[ad_1]
Microsoft has released Security Updates (SUs) for vulnerabilities found in:
- Exchange Server 2019
- Exchange Server 2016
SUs are available for the following specific versions of Exchange Server:
The November 2023 SUs address vulnerabilities responsibly reported to Microsoft by security partners and found through Microsoft’s internal processes. Although we are not aware of any active exploits in the wild, our recommendation is to immediately install these updates to protect your environment.
These vulnerabilities affect Exchange Server. Exchange Online customers are already protected from the vulnerabilities addressed by these SUs and do not need to take any action other than updating any Exchange servers or Exchange Management tools workstations in their environment.
More details about specific CVEs can be found in the Security Update Guide (filter on Exchange Server under Product Family).
Certificate signing of PowerShell serialization payload is now enabled by default
Starting with November 2023 SU, we are enabling certificate signing of PowerShell serialization payload by default (as a reminder, this is a feature that we released in January 2023 as an optional feature at the time). Once November 2023 (or later) SU is installed on a server, certificate signing will be automatically turned on (for that specific server only).
For more information on this, please see the feature documentation.
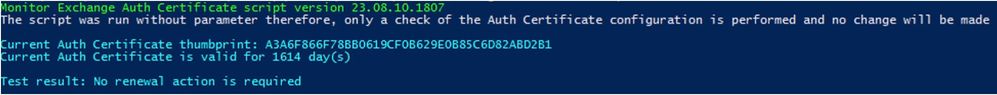
Make sure that the Exchange Auth Certificate is valid before installing the Security Update. You can use the MonitorExchangeAuthCertificate.ps1 script to perform a quick check.
The output of the MonitorExchangeAuthCertificate.ps1 script will look like this if no actions are required:
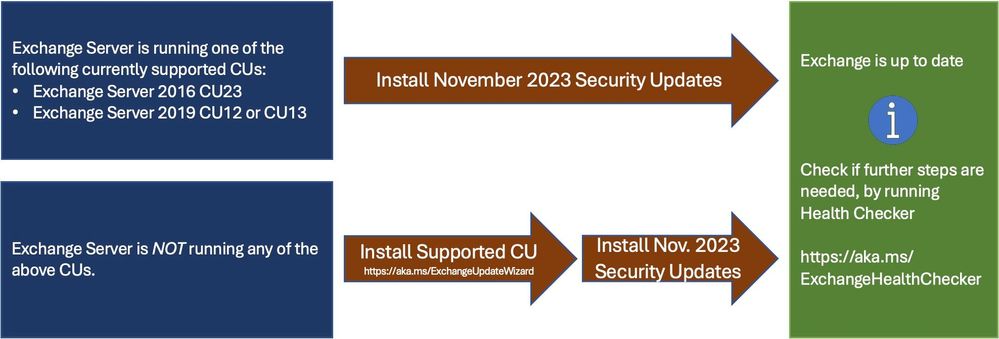
The following update paths are available:
Known issues with this release
Certain piped cmdlets (for example, Get-MailboxDatabase | Get-Mailbox) might fail on Management Tools only machines. More details and a possible workarounds can be found in the Serialized Data Signing feature documentation.
Our organization is in Hybrid mode with Exchange Online. Do we need to do anything?
Exchange Online is already protected, but this SU needs to be installed on your Exchange servers, even if they are used only for management purposes. If you change the auth certificate after installing an SU, you should re-run the Hybrid Configuration Wizard.
The last SU we installed is a few months old. Do we need to install all SUs in order to install the latest one?
SUs are cumulative. If you are running a CU supported by the SU, you do not need to install all SUs in sequential order; simply install the latest SU. Please see this blog post for more information.
Do we need to install SUs on all Exchange Servers within our organization? What about ‘Management Tools only’ machines?
Our recommendation is to install SUs on all Exchange Servers and all servers and workstations running the Exchange Management Tools to ensure compatibility between management tools clients and servers. If you are trying to update the Exchange Management Tools in the environment with no running Exchange servers, please see this.
Is it safe to disable Serialized Data Signing feature if we install November 2023 SU?
Disabling certificate signing of PowerShell serialization payloads will make your server vulnerable to known Exchange vulnerabilities and weakens protection against unknown threats. We recommend leaving this feature enabled.
Documentation may not be fully available at the time this post is published.
This post might receive future updates; they will be listed here (if available).
The Exchange Server Team
[ad_2]
Source link