[ad_1]
Howdy folks!
At Ignite 2022, we announced the general availability of Azure Active Directory (Azure AD) Certificate-Based Authentication (CBA) as a part of Microsoft’s commitment to Executive Order 14028, Improving the Nation’s Cybersecurity. Now, we’re thrilled to announce the general availability of Azure AD CBA support on mobile.
We support both on-device certificates and external hardware security keys, like YubiKeys over USB or NFC on iOS and Android devices. With Bring Your Own Device (BYOD) on the rise, this feature will give you the ability to require phishing-resistant multi-factor authentication (MFA) on mobile without having to provision certificates on the user’s mobile device.
To tell you more about the support for Azure AD CBA on mobile, I’ve invited Vimala Ranganathan, Product Manager on Microsoft Entra, to walk you through the details of phishing-resistant MFA on mobile.
We always love to hear your feedback and suggestions and look forward to hearing from you! Let us know what you think in the comments below or reach out to us on Twitter (@azuread).
Best Regards,
Alex Simons (@Alex_A_Simons)
Corporate Vice President
Microsoft Identity Division
Hello everyone,
We’re excited to share with you more about the general availability of Azure AD CBA on iOS and Android devices using certificates on hardware security key via USB and NFC.
US Cybersecurity Executive Order 14028 requires the use of phishing-resistant MFA on all device platforms. Customers can now provision certificates on a hardware security key, which can then be used for authentication with Azure AD on iOS and Android devices. Microsoft’s mobile certificate-based solution coupled with the hardware security keys is a simple, convenient, Federal Information Processing Standards (FIPS) certified phishing-resistant MFA method.
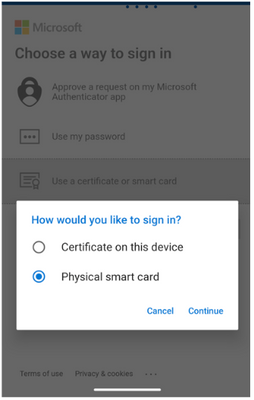
With iOS 16 and iPadOS 16.1, Apple added native support for physical smart card authentication using an NFC or a CCID class-compliant reader. You should be able to use CCID compatible smart cards against Azure AD for authentication.
All native apps, including Microsoft first-party apps using the latest Microsoft Authentication Library (MSAL), support Azure AD CBA with YubiKey on mobile devices. Azure AD CBA with YubiKey is also supported with the brokered authentication flow using latest Microsoft Authenticator (Android or iOS/iPadOS) for all apps that are not already on the latest MSAL.
Azure AD CBA on iOS mobile with YubiKey
If iOS doesn’t recognize the YubiKey, use the Yubico Authenticator App to copy YubiKey’s public certificate into the iOS keychain (the private part of the smartcard certificate never leaves the YubiKey).
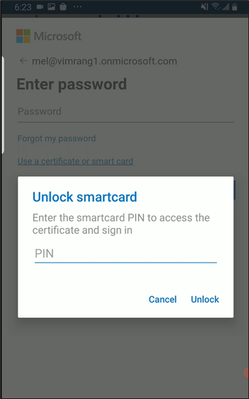
To sign in, users can select the YubiKey certificate from the certificate picker, either insert the YubiKey or tap an NFC enabled YubiKey, enter PIN via YubiKey Authenticator, and finish the authentication flow.
Azure AD CBA on Android mobile with YubiKey
Azure AD CBA support with YubiKey on Android mobile is enabled via the latest MSAL and YubiKey Authenticator app is not a requirement for Android support.
Users can initiate Azure AD CBA via certs on a physical smart card, plug in their YubiKey via USB or use NFC, pick the certificate from YubiKey, enter PIN, and get authenticated into the application.
You can also learn more about Azure AD CBA and YubiKeys here:
What’s next
Keep your feedback coming at Azure Active Directory Community! We are working diligently to add the ability to filter the certificates shown in certificate picker, as well as to integrate support for other smart card providers on Azure AD CBA on mobile.
You can learn more about Microsoft’s commitment to Executive Order 14028 here.
Thanks,
Vimala Ranganathan
Product Manager, Microsoft Entra
Follow me on LinkedIn
Learn more about Microsoft identity:
[ad_2]
Source link