[ad_1]
Microsoft customers around the globe have responded to COVID-19 by moving their office employees to remote work. With more people working from home, identity-driven security solutions are required to help safeguard company resources. Nathan Lasnoski, Chief Technology Officer at Concurrency, has worked with many of our customers to implement a Zero Trust security strategy that puts identity protection at the center. In this “Voice of the Partner” blog, he shares how this approach has benefited global marine manufacturer, Brunswick Corporation.
Supporting Modern Work with Zero Trust
By Nathan Lasnoski, Chief Technology Officer, Concurrency
Concurrency is a business and technology professional services firm driving technology innovation and organizational change management. Today, like most organizations, our clients are confronting challenges associated with migrating a significant percentage of employees to remote work in response to COVID-19. This has been tough for everyone, but I’ve found that organizations that adopt a Zero Trust security model have been able to move to remote work faster and more securely.
Brunswick Corporation is a great example of a client whose investments in Zero Trust and identity modernization have made the transition to remote work smoother. Brunswick’s brands manufacture boats and marine propulsion systems. It also owns Freedom Boat Club, the world’s largest social club that allows people to get the benefits of a boat without owning one.
We got involved with Brunswick about 18 months ago. The organization needed a partner to help digitally transform its business in a way that enhances security. When COVID-19 began to spread, these efforts also made it easier and more secure for Brunswick employees to work from home. In this post, I’ll outline a few of the core tenets of Zero Trust that guided our work.
Zero Trust is the baseline for modern work
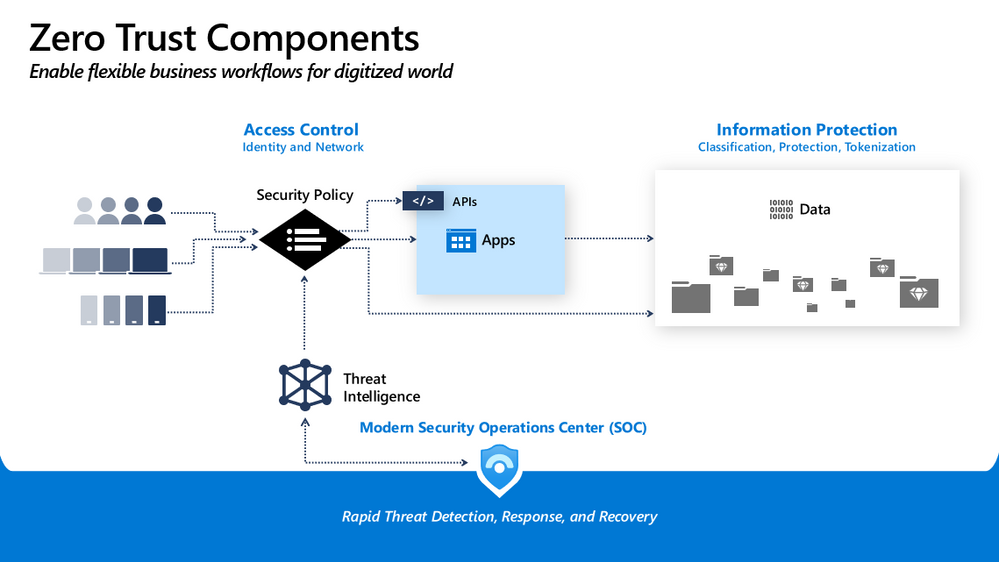
Before I dive in, I should define Zero Trust. In the traditional network security model, IT creates a wall to keep out the bad actors, while allowing largely free communications inside. This approach was mostly successful when apps were hosted almost exclusively inside the network, but organizations have moved more business assets to the cloud. Today, people are no longer tethered to a company-provided desktop in the physical workplace. They access work data from any device and any network. Employees aren’t the only users. Partners and contractors also need access. It’s no longer possible to automatically trust traffic inside the network. In a Zero Trust model, users and devices, both inside and outside the corporate network, are verified in real time before gaining access.
It starts with identity
A key component of Brunswick’s cloud journey was identity modernization. As the company shifted to a Zero Trust security model, they needed tools to verify users who wanted to use its apps and systems—whether they were inside the network accessing on-premises apps or outside the network accessing software-as-a-service (SaaS) apps.
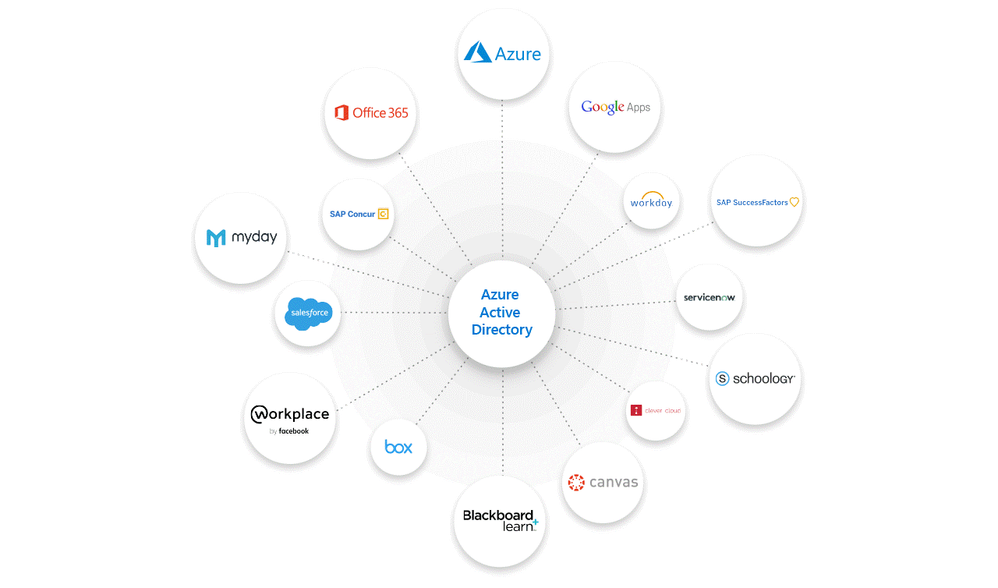
Brunswick deployed Azure Active Directory (Azure AD) to manage identities and access. Azure AD integrates with Office 365 and thousands of non-Microsoft software-as-a-service (SaaS) apps, such as Workday, SAP, or Adobe. With Azure AD App Proxy, Brunswick can also connect on-premises apps to Azure AD. Unifying credentials into one identity lets employees sign in once using single sign-on (SSO) to use all their apps—whether Office 365, non-Microsoft, or on-premises.
With Azure AD, Brunswick can apply universal security controls, like multi-factor authentication (MFA), to all their connected apps. MFA requires at least two authentication factors at every sign-in, reducing the likelihood that an account will be compromised.
Network Micro-segmentation
The Zero Trust approach is premised on the idea that you should “assume breach.” That’s why it’s important not to automatically trust access requests, even those that originate on the corporate network. If organizations make it easy for resources to talk to each other, they also make it easy for an attacker to move around.
When Brunswick and Concurrency migrated the Brunswick’s data center to Microsoft Azure, we implemented micro-segmentation. We isolated workloads from each other and applied security policies to each segment. In this model, systems and devices aren’t automatically connected, making it difficult for an attacker to move laterally. As Alan Mitchell, CISO of Brunswick Corporation, explained in a recent interview, “Think of micro-segmentation like a battleship with compartments that I can shut off. If water flows in, it can be limited to a specific area, and we can respond, versus worrying that the whole ship is sinking.”
Evaluate and enforce device compliance
Devices are the last frontier in a Zero Trust model, because that’s where the data lives after people successfully access it. When employees use personal or unmanaged devices for work, it becomes more challenging to make sure the devices are healthy and safe. Every user applies different security controls to their devices, downloads a variety of mobile apps, and may or may not apply security updates recommended by the manufacturer. To apply Zero Trust principles to any Android, iOS, macOS, and Windows devices requesting access to the network, Brunswick uses Microsoft Endpoint Manager to ensure that only devices that are compliant with its security standards can access corporate resources. To further protect corporate data and intellectual property, data can only be accessed using trusted apps and shared with other trusted apps.
Protect data
One of the reasons that security is so challenging is that threats continually evolve. It’s impossible to secure every potential endpoint. To reduce the risk that sensitive information will be leaked, organizations protect the data itself—both at rest and in flight. Brunswick deployed Azure Information Protection and Microsoft Data Loss Prevention to classify and safeguard privileged information. Alan said, “It’s difficult to keep up with every threat vector, so we put policies, controls, and data labeling in place to make it harder for someone to copy sensitive information to a USB drive or a cloud storage device.”
Apply Conditional Access policies
The reason that Brunswick selected Microsoft 365 security solutions is because the products are integrated and work together. This makes detecting and responding to incidents more effective. It also allows the company to apply Zero Trust in a consistent approach. Azure AD Conditional Access is a very important tool. With Azure AD, Microsoft Endpoint Manager, Azure Information Protection, and other Microsoft 365 solutions, Brunswick is able to create granular Conditional Access policies to control access based on context. These policies can be especially useful for a remote workforce. When users try to sign in, Azure AD Conditional Access policies use Microsoft Endpoint Manager to check the health of their device, their location, which application they are trying to access, and other risk factors. If the access request doesn’t meet Brunswick policies, Azure AD can automatically block access or force a password reset, among other actions.
COVID-19 has forced many organizations to quickly deploy new technology to enable secure business continuity, but the virus has only accelerated existing trends. The office isn’t going away, but at Concurrency, we believe that as organizations move more of their infrastructure to the cloud so they can focus on product innovation, employees will take advantage of the flexibility of working from anywhere. A Zero Trust security strategy makes both possible.
Learn more
A Zero Trust security strategy can help you improve security for your remote workforce. By verifying identities and devices with Azure AD Conditional Access policies, you can reduce the risk of compromise.
Read more about Microsoft’s approach to Zero Trust
Source link