[ad_1]
Howdy folks,
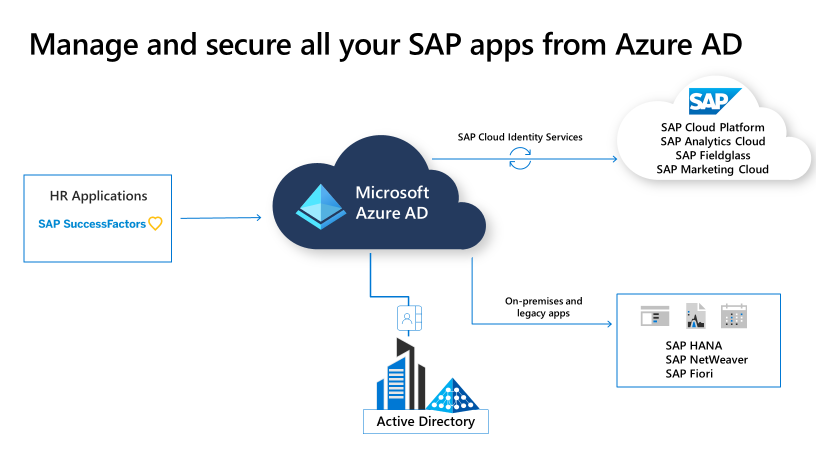
Today, we’re announcing the general availability of user provisioning from SAP SuccessFactors to Azure AD. In addition, SAP and Microsoft have been working closely together to enhance existing integrations between Azure AD and SAP Cloud Identity Services of the SAP Cloud Platform, making it easier to manage and secure your SAP applications.
User provisioning from SAP SuccessFactors to Azure AD is now generally available
With the integration between Azure AD and SAP SuccessFactors, you can now automate user access to applications and resources so that a new hire can be up and running with full access to the necessary applications on day one. The integration also helps you reduce dependencies on IT helpdesk for on-boarding and off-boarding tasks.
Thanks to your feedback on our public preview, we’ve added these new capabilities:
- With enhanced attribute support, you can now include any SAP SuccessFactors Employee Central attributes associated with Person, Employment and Foundation objects in your provisioning rules and attribute mapping.
- Using flexible mapping rules, you can now handle different HR scenarios such as worker conversion, rehire, concurrent assignment, and global assignment.
- In addition to email, we now support writeback of phone numbers, username, and login method from Azure AD to SAP SuccessFactors.
We’d like to say a special thank you to SAP SuccessFactors team who helped us enhance the integration. Here’s what they had to say:
“Enabling end-to-end user lifecycle management is critical. The Azure AD and SAP SuccessFactors integration will help streamline HR and IT processes to help our joint customers save time, improve security, and enable employee productivity.“ – Lara Albert, VP, Solution Marketing, SAP SuccessFactors
We’d like to also thank our preview customers and partners who provided great feedback on different aspects of this integration! Here’s what one of our system integrator partners, Olikka, had to say:
“Inbound provisioning from SAP SuccessFactors to Azure AD and on-premises Active Directory has helped us reduce the time customers need to spend on-boarding/off-boarding and adjusting access through the employee lifecycle. The integration that Microsoft has delivered means that we can avoid building complex custom connectors and managing on-premises infrastructure. This enables Olikka to get the customer up and running quickly while leveraging their existing Azure AD subscription.” – Chris Friday, Senior Project Consultant, Olikka
Using Azure AD to manage and secure your SAP applications
Our new provisioning integration between Azure AD and SAP Cloud Identity Services allows you to spend less time creating or managing accounts for individual SAP applications. With this integration, you can now use Azure AD to automatically provision user accounts for SAP Analytics Cloud. In the coming months, we will expand this support to additional SAP applications like SAP S/4HANA, SAP Fieldglass, and SAP Marketing Cloud.
We’re also enabling One-click SSO to simplify the configuration and setup of single sign-on with SAP Cloud Identity Services. One-click SSO allows you to quickly setup single sign-on between Azure AD and SAP Cloud Platform without needing to copy and paste values from different admin portals.
Learn more
User provisioning from SAP SuccessFactors to Azure AD requires an Azure AD P1 license, all other features referenced in this blog are available across all licensing tiers. To get started with these integrations, read our SAP identity integration documentation.
SAP Cloud Platform is also available on Azure regions around the globe to complement your SAP S/4HANA on Azure implementations, providing low latency and ease of integration. Learn more about SAP solutions on Azure at www.microsoft.com/sap and explore our SAP on Azure use cases to get started.
Together, our integrations with SAP allow you to manage and protect access to all your critical SAP landscape. As always, we’d love to hear any feedback or suggestions you may have. Please let us know what you think in the comments below or on the Azure AD feedback forum.
Best regards,
Alex Simons (@Alex_A_Simons)
Corporate VP of Program Management
Microsoft Identity Division
Learn more about Microsoft identity:
Source link