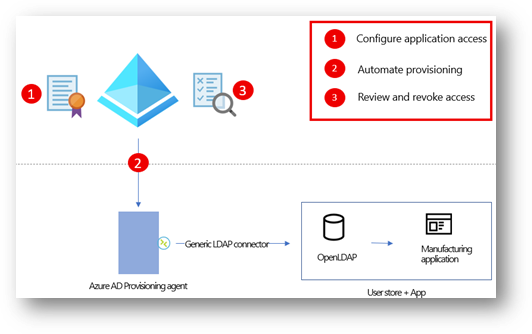
In three easy steps, the admins at Contoso enable users to access on-premises applications, while ensuring the necessary governance processes are in place:
1. Configure application access
When employees join the organization, they are marked as hired in Workday and have an account automatically provisioned in Azure AD. The administrators have configured an access package with entitlement management. When a new employee in the manufacturing department is hired, they are automatically assigned access to the manufacturing app through the access package. When employees leave, or change jobs, their assignment is automatically removed, so they can no longer access that application.
There are some users that need time-limited access to the manufacturing app that aren’t in the manufacturing department. To accommodate this requirement, the admins at Contoso have a second policy that allows other employees to request access to the application via an access package.
All users that need access are either automatically granted access or can self-service request the access they need.
2. Automate provisioning accounts
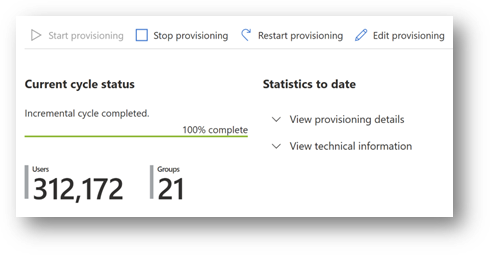
The manufacturing app is on-premises and doesn’t support modern standards such as SCIM, but it does have an OpenLDAP server used for access control. The administrators use the generic LDAP connector that Azure AD provides and sets up provisioning. Users that are granted access to the manufacturing application through an access package automatically have accounts provisioned.
The admins at Contoso can take advantage of the out of the box LDAP connector and automate provisioning, without needing to modernize their application.
3. Periodically review and certify access
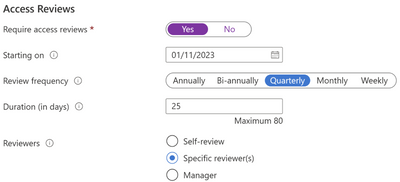
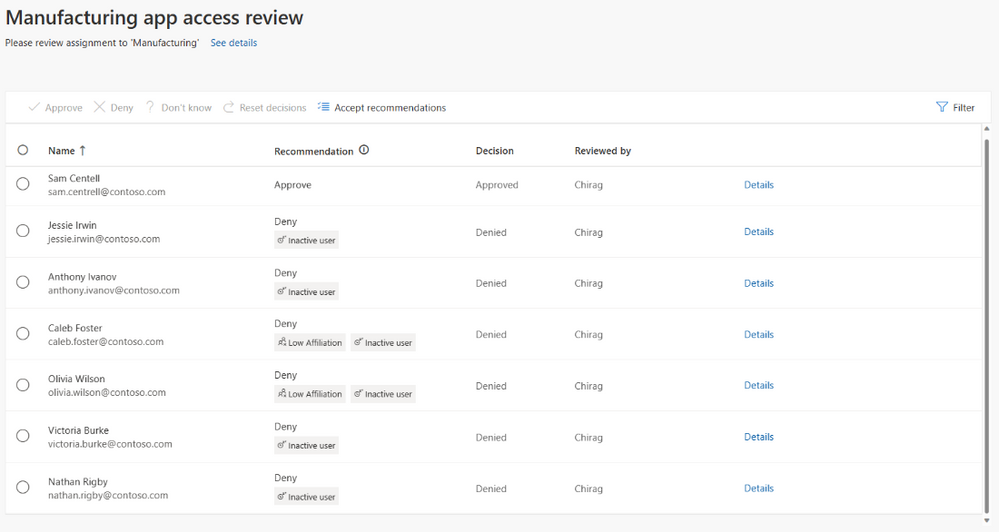
The manufacturing app has business critical data and Contoso is required as part of compliance processes to ask employees outside of the manufacturing department to regularly confirm that they need access and provide a justification. The administrators of Contoso set up a multi-stage access review of non-manufacturing users that have access to the app. First, the employee self-attests to requiring access, and then the review is transferred to the application owner for final approval. Users that do not complete the access review are automatically removed from the application.
Internal and external audit requirements are satisfied as the right access controls and reviews are in place and the “why” access exists can be proven.
Together with Azure AD’s entitlement management, provisioning, and access review capabilities, Contoso is able to provide access to both SaaS and on-premises applications while ensuring governance and security requirements are met. Go enable this new capability today and start governing access to on-prem applications in the same way you do your SaaS applications.
This is just the beginning of on-premises support from Microsoft Entra Identity Governance. We’ll continue to invest more, including the ability to provision using PowerShell, Web Services, and other custom connectors to line of business applications so that customers using Microsoft Identity Manager (MIM) can migrate their provisioning capabilities to Microsoft Entra Identity Governance.
We love hearing from you, so share your feedback on these new features through the Azure forum or by tagging @AzureAD on Twitter.
Joseph Dadzie, Partner Director Product Management
Twitter: @joe_dadzie
LinkedIn: @joedadzie
Learn more about Microsoft identity:
[ad_2]
Source link