[ad_1]
I noticed a section on the Features in development page that talks about a change coming on April 1st, which is not very far away (and an interesting place to put “we’re going to break things” notices):
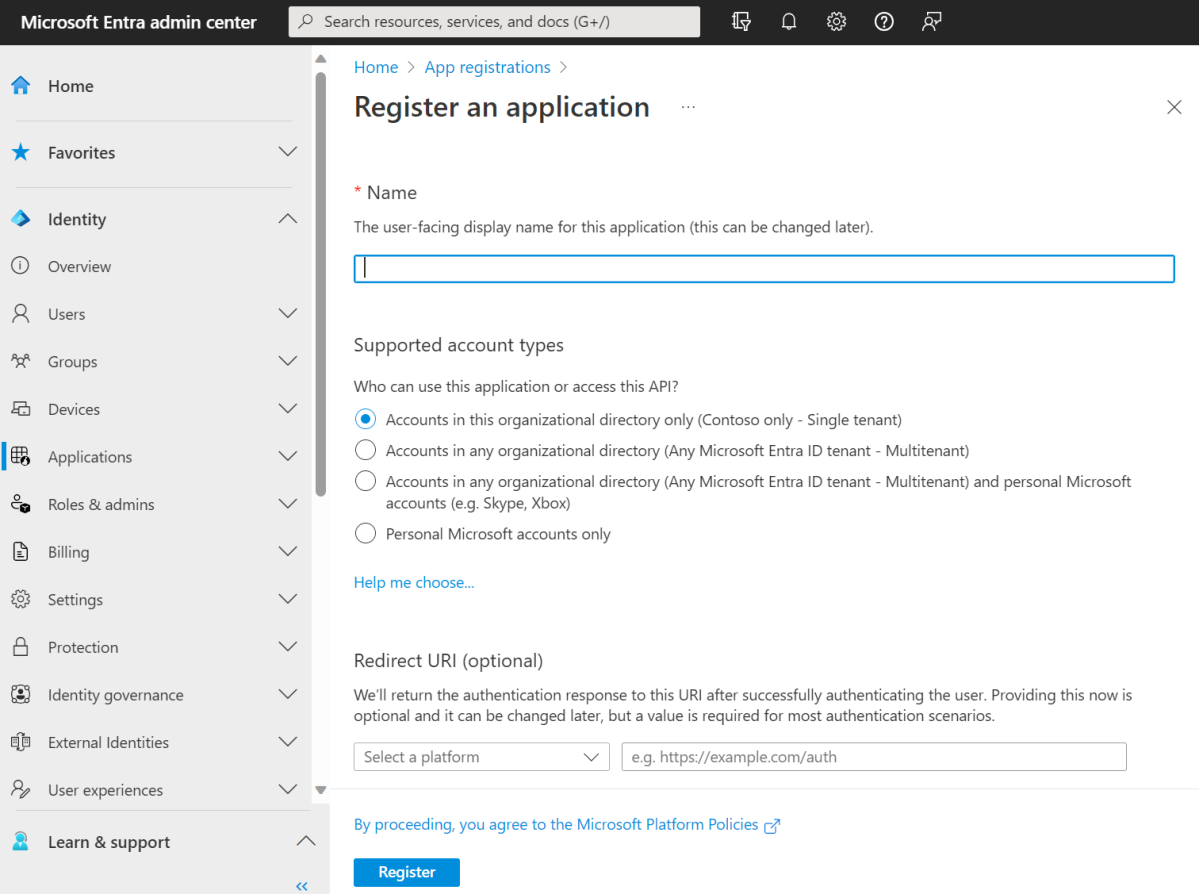
If you’re using the Intune PowerShell application ID (d1ddf0e4-d672-4dae-b554-9d5bdfd93547), you’ll need to update your scripts with a Microsoft Entra ID registered application ID to prevent your scripts from breaking.
There’s another note on the separate Intune code samples page saying the same thing, with a little more detail (but not much):
Before April 1, 2024, update your PowerShell scripts by:
And of course there is some chatter on Twitter about it:
And of course there are other blogs about it too:
OK great, if there are some scripts that you developed yourself you’ll need to make some changes. But what about other scripts that are out in the wild? Not surprisingly, there appear to be a bunch of them that haven’t been changed.
Why are they making this change? Well, I’m sure at the heart of it, it’s related to security. Imagine having an app ID that, when combined with a valid Azure AD/Entra ID user token, will get access to everything that you have granted to that app over time from running various sample scripts that use it. By forcing you to create your own app ID, it won’t be well-known, and with any luck you’ll secure it appropriately so that only needed people can use it. (I could see the same thing coming for the app ID used with Graph Explorer, for the same reason.)
A quick search on GitHub turns up a lot of references to this in various PowerShell scripts, as well as a few C# projects. And there are a number of published scripts and modules on the PowerShell Gallery that will also have issues. The most popular ones that I checked looked fine, but I’m sure we’ll hear from many people in the coming weeks who find those that aren’t fine.
[ad_2]
Source link




