[ad_1]
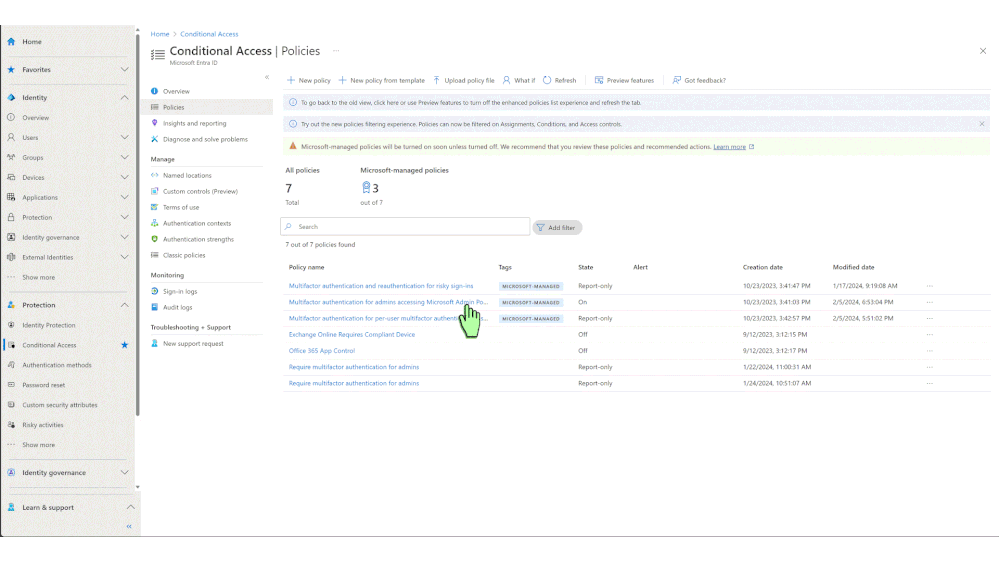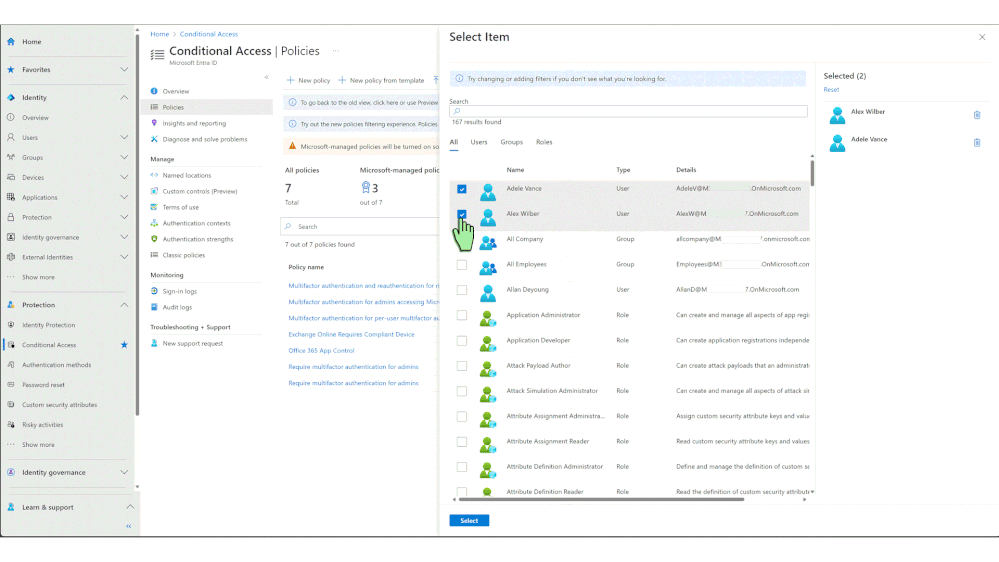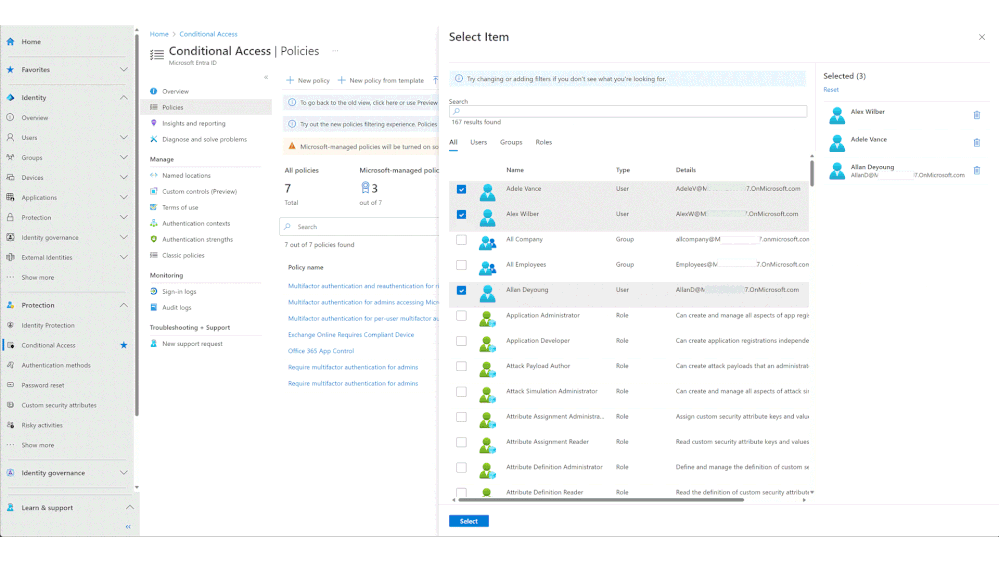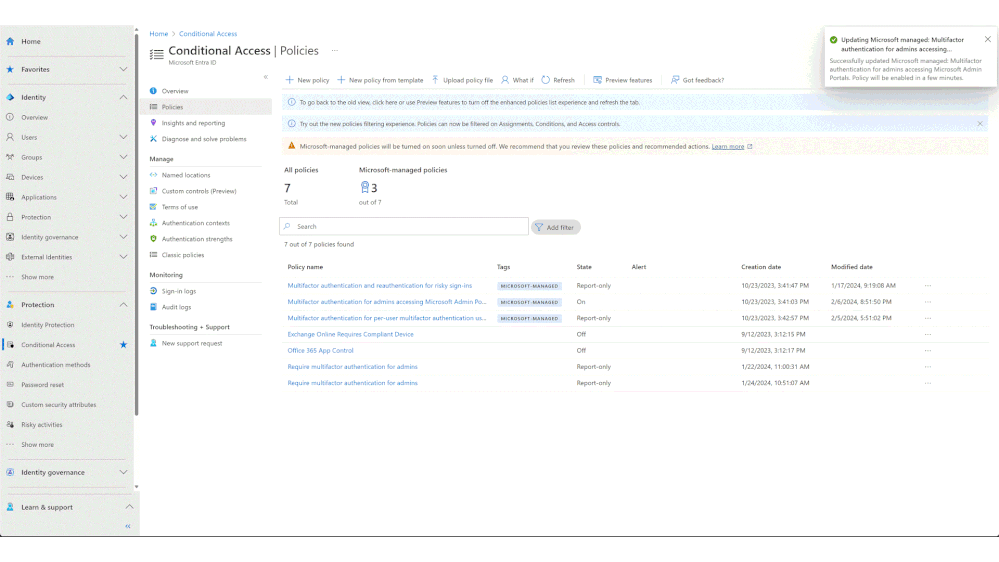
As part of our Secure Future Initiative, we announced Microsoft-managed Conditional Access policies in November 2023. These policies are designed to help you secure your organization’s resources and data based on your usage patterns, risk factors, and existing policy configuration, all while minimizing your effort. Our top recommendation for improving your identity secure posture is enabling multifactor authentication (MFA), which reduces the risk of compromise by 99.2%. This is why our first three policies are all related to MFA for different scenarios.
Since we announced Microsoft-managed Conditional Access policies, we’ve rolled out these policies to more than 500,000 tenants in report-only mode. In this mode, the policies don’t impact access but log the results of policy evaluation. This allows administrators to assess the impact before enforcing these policies. Thanks to proactive actions taken by administrators to enable or customize these policies, over 900,000 users are now protected with MFA.
We’ve been actively listening to your feedback. Customers shared that Microsoft-managed policies impact the number of Conditional Access policies that organizations can create. We’ve addressed this by making a significant change: Microsoft-managed policies will no longer count towards the Conditional Access policy limit. Another adjustment relates to existing Conditional Access policies. If you already have a policy in the “On” state that meets or exceeds the requirements set by the Microsoft-managed policy, the latter will not be automatically enforced in your tenant.
Initially, we communicated that these policies would be automatically enabled 90 days after creation. However, based on customer feedback, we recognize that some customers need additional time to prepare for these policies to be enforced. As a result, we have extended the time frame before enforcing the policies for this initial set of policies. For these three policies, you will have more than 90 days to review and customize (or disable) your Microsoft-managed Conditional Access policies before they are automatically enforced. Rest assured, you’ll receive an email and a Message Center notification providing a 28-day advance notification before the policies are enforced in your tenant.
Call to Action
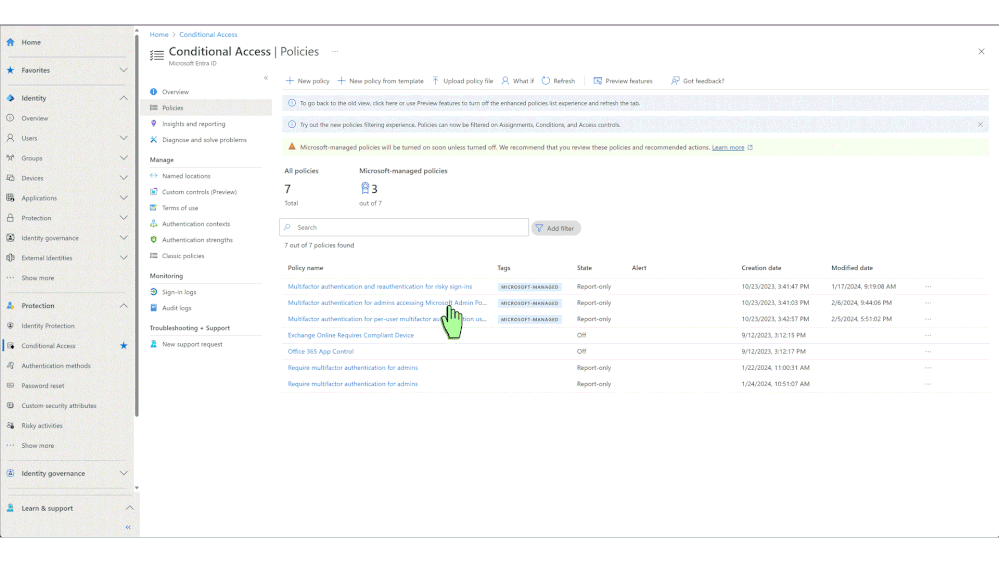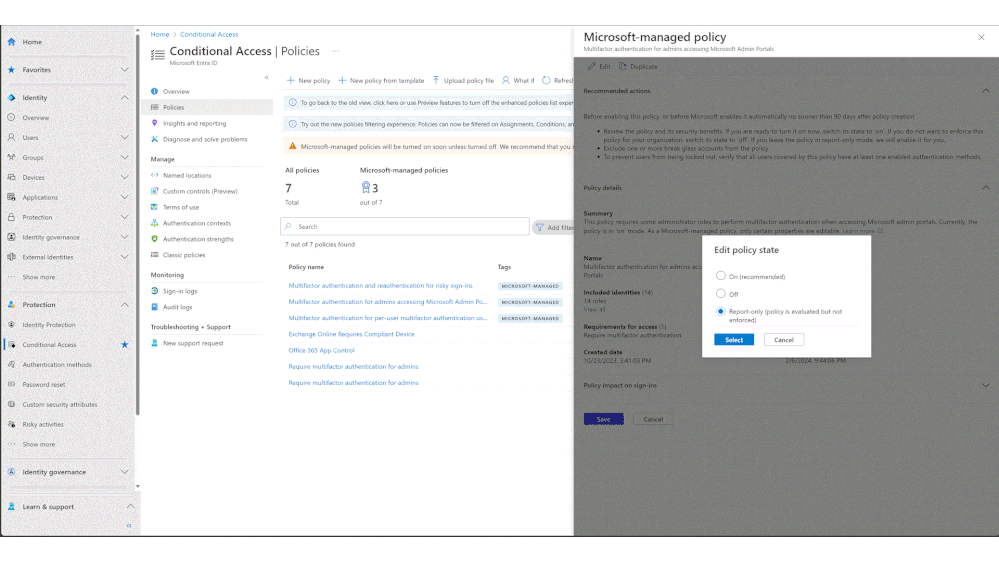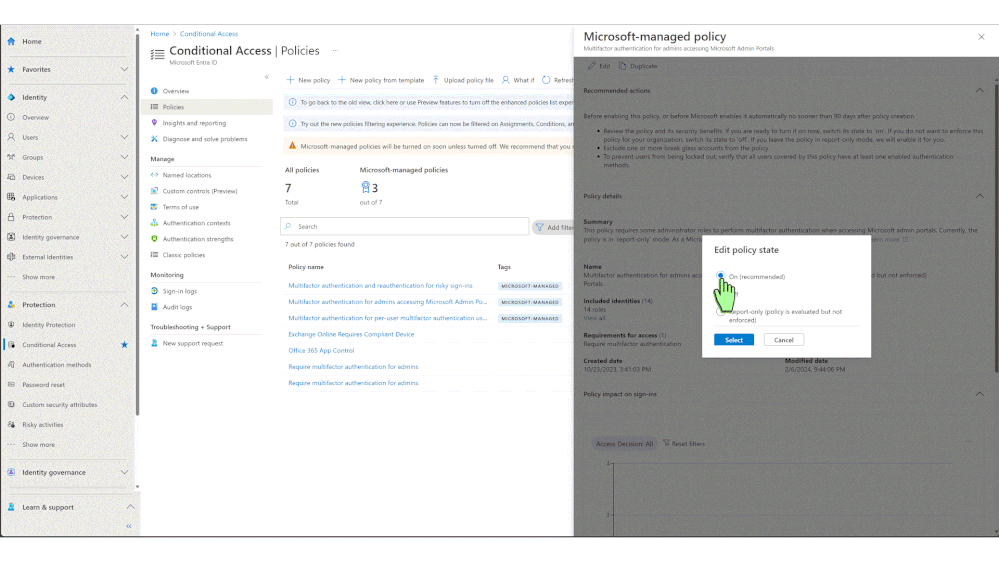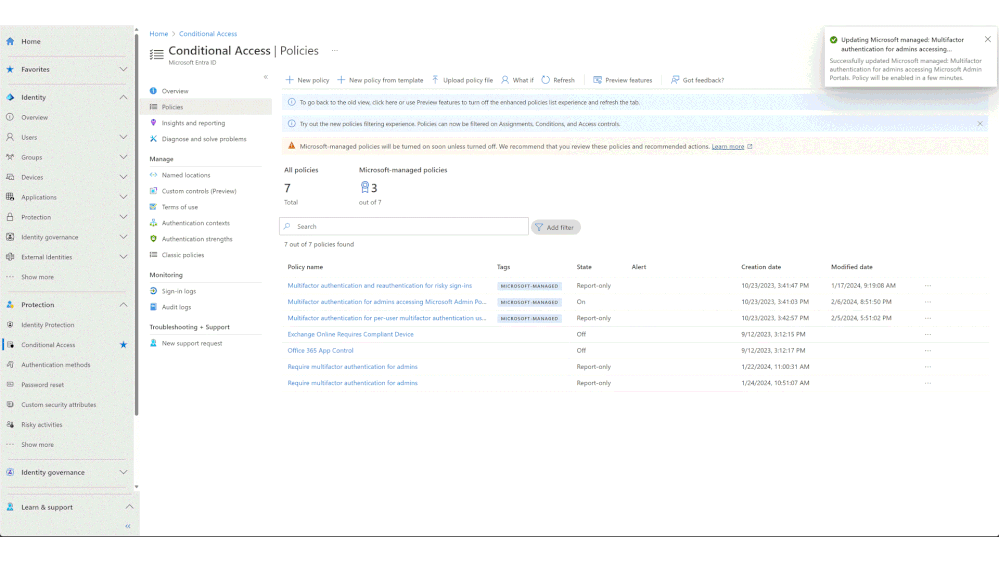
- Review these policies in the Conditional Access policies blade.
- Add customizations such as excluding emergency accounts and service accounts.
- Once ready, the policies can be moved to the ON state.
For additional customization needs, you can duplicate these policies and make further adjustments.
To learn more about how to secure your resources, visit our Microsoft-managed policies documentation.
Nitika Gupta
Principal Group Product Manager, Microsoft
Learn more about Microsoft Entra:
[ad_2]
Source link