
[ad_1]
Like any other service, Microsoft Entra ID is not immune to human errors, accidental deletions, or malicious attacks that could result in the loss of important data. Therefore, it is essential to have a Microsoft Entra ID recovery strategy, especially for the objects that are hard deleted when removed from the service.
Hard deletion means the object is permanently erased and cannot be restored by any means. The good news is that many objects support soft deletion, which means the object is marked as deleted in the service and moved to the recycle bin but not actually removed. The advantage of soft deletion is that the object can be recovered with its original configuration and dependencies, such as membership, assignments, and permissions, within 30 days. Therefore, it’s important to monitor and manage the soft-deleted objects in Microsoft Entra ID and decide whether to restore or permanently delete them.
Keep in mind:
- Users, Microsoft 365 Groups, (not security or distribution groups), and application registrations support soft deletion and can be restored using both the Microsoft Entra admin center and Microsoft Graph API.
- Service principals and administrative units can also be restored from the recycle bin but only via the Microsoft Graph API.
It’s important to note that while synchronized user objects also support soft deletion, they should be backed up and restored at the source (Active Directory). Re-synchronization will automatically trigger the restoration of soft-deleted objects from the recycle bin.
Tracking deletions using Entra ID audit logs
Every object deletion will trigger an event depending on the deletion type. For example, a soft-deleted user will trigger an event with the activity “Delete user” and a hard deletion will generate a “Hard Delete user” for a group that would be “Delete group” and “Hard Delete group” and so on, as shown in figure one below.
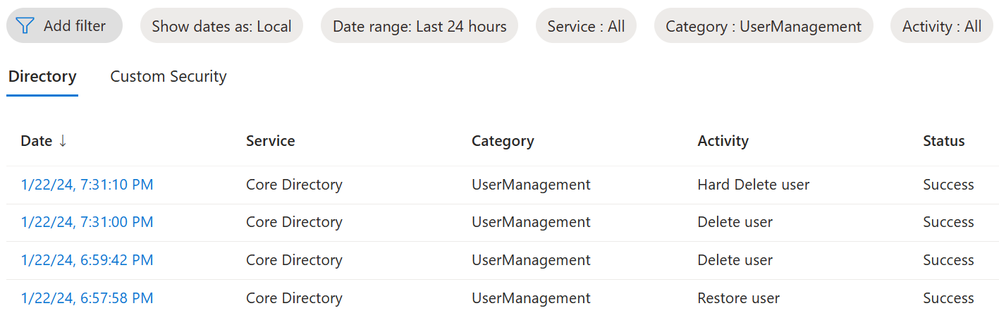
In the table below, delete, hard delete, and restore activities are listed for objects that support soft deletion, as they are seen in the audit log.
|
Deletion Activity |
Hard deletion activity |
Restore activity |
|
Delete group |
Hard Delete group |
Restore Group |
|
Delete user |
Hard Delete user |
Restore user |
|
Delete application |
Hard Delete application |
Restore application |
|
Delete administrative unit |
(hard delete not possible) |
Restore Administrative Unit |
|
Remove service principal |
Hard delete service principal |
Restore service principal |
Please also be mindful of the following when working with events in the audit log:
- Notice minor differences in activity naming, as Kusto Query Language (KQL) is case sensitive. You might have unexpected results when using strict “==” equality operators.
- For any object type that does not support soft deletion, only “Delete objectType” events will be logged, meaning a hard deletion. For example, Delete conditional access policy.
- For some object types, there’s an option to perform operations in bulk, providing a .csv file as input. For such bulk operations, there are additional events logged for start and finish, but there are still individual events for every object on the list. For example, (started (bulk) / Bulk restore deleted users – finished (bulk)).
- When a synchronized object is moved out of sync or deleted in Active Directory, then it will be soft deleted in Microsoft Entra ID with a corresponding event.
Examples of queries for monitoring deletions with Microsoft Sentinel
Microsoft Entra ID works well with Microsoft Sentinel, our cloud-native security information and event management (SIEM), platform that is built on cloud technology and offers extensive threat detection and response features. If you use Microsoft Sentinel or Log Analytics to collect and analyze Microsoft Entra ID logs, here are some KQL query examples that can help you with investigating and alerting object deletion events from Microsoft Entra ID.
Users that were soft deleted more than 25 days ago, will automatically be hard deleted soon:
AuditLogs
| where OperationName in ("Delete group", "Delete user", "Delete application", "Delete administrative unit", "Remove service principal")
| where TimeGenerated between (ago(29d) .. ago(25d))
More than 50 objects hard deleted in the past 10 minutes:
AuditLogs
| where TimeGenerated > ago(10m)
| where OperationName in ("Hard Delete group", "Hard Delete user", "Hard Delete application", "Hard delete service principal")
| summarize count()
| where count_ > 50
User deletion is followed by hard deletion:
let queryfrequency = 1h;
let queryperiod = 2h;
AuditLogs
| where TimeGenerated > ago(queryfrequency)
| where OperationName =~ "Hard Delete user"
| extend UserId = tostring(TargetResources[0].id)
| project-rename HardDeletion_TimeGenerated = TimeGenerated
| join kind=inner (
AuditLogs
| where TimeGenerated > ago(1d)
| where OperationName =~ "Delete user"
| extend UserId = tostring(TargetResources[0].id)
| project-rename SoftDeletion_TimeGenerated = TimeGenerated
) on UserId
| extend TimeDelta = HardDeletion_TimeGenerated - SoftDeletion_TimeGenerated
| where TimeDelta between (time(0s) .. queryperiod)
The queries above are provided as examples, and real detection logic and thresholds will be different for each organization. One approach could be building a Sentinel workbook to visualize data and establish deletion/restoration/hard deletion baselines that will eventually help with the creation of detections.
Reviewing deleted objects
Along with monitoring, it’s recommended to perform reviews of deleted objects. Reviews can be done regularly or prompted by some of the detection events discussed above. This can be done using the Microsoft Entra admin center, audit log-based queries, or Microsoft Graph API.
Microsoft Entra admin center / Azure Portal
The easiest way to examine “recycle bins” for deleted users, groups, or applications is by administering Microsoft Entra ID in the Microsoft Entra admin center or Azure portal. However, this method has limitations, as the interface varies slightly depending on the object type, and for administrative units and service principals, there is no graphical experience.
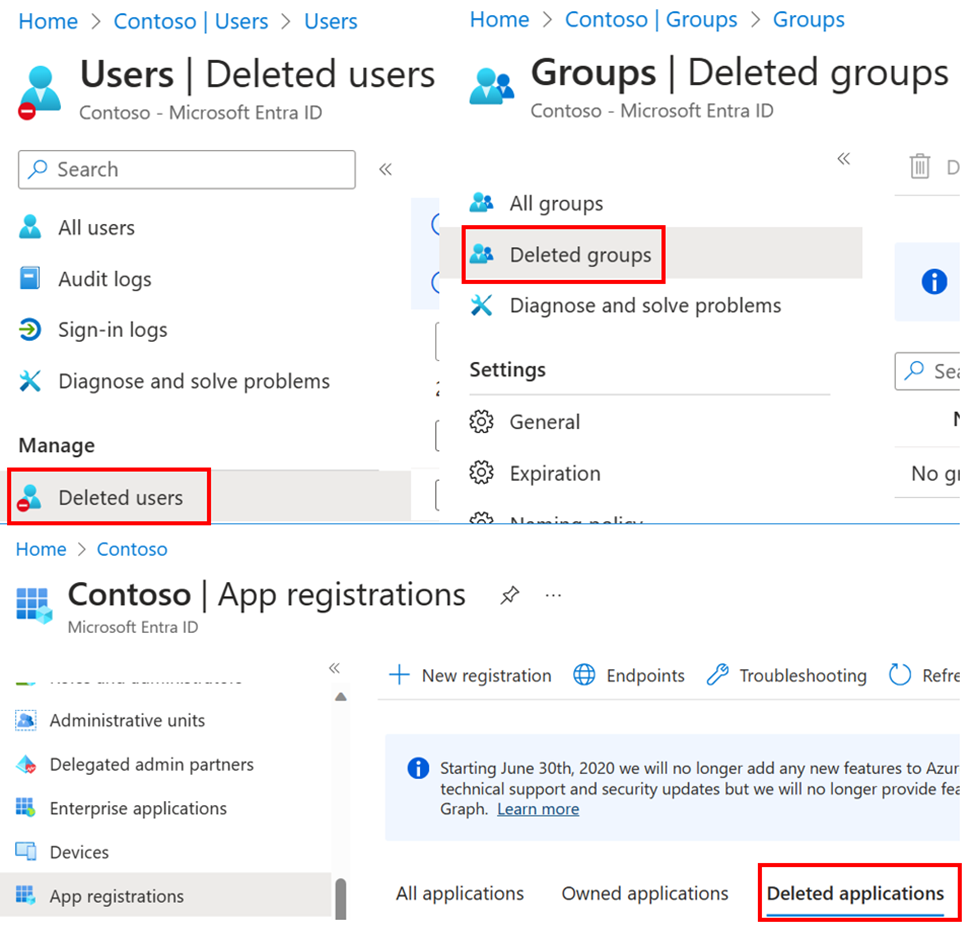
Audit logs
Audit logs can also be used to generate a soft deleted items report that shows all the deleted objects for the last 30 days, excluding those that have already been restored or hard deleted.
Here’s a sample query for User objects:
let Users = AuditLogs
| where TimeGenerated > ago(30d)
| where Category == "UserManagement";
Users
| where OperationName =~ "Delete user"
| extend UserId = tostring(TargetResources[0].id)
| join kind=anti (
Users
| where OperationName =~ "Hard Delete user"
| extend UserId = tostring(TargetResources[0].id)
) on UserId
| join kind=anti (
Users
| where OperationName =~ "Restore user"
| extend UserId = tostring(TargetResources[0].id)
) on UserId
While audit logs is not a completely reliable method, they might be useful while building workbooks or reports.
Microsoft Graph API
By calling the Microsoft Graph API using PowerShell and the Microsoft.Graph module, you can get a list of all the objects currently in the recycle bin. The sample code below will generate a single report for all the object types, and when needed, it can be easily adjusted to perform restores using the Restore-MgBetaDirectoryDeletedItem cmdlet.
Install-Module Microsoft.Graph
Connect-MgGraph
$deletedUsers = Get-MgBetaDirectoryDeletedItemAsUser
$deletedServicePrincipals = Get-MgBetaDirectoryDeletedItemAsServicePrincipal
$deletedGroups = Get-MgBetaDirectoryDeletedItemAsGroup
$deletedApplications = Get-MgBetaDirectoryDeletedItemAsApplication
$deletedAUs = Get-MgBetaDirectoryDeletedItemAsAdministrativeUnit
$deletedItems = @()
$deletedItems += $deletedGroups
$deletedItems += $deletedApplications
$deletedItems += $deletedUsers
$deletedItems += $deletedServicePrincipals
$deletedItems += $deletedAUs
if ($deletedItems.Count -eq 0) {
Write-Host "No soft deleted objects found." -ForegroundColor Green
}
else {
Write-Host "Soft deleted Users: $($deletedUsers.Count)" -ForegroundColor Green
Write-Host "Soft deleted Service Principals: $($deletedServicePrincipals.Count)" -ForegroundColor Green
Write-Host "Soft deleted M365 Groups: $($deletedGroups.Count)" -ForegroundColor Green
Write-Host "Soft deleted Applications: $($deletedApplications.Count)" -ForegroundColor Green
Write-Host "Soft deleted Administrative Units: $($deletedAUs.Count)" -ForegroundColor Green
$report = foreach ($item in $deletedItems) {
$deletedDate = Get-Date($item.DeletedDateTime)
$now = Get-Date
$hardDeletedInDays = 30 - ($now - $deletedDate).Days
[PSCustomObject]@{
Id = $item.Id
UserPrincipalName = $item.UserPrincipalName
DisplayName = $item.DisplayName
Deleted = $deletedDate
HardDeletionIn = $hardDeletedInDays
}
}
$report | Sort-Object 'Display Name' | Select-Object Id, DisplayName, Deleted, HardDeletionIn | Format-Table
$report | Export-Csv -Path "C:tempsoftDeletedObjects.csv" -Encoding UTF8 -NoTypeInformation
}
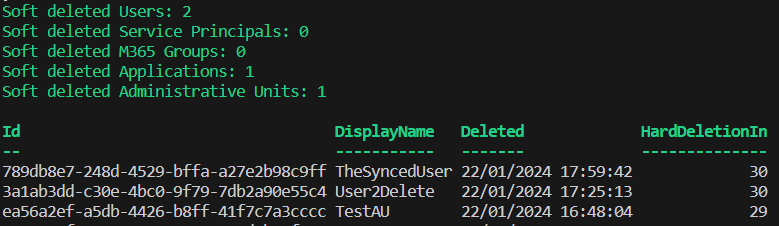
This script will generate a .csv file and provide a summary output:
Conclusion
Tracking deletions in Microsoft Entra ID can be useful for several reasons. These include identifying and recovering any objects that were accidentally or maliciously deleted, to monitoring and auditing changes in the directory and ensuring compliance with security policies and regulations, and to optimizing license usage by removing any unnecessary or obsolete objects. Make sure to enable monitoring of deletions using queries above as a starting point and perform regular reviews of deleted items to be able to catch any potentially unwanted deletions while objects are still available for restoration.
Alexander Zagranichnov
Learn more about Microsoft Entra:
[ad_2]
Source link




