
[ad_1]
Howdy Folks,
Our team has been working hard to make passwords a thing of the past. Last year was a breakthrough year, and the start of the movement to passwordless sign in. Today we’re announcing our passwordless solution is now generally available!
This is a major milestone in Microsoft’s strategy to encourage all our users and organizations to go passwordless! Now organizations can rollout passwordless authentication across their hybrid environments at scale. Users get a familiar, simple to use authentication experience that offers industry best security and works across an increasingly broad set of devices and services.
Thanks in large part to the feedback we’ve received since we launched public preview in July 2019, we added a fleet of new features to improve the management and usability of these credentials, including Authentication methods management, step-up authentication, and passwordless APIs. One of the most impactful updates is the new Temporary Access Pass, now in public preview. This time limited passcode ties the onboarding and recovery story of passwordless together for an end-to-end passwordless experience from day one.
Authentication methods management
Authentication methods policies form the foundation of our passwordless story. These policies provide IT admins with more granular control of authentication methods usage within their organizations. In this space, you’ll continue to see more credentials added to the Authentication Methods blade both in the Azure Portal and via Microsoft Graph, to access and manage authentication methods policies and user credentials for your organization. We’ve merged management of credentials in the Microsoft Authenticator app so that an admin can set one policy for both passwordless and standard push multi-factor authentication.
In the portal, you also can now see and delete passwordless methods on the User blade, for example revoking a FIDO2 Security Key registration if the user has lost it. Policies related to passwordless credentials are now in MSGraph V1. We’ve introduced a new scoped role specifically for authentication methods policy management, aptly named Authentication Policy Administrator, in addition to the Authentication administrator.
Figure 1: Authentication methods management in Azure Portal
Figure 2: Merged Microsoft Authenticator policy management configuration
Figure 3: A user’s registered credentials in Azure Portal
Figure 4: A user’s authentication methods as displayed in Graph Explorer
Improved user experiences
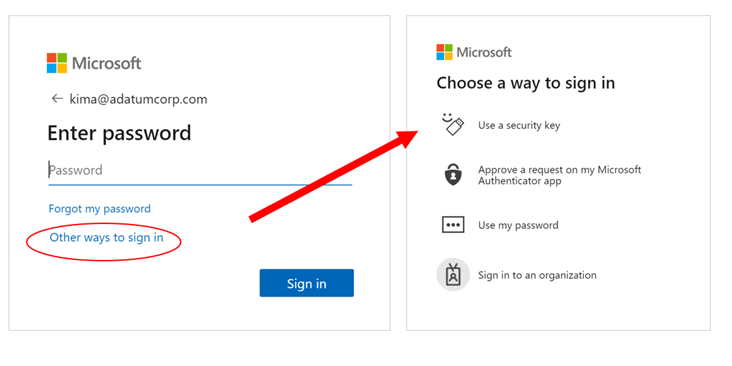
From the beginning, making the passwordless authentication flow delightful has been a top priority, which is why we’ve made numerous improvements to user consistency and flow. We promote credentials that users use frequently so they have the best user experience across devices. This credential will prompt for an authentication method, be it password or Authenticator app or FIDO key, until the user chooses “Other ways to sign-in,” to switch. People can choose when to begin using their new passwordless options and avoid having it foisted on them unexpectedly.
We’ve also fixed a few bugs around credentials in a guest user flow, so if someone chooses to always log in with passwordless phone sign-in at the Contoso tenant, they can start the authentication to Fabrikam using that same method.
To support users who have registered FIDO2 security key or enabled passwordless phone sign-in, we’ve given them the choice to use those strong authentication methods to re-verify their identity if they prefer. This is sometimes called a “step-up” authentication or second-factor flow. Coupled with a Temporary Access pass, this gives users the ability to set up and use one of these strong authentication methods, without needing another credential just for MFA.
Figure 6: Using a FIDO2 security key in a verification scenario
Improved account setup experience in Microsoft Authenticator
One major change to the passwordless phone sign-in experience is the ability to set up your account from directly within the Microsoft Authenticator app. This works best if you’ve already registered at least one multifactor authentication factor in advance or have a Temporary Access Pass.
Figure 7: Microsoft Authenticator with new “Sign in” feature to add work or school account
Authentication methods activity
Reporting is another area where we heard your feedback loud and clear, and have made huge strides since we launched its public preview. You can now view registration and usage information for all your authentication methods in the updated Authentication methods activity blade. This report will help you track the progress of registration campaigns and the adoption of passwordless authentication methods, and dive straight into the data to get more details. Our documentation provides details on permissions and licensing requirements to access these new features.
Figure 8: Authentication methods registration report
Windows Hello for Business joins the club
Our most deployed and used passwordless credential, Windows Hello for Business, is also being brought more closely into the authentication methods management, so users and admins can see their Windows Hello for Business-capable devices at the security info registration portal and the Azure Portal user blade, respectively. Windows Hello for Business registration and usage will also be captured in the new reporting. Lastly, users who want to remain entirely passwordless can use their FIDO2 security keys, in the Windows Out-Of-Box-Experience (OOBE) or via Settings, to set up their Azure Active Directory identity on a Windows device.
Figure 9: Windows Hello for Business devices now show in a user’s list of authentication methods.
Temporary Access Pass
Of course, to have a world without passwords, we must give our customers the ability to set up all these passwordless authentication methods, and recover from lost devices, without performing the traditional password and multi-factor authentication. To that end, we’ve created and just announced the public preview of Temporary Access Pass. This time-limited passcode allows you to set up security keys and the Microsoft Authenticator without ever needing to use, much less know, your password! We can’t wait to get your feedback on how the Temporary Access Pass helps you with your passwordless rollout.
As you have seen, this post contains only a high-level summary of each of the new features that are coming with general availability; for more details and supported scenarios, be sure to visit the links provided to dig deeper into each area.
As excited as we are for this major milestone, general availability is just that – a moment in our passwordless journey. We hope you’ll also now take the next step in identifying the right user segments that can go passwordless today, and then start your organization’s own journey to Go Passwordless, whether that’s moving forward in deploying a Windows Hello for Business upgrade, or piloting a new authentication method, or testing FIDO2 security keys across your workloads. All progress is a positive advance towards improving your organization’s security, and your authentication experience.
As always, we welcome your comments and feedback below or on the Azure AD feedback forum.
Best regards,
Alex Simons (@Alex_A_Simons)
Corporate VP of Program Management
Microsoft Identity Division
Related posts:
Learn more about Microsoft identity:
[ad_2]
Source link












