[ad_1]
Managing the myriad settings and resources within your tenant can be daunting. In an era of escalating security risks and an unprecedented global threat landscape, organizations seek trusted guidance to enhance their security posture That’s why we introduced Microsoft Entra Recommendations to diligently monitor your tenant’s status, ensuring it remains secure and healthy. Moreover, they empower you to extract maximum value from the features offered by Microsoft Entra ID. Since the launch of Microsoft Entra recommendations, thousands of customers have adopted these recommendations and resolved millions of resources.
Today, we’re thrilled to announce the upcoming general availability of four recommendations, and another three recommendations in public preview. We’re also excited to share new updates on Identity secure score. These recommendations cover a wide spectrum, including credentials, application health, and broader security settings—equipping you to safeguard your digital estate effectively.
Presenting new and upcoming recommendations- Learn from our best practices.
The following list of new and upcoming recommendations help improve the health and security of your applications:
- Remove unused credentials from applications: An application credential is used to get a token that grants access to a resource or another service. If an application credential is compromised, it could be used to access sensitive resources or allow a bad actor to move latterly, depending on the access granted to the application. Removing credentials not actively used by applications improves security posture and promotes application hygiene. It reduces the risk of application compromise and improves the security posture of the application by reducing the attack surface for credential misuse by discovery.
- Renew expiring service principal credentials: Renewing the service principal credential(s) before expiration ensures the application continues to function and reduces the possibility of downtime due to an expired credential.
- Renew expiring application credentials: Renewing the app credential(s) before its expiration ensures the application continues to function and reduces the possibility of downtime due to an expired credential.
- Remove unused applications: Removing unused applications improves the security posture and promotes good application hygiene. It reduces the risk of application compromise by someone discovering an unused application and misusing it. Depending on the permissions granted to the application and the resources that it exposes, an application compromise could expose sensitive data in an organization.
- Migrate applications from the retiring Azure AD Graph APIs to Microsoft Graph: The Azure AD Graph service (graph.windows.net) was announced as deprecated in 2020 and is in a retirement cycle. It’ is important that applications in your tenant, and applications supplied by vendors that are consented in your tenant (service principals), are updated to use Microsoft Graph APIs as soon as possible. This recommendation reports applications that have recently used Azure AD Graph APIs, along with more details about which Azure AD Graph APIs the applications are using.
- Migrate Service Principals from the retiring Azure AD Graph APIs to Microsoft Graph: The Azure AD Graph service (graph.windows.net) was announced as deprecated in 2020 and is in a retirement cycle. It’ is important that service principals in your tenant, and service principals for applications supplied by vendors that are consented in your tenant, are updated to use Microsoft Graph APIs as soon as possible. This recommendation reports service principals that have recently used Azure AD Graph APIs, along with more details about which Azure AD Graph APIs the service principals are using.
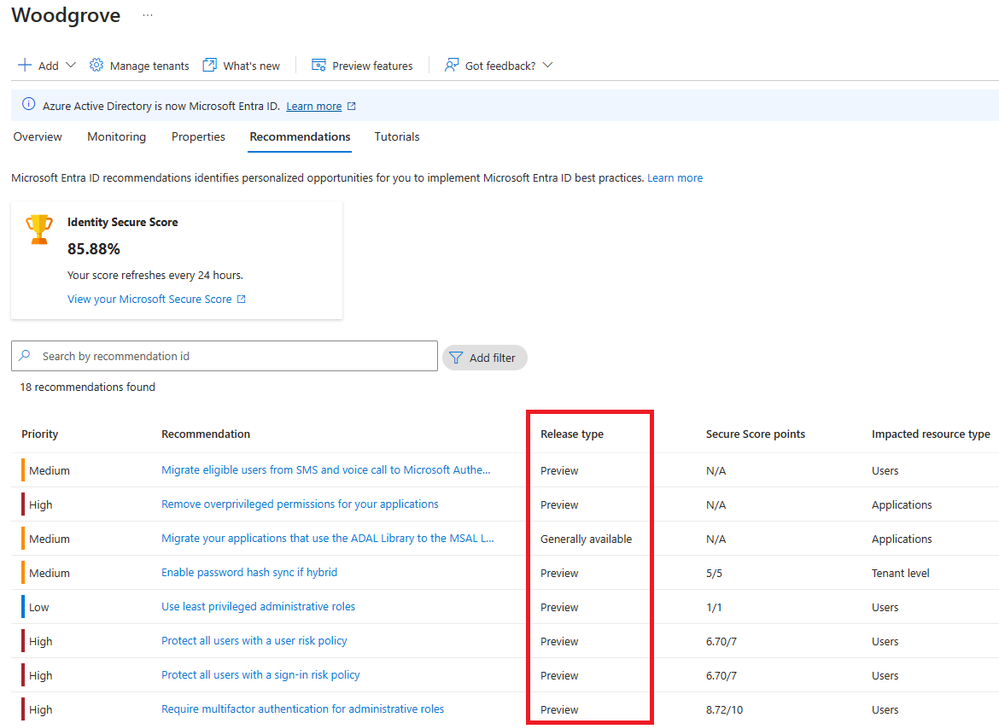
You can find these recommendations that are in general availability on the Microsoft Entra recommendations portal by looking for “Generally Available” under the column titled “Release Type” as shown below.
Changes to Secure Score – Your security analytics tool to enhance security.
We’re happy to announce some new developments in Identity Secure Score which functions as an indicator for how aligned you are with Microsoft’s recommendations for security. Each improvement action in Identity Secure Score is customized to your configuration and you can easily see the security impact of your changes. We have an upcoming Secure Score recommendation in public preview to help you protect your organization from Insider risk. Please see the details below:
- Protect your tenant with Insider Risk policy: Implementing a Conditional Access policy that blocks access to resources for high-risk internal users is of high priority due to its critical role in proactively enhancing security, mitigating insider threats, and safeguarding sensitive data in real-time. Learn more about this feature here.
In addition to the new Secure Score recommendation, we have several other recommendations related to Secure Score. We strongly advise you to check your security-related recommendations if you haven’t done so yet. Please see below for the current list of recommendations for secure score:
- Enable password hash sync if hybrid: Password hash synchronization is one of the sign-in methods used to accomplish hybrid identity. Microsoft Entra Connect synchronizes a hash of the hash of a user’s password from an on-premises Microsoft Entra Connect instance to a cloud-based Microsoft Entra Connect cloud sync instance. Password hash synchronization helps by reducing the number of passwords your users need to maintain to just one. Enabling password hash synchronization also allows for leaked credential reporting.
- Protect all users with a user risk policy: With the user risk policy turned on, Microsoft Entra ID detects the probability that a user account has been compromised. As an administrator, you can configure a user risk Conditional Access policy to automatically respond to a specific user risk level.
- Protect all users with a sign-in risk policy: Turning on the sign-in risk policy ensures that suspicious sign-ins are challenged for multifactor authentication (MFA).
- Use least privileged administrative roles: Ensure that your administrators can accomplish their work with the least amount of privilege assigned to their account. Assigning users roles like Password Administrator or Exchange Online Administrator, instead of Global Administrator, reduces the likelihood of a privileged account being breached.
- Require multifactor authentication for administrative roles: Requiring multifactor authentication (MFA) for administrative roles makes it harder for attackers to access accounts. Administrative roles have higher permissions than typical users. If any of those accounts are compromised, your entire organization is exposed.
- Ensure all users can complete MFA: Help protect devices and data that are accessible to these users with MFA. Adding more authentication methods like the Microsoft Authenticator app or a phone number, increases the level of protection if another factor is compromised.
- Enable policy to block legacy authentication: Today, most compromising sign-in attempts come from legacy authentication. Older office clients such as Office 2010 don’t support modern authentication and use legacy protocols such as IMAP, SMTP, and POP3. Legacy authentication doesn’t support MFA. Even if an MFA policy is configured in your environment, bad actors can bypass these enforcements through legacy protocols. We recommend enabling policy to block legacy authentication.
- Designate more than one Global Admin: Having more than one Global Administrator helps if you’re unable to fulfill the needs or obligations of your organization. It’s important to have a delegate or an emergency access account that someone from your team can access if necessary. It also allows admins the ability to monitor each other for signs of a breach.
- Do not expire passwords: Research has found that when periodic password resets are enforced, passwords become less secure. Users tend to pick a weaker password and vary it slightly for each reset. If a user creates a strong password (long, complex, and without any pragmatic words present), it should remain as strong in the future as it is today. It is Microsoft’s official security position to not expire passwords periodically without a specific reason and recommends that cloud-only tenants set the password policy to never expire.
- Enable self-service password reset: With self-service password reset in Microsoft Entra ID, users no longer need to engage helpdesk to reset passwords. This feature works well with Microsoft Entra dynamically banned passwords, which prevents easily guessable passwords from being used.
- Do not allow users to grant consent to unreliable applications: To reduce the risk of malicious applications attempting to trick users into granting them access to your organization’s data, we recommend that you allow user consent only for applications that have been published by a verified publisher.
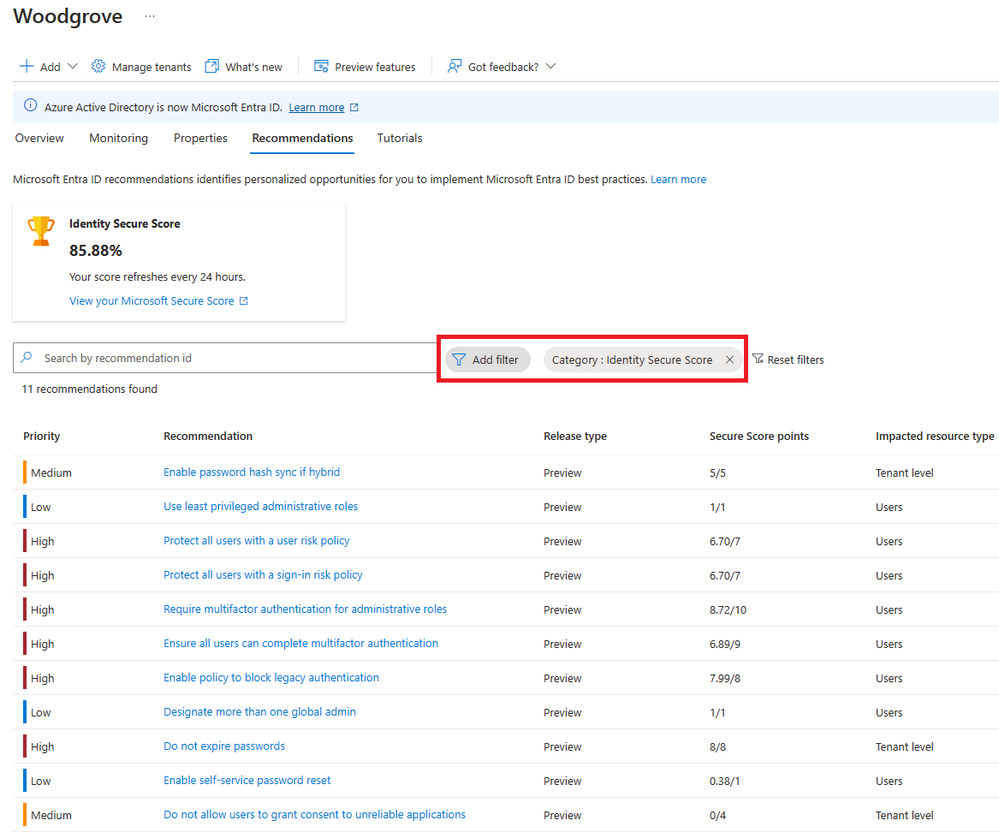
You can find your Secure Score recommendations on Microsoft Entra recommendations portal by adding a filter on “Category” and selecting “Identity Secure Score” as shown below.
We look forward to you leveraging these learnings and best practices for your organization. We’re constantly innovating and improving customers’ experience to bring the right recommendations to the right people. In our future release, we’ll introduce new capabilities like email notifications to create awareness of new recommendations and delegation capabilities to other roles, and provide more actionable recommendations so you can quickly resolve them to secure your organization.
Shobhit Sahay
Learn more about Microsoft Entra:
[ad_2]
Source link