[ad_1]
With Microsoft Entra ID Governance, you can effectively manage your organization’s security and identity governance needs and boost employee productivity by implementing appropriate processes and enhancing visibility. The Microsoft Entra platform empowers you with the ability to guarantee that the right people have the right access to the right resources.
We’re excited to announce the general availability of a set of capabilities in Entitlement Management available through Microsoft Entra ID Governance to help you strengthen your identity governance posture.
1. Extending the access lifecycle with your organization-specific processes and business logic
Last year we announced the public preview of entitlement management custom extensions, allowing you to extend the access lifecycle with your organization-specific processes and business logic when access is requested or about to expire. With it you can create tickets for manual access provisioning in disconnected systems, send custom notifications to additional stakeholders, or automate additional access-related configuration in your business applications such as assigning the correct sales region in Salesforce.
Earlier this year, we refreshed the public preview to enable introducing external governance, risk, and compliance (GRC) checks into the entitlement management processes. This preview refreshed enabled you to configure that an extension could pause or stop the access request and surface additional information to approvers users in My Access. Today, I’m happy to announce this capability is now generally available.
Scenario: Automate additional compliance checks as part of the access request with custom extensions
You allow your resellers to purchase goods through your reseller purchasing portal. Before someone gets access to the portal, your internal sales organization must approve and ensure that a reseller contract is in place. Until now, an approver in the sales department had to validate the contract in the contract database, what has been a manual and time-consuming process can now be automated.
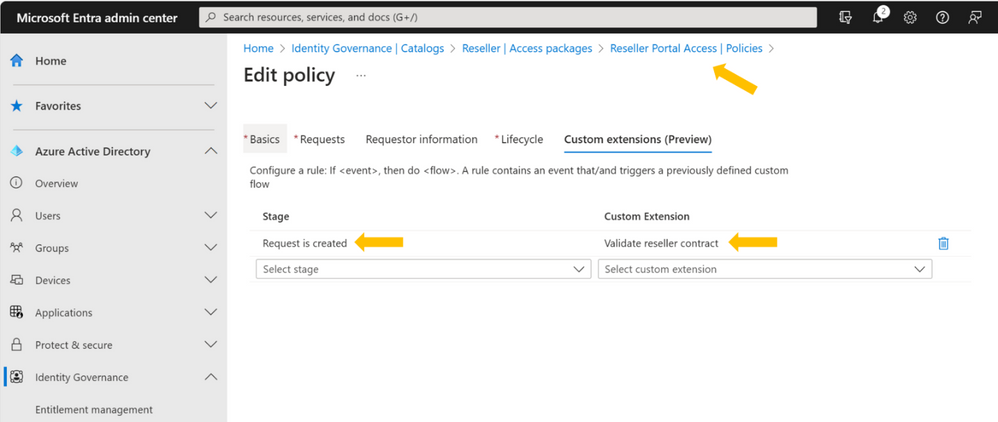
Custom extension creation
You, as an admin, can now make a custom extension available to the sales department which will validate if a reseller contract is in place. During the creation, you can specify that the extension is intended to be used during the access request workflow and that the access request should be paused until a response is received from the corresponding Logic App which will perform the contract validation.
Linking the contract validation to the access package of the reseller portal
The sales department can now extend the policy of the reseller portal access package to perform the contract validation at several stages of the access request process. In this case, the sales department opts for the validation to happen right after the access request is submitted so it’s enriched with the contract status once the request makes it to the sales representative for approval.
Approver empowered with contract status information
Going forward, when the sales representative receives an access request for the purchasing portal, the request details will be enriched with the contract information so they can quickly make a decision.
Note: The external process could have stopped the request completely if needed.
For more information about embedding your custom processes into entitlement management, see: Trigger Logic Apps with custom extensions in entitlement management.
2. Assigning access automatically to access packages instead of requiring users to request access
Last year we announced the public preview of dynamic automated access with entitlement management to automate your processes for access lifecycle management by assigning access to users based on their attributes without the need of access requests or administrative interaction. Today, I’m happy to announce that this capability is now generally available.
Scenario: Automatically assign people to Sales Team access package based on user’s department
You want employees in the Sales department to be automatically assigned to the Sales Team access package which contains sales-related projects’ resources. For that, you add a new auto-assignment policy to the Sales Team access package, that checks if the user is in the internal organization’s Sales department.
In this policy, you specify a rule for how entitlement management will select the users who need assignments. The rule is based on the attributes of the user, such as department, that typically come from your organization’s HR system, where many people with the same value of the attribute need the same access. As you want employees only (not guests) you create a rule as follows.
For more information see: Configure an automatic assignment policy for an access package in entitlement management.
3. Configuring Verified ID checks in entitlement management
In Spring 2023, we announced the public preview of an integration with the Microsoft Entra Verified ID service. This integration allows you to incorporate Verified ID checks into the access request management workflow, saving you valuable time and effort, and enhancing security by removing human errors and reducing the risk of unauthorized access.
In response to your feedback, we’ve expanded the integration to include Logic App support. With this you can ensure that the Verified ID presented by the user corresponds to the same user who is currently logged into their account and submitting the access request. This powerful combination guarantees an additional layer of confidence and accuracy in the verification process, reinforcing the integrity of your access controls.
Today, I’m happy to announce that these capabilities are now generally available.
Scenario: Require independently verified credentials to automate approvals
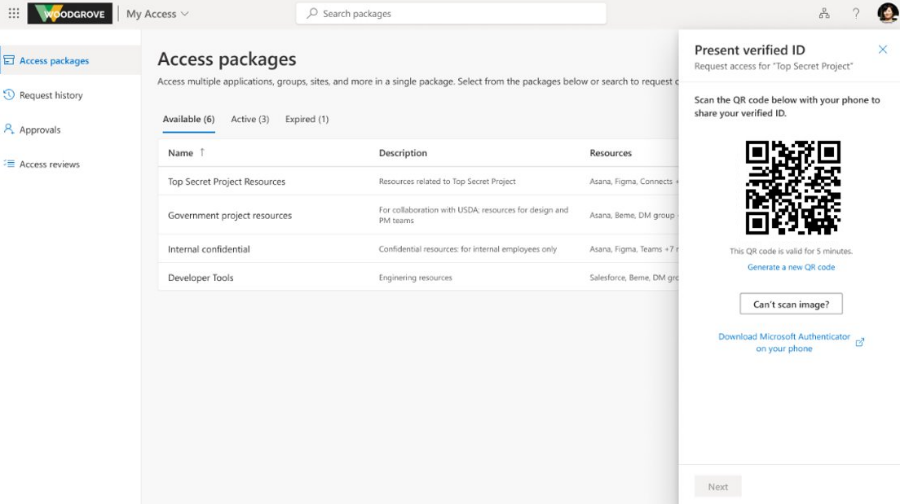
You are working with an external design agency on a project for a new customer. You require consultants to complete a Verified Vendor certification before they can be onboarded to new projects. Previously, consultants had to email a notarized copy of their certificate for manual review and approval by someone in your organization to onboard. Now, you can configure access packages with Verified ID requirements, setting a new standard for streamlined onboarding processes.
When a consultant goes to request access to the access package from the My Access portal, they will be able to select from one of two policies. Policy 1 requires approval whereas Policy 2 auto-approves the request if the user presents the required Verified ID. When the consultant selects Policy 2, all they need to do is scan the QR code on the screen. This will allow them to present the credentials from their digital wallet, and since the access package does not require approval, the consultant will receive automatic access after their credentials have been verified by the issuing agency.
For more information see: How to configure your access package with a verified ID requirement.
4. Entitlement Management support in Conditional Access
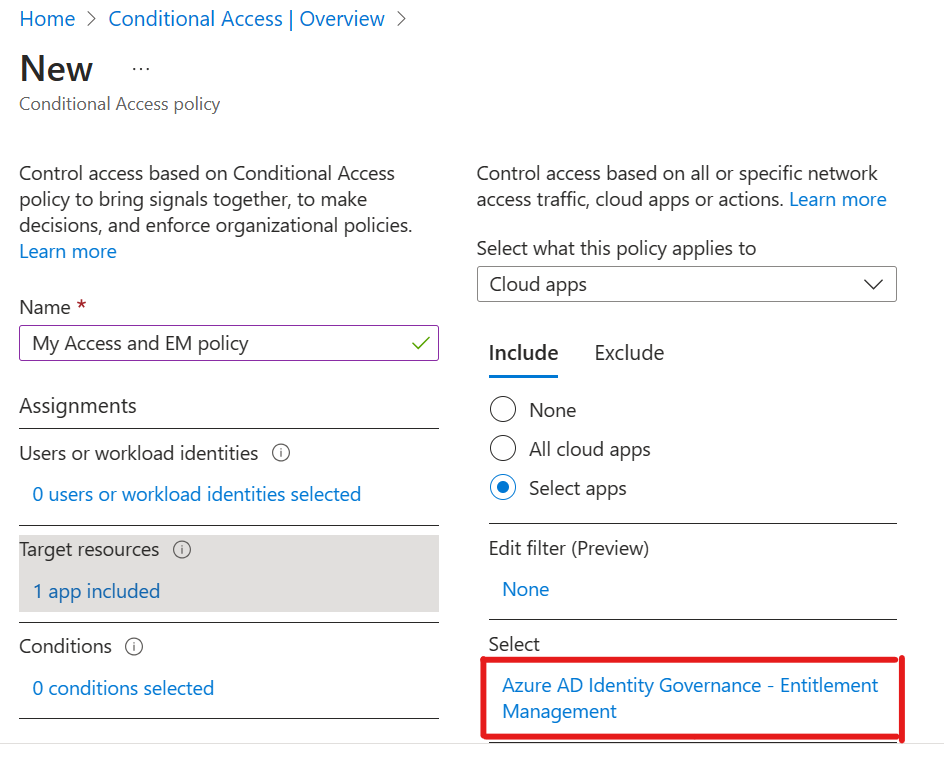
The Entitlement Management service is now targetable in the conditional access policy for inclusion or exclusion of applications. By enabling the inclusion or exclusion of Entitlement Management and/or My Access in conditional access policies, your organization is better set up for self-service onboarding and conditional access policy exception management scenarios.
For more information about conditional access see: Azure AD Conditional Access documentation. To target the Entitlement Management service, select “Azure AD Identity Governance – Entitlement Management” in the cloud apps picker.
5. My Access search improvements
As dedicated as we are to expanding Microsoft Entra’s end-to-end capabilities for admins, we’re equally committed to ensuring secure access remains a breeze for your valued end users. As part of our commitment to making the end-user experience as smooth and effortless as possible, we’ve made significant improvements to the My Access search functionality.
To enable users to find access packages more effectively, we’ve added a Resources column that shows users the resources that are part of the access package. In addition, users can now search for access packages using additional criteria, such as the access package name, description, and resources.
Give it a try
We’re excited about these new capabilities, and we’d love for you to try them out! Current Microsoft Entra ID Premium customers have two ways to use the new capabilities:
- You can set up a trial of Microsoft Entra ID Governance at https://aka.ms/EntraIDGovTrial.
- You can upgrade to Microsoft Entra ID Governance by purchasing licenses online, via our licensing partners, or directly from Microsoft if they work with a Microsoft account team.
Joseph Dadzie
Partner Director of Product Management
LinkedIn: @joedadzie
Twitter: @joe_dadzie
Learn more about Microsoft Entra:
[ad_2]
Source link