[ad_1]
Howdy folks!
As we shared earlier this year in The state of apps by Microsoft identity report, organizations have been connecting all types of apps with Azure AD to keep employees connected and secure in this era of remote work. In case you missed Microsoft Ignite earlier this month, we’ve been busy adding new capabilities to help you secure and manage your apps in the cloud and on-premises with Azure AD. Read on to learn more about new app management updates we made this month!
Increase IT efficiency with new enterprise app management capabilities
We’ve released three new enterprise app management updates to give you more ways to secure and manage apps while simplifying employees’ access to the apps they need.
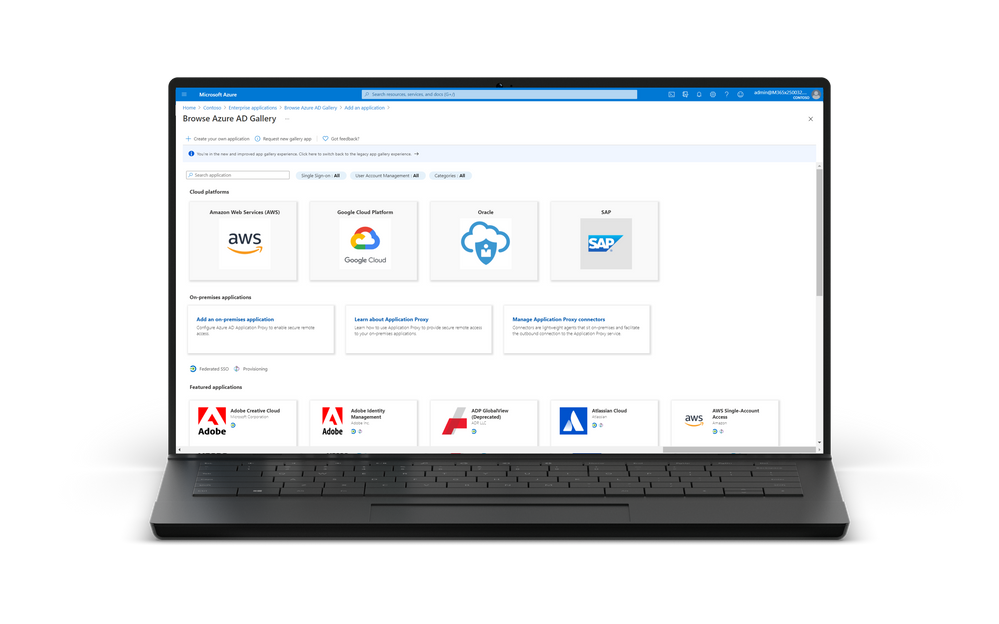
- GA of the new Azure AD app gallery experience – The Azure AD app gallery experience has a refreshed look and feel! The new app gallery experience allows you to filter for applications based on category or on the supported single sign-on type like SAML or OIDC. Additionally, the new app gallery experience includes icons to help you quickly identify which applications support federated single sign-on and provisioning.
- GA of the Application Template API – The application template API available in Microsoft Graph allows admins and developers to programmatically manage applications at scale in the Azure AD App gallery. Admins and developers can now list, search, update, or add applications from the Azure AD app gallery in their tenant via an API.
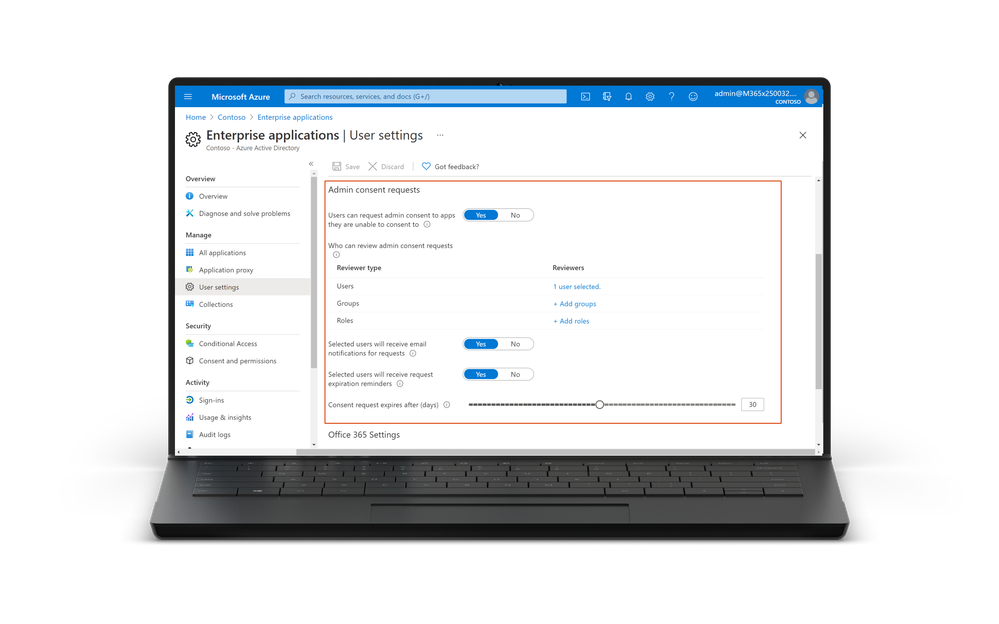
- GA of the Admin Consent Workflow – the admin consent workflow, which is rolling out in the next few days, gives users an easy way to request that an admin review the application they’re trying to use. When users try to access an application that requires consent by an admin, users can now send a request to admins during the sign-in flow. The request is sent via email to admins who have been designated as reviewers and once a reviewer takes action on the request, the user is notified whether access has been granted or denied. You can also list pending admin requests by using APIs in Microsoft Graph or PowerShell. By using our new APIs you can integrate admin consent requests into your existing processes to streamline workflows.
Modernize your app authentication from Active Directory Federation Services (AD FS) to Azure AD
One of the best ways to secure your environment is to manage everything from the cloud—and that includes moving your application’s authentication off AD FS to Azure AD. To help upgrade your application authentication from AD FS to Azure AD, the AD FS activity and insights report is now generally available.
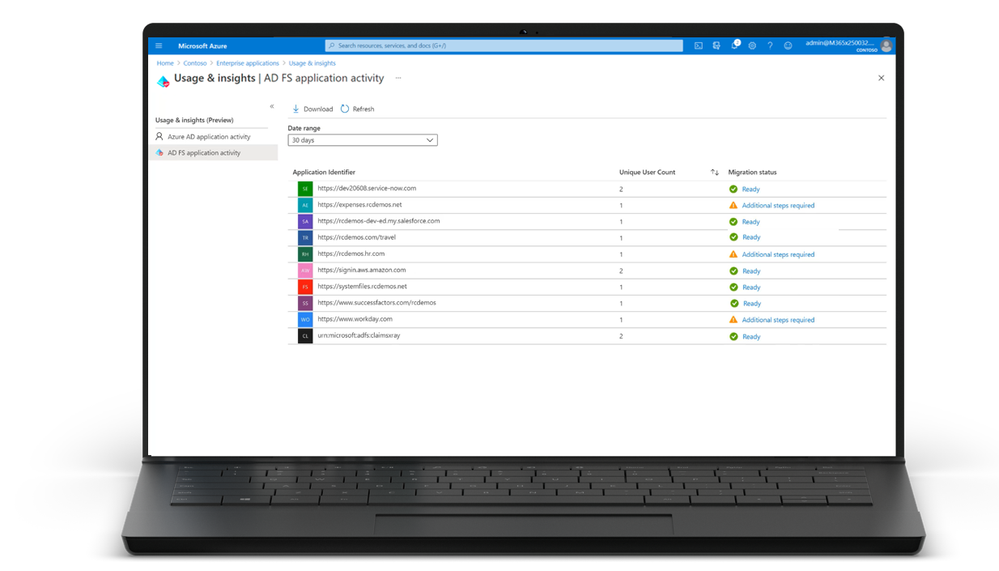
- GA of the AD FS activity and insights report. The AD FS activity insights report lets you quickly identify which of your applications are ready to be upgraded to Azure AD with no configuration changes. It assesses all your AD FS applications for compatibility with Azure AD, checks for any configuration differences, and gives guidance on preparing individual applications for migration to Azure AD.
Secure your on-premises apps with Azure AD application proxy
During the past 12 months, organizations have increasingly relied on Azure AD Application Proxy service to give employees remote access to their on-premises apps. To help you get even more out of Azure AD Application Proxy we’ve made the following enhancements:
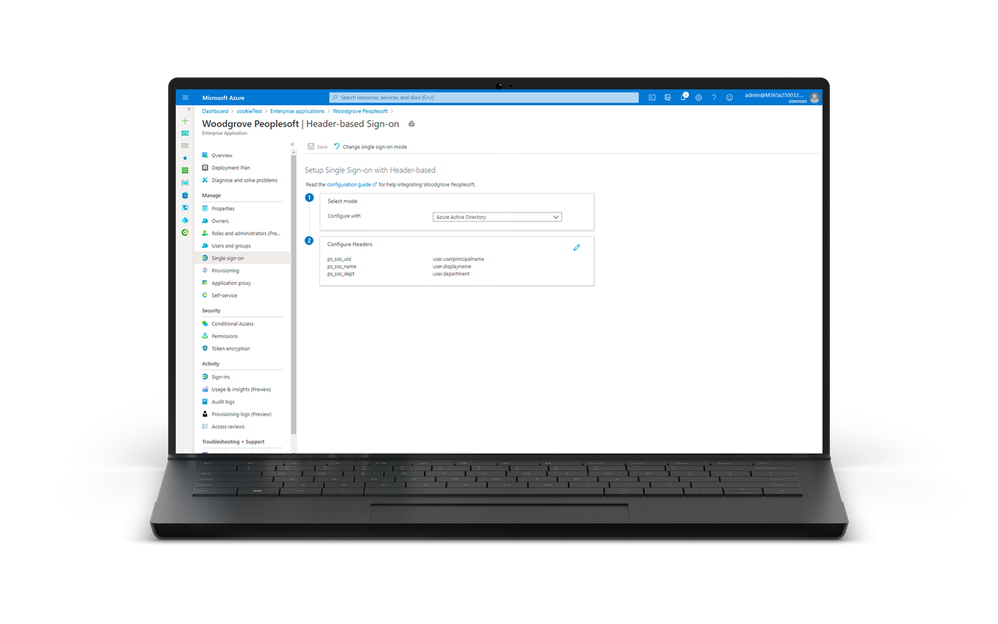
- GA of header-based authentication – Announced last year, Azure AD Application Proxy natively supports apps that use header-based authentication. You can configure a wide range of header values required by your application in Azure AD. These header values will be sent down to the application via Application Proxy. This means that all attributes and transformations available for configuring SAML or OIDC applications can be used as header values.
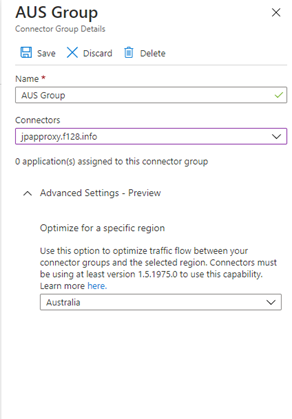
- Optimize your Application Proxy traffic in public preview: You now can now designate which region your Application Proxy service connector group should use. By choosing the closest region to your applications and connectors, you can improve performance and reduce the latency to the App Proxy service.
Tell us what you think
As always, we’d love to hear from you. Please let us know what you think in the comments below or on the Azure AD feedback forum. And be sure watch our on demand Ignite session “Prevent attacks by protecting your applications with Azure Active Directory” to learn more about these new app management capabilities.
Alex Simons (@Alex_A_Simons)
Corporate VP of Program Management
Microsoft Identity Division
Source link