
[ad_1]
Today, I’m excited to share with you several new developments in the journey towards phishing-resistant authentication for all users! This isn’t just essential for compliance with Executive Order 14028 on Improving the Nation’s Cybersecurity but is increasingly critical for the safety of all the orgs and users who bet on digital identity.
TL;DR? Here’s the cheat sheet!
- Microsoft Authenticator announces phishing-resistant passkey support.
- Microsoft Authenticator is FIPS 140-3 compliant on all platforms.
- More configuration options for PIV/CAC authentication.
- FIDO2 support for iOS and MacOS applications.
- Managed policies help you with “secure by design, secure by default.”
Details below!
Microsoft Authenticator is becoming phishing-resistant!
As announced at Ignite 2023, in the first half of 2024, Microsoft Entra ID users will soon be able to register and sign in with device-bound passkeys managed in the Microsoft Authenticator app. This is a cost-effective, phishing-resistant credential available to anyone with the Authenticator app! Passkeys provide you with the latest and greatest security enhancements that will come to the FIDO standard over the next many years – and Authenticator integration lets you take advantage of the security innovations and advanced features Authenticator provides.
To further enhance Microsoft Authenticator and help customers meet compliance requirements, the Authenticator App on Android is now FIPS-140 compliant.
Beginning with version 6.2310.7174, Microsoft Authenticator for Android is compliant with Federal Information Processing Standard (FIPS 140-3) for all Microsoft Entra authentications using phishing-resistant device-bound passkeys, push multifactor authentications (MFA), passwordless Phone Sign-In (PSI), and time-based one-time passcodes (TOTP). For organizations using Intune Company Portal, install version 5.0.6043.0 in addition to the latest version of the Authenticator for FIPS compliance.
The Microsoft Authenticator app on iOS is already FIPS-140 compliant, as announced in December of 2022. Learn more about FIPS 140 complaint for the Microsoft Authenticator app.
Improved configurability for organizations that uses PIV / CAC
In the last year since we announced the General Availability of Certificate-based Authentication (CBA), we’ve seen an increase of over 850% in Entra ID CBA usage for US Government customers. CBA helps our customers in their Zero Trust journey, migrating from on-premises IdPs such as AD FS, while continuing to provide familiar end user experience using PIV / CAC.
We continue our investments in cloud-based CBA with recently added capabilities that allow you to tailor authentication policies by certificate and resource type, as well as user group. You can now select certificate strength for different users, use CBA with other methods for multifactor or step-up authentication, and set high affinity (strong) binding for either the entire tenant or by user group.
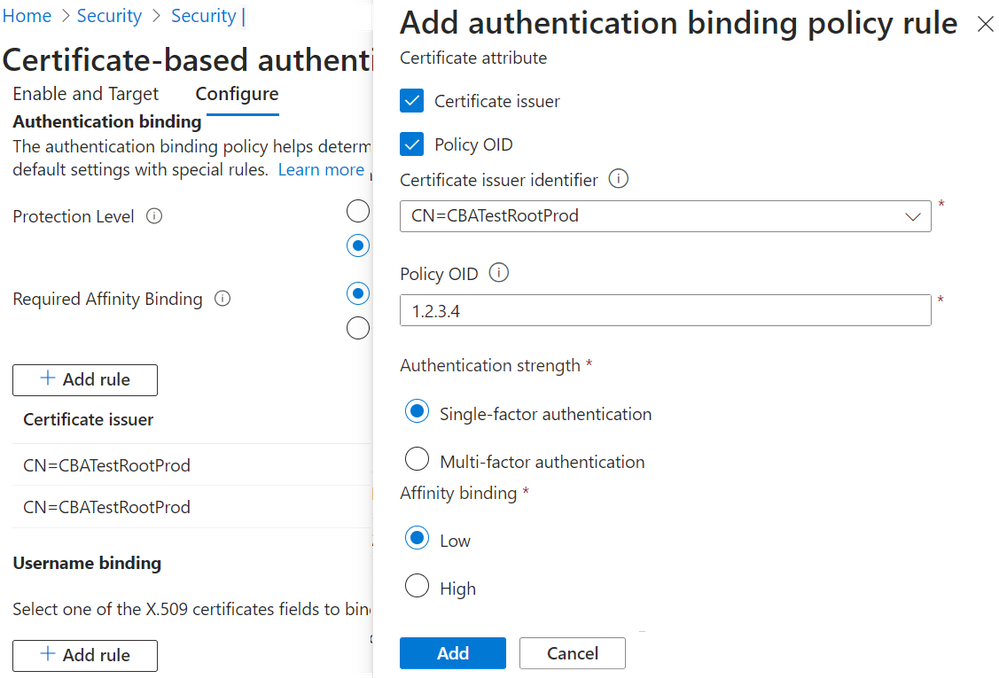
Learn more about our latest enhancements to Microsoft Entra certificate-based authentication.
Additional phishing-resistant authentication options for mobile: FIDO2 support for iOS and macOS applications
In the summer of 2023, we announced support for FIDO2 authentication on iOS and macOS web browsers. Today, we’re excited to announce the public preview of FIDO2 authentication on iOS and macOS . With this release, users who have Microsoft Authenticator installed on iOS or Microsoft Intune Company Portal installed on macOS can sign into Microsoft applications using a FIDO2 security key. This feature is available now on iOS and will be available early next year on macOS.
FIDO2 authentication is also available in MSAL-enabled third-party apps on iOS and macOS that meet the requirements listed in Support passwordless authentication with FIDO2 keys in apps you develop.
Learn more about the supported platforms here.
Adopting secure defaults, aligned with “Secure by design, secure by default” approach outlined by CISA
Earlier this month, Microsoft announced the Secure Future Initiative. As part of this initiative, we will start Auto-rollout of Conditional Access policies. These initiatives align with the “Secure by design, Secure by default” approach called out by The Cybersecurity and Infrastructure Security Agency (CISA), to ensure consumers can trust the safety and integrity of the technology that they use every day.
We believe that tackling cybersecurity challenges is a collective effort. We’re dedicated to collaborating closely with government agencies, security experts, and the broader community to strengthen our collective defenses against cyber threats. Our aim is to provide government customers with the tools and knowledge they need to stay ahead of evolving risks.
Our recent releases and ongoing commitment to enhancing cybersecurity will support our broad set of customers, including the U.S. government customers who are working to meet the Executive Order. Together, we can build a more secure digital future.
Best regards,
Alex Weinert
Learn more about Microsoft Entra:
[ad_2]
Source link




