[ad_1]
Hello friends,
As a follow-on to our previous External Identities update, today I’m really excited to announce the availability of cross-tenant access settings for external collaboration in public preview.
Cross-tenant access settings enable you to control how users in your organization collaborate with members of external Azure AD organizations. Now you’ll have granular inbound and outbound access control settings that work on a per org, user, group, and application basis. These settings also make it possible for you to trust security claims from external Azure AD organizations like Multi-Factor Authentication (MFA), device compliance, and hybrid Azure AD joined devices.
When it comes to external collaboration, you’ve told us that:
- You want to ensure only approved external users can access your apps and resources, and only approved users from your organization can access external apps and resources.
- You want to trust MFA claims from your partners, so your guest users who have performed MFA in their directories aren’t prompted for MFA again in your directory.
- You want insights on what apps your users are accessing externally and what apps external users are accessing in your organization.
So, we’ve designed the experience based directly on your feedback. Let’s take a look at how it works.
How to get started with cross-tenant access settings
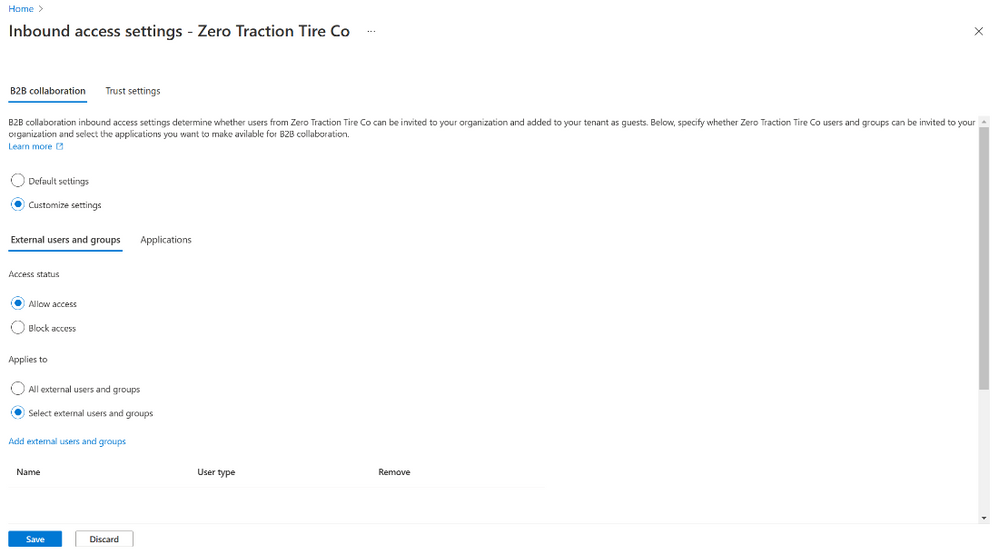
Control the external users and organizations that can collaborate with your users
Inbound settings let you control which external users can access your apps and resources. You can allow all external users to collaborate with you, or you can limit access to only allow specific users and groups from specific organizations. You can also specify the apps in your organization you want these users to be able to access. Read the
Control the external organizations your users can collaborate with
Outbound settings let you control which external organizations your users can collaborate with. You can allow your users to collaborate with all external organizations or only allow specific users and groups to access specific apps in specific external organizations.
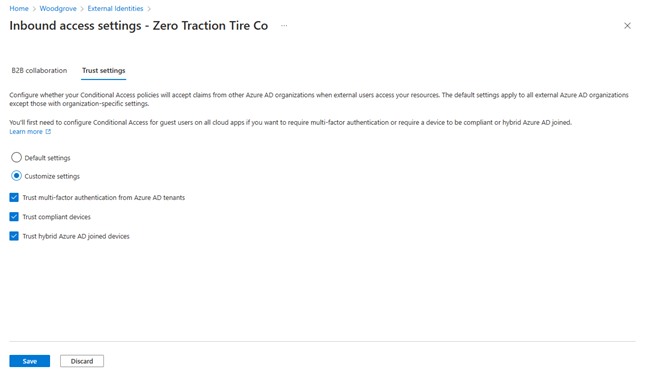
Trust security claims from external Azure AD organizations for MFA and device
Inbound trust settings let you trust the MFA external users perform in their home directories. This addresses the feedback you’ve given us around your external users having to perform MFA multiple times, both in their home directories and in your directory. Now you can enable a seamless authentication experience for your external users by trusting the MFA they perform in their home directories so they don’t need to complete MFA with you. You’ll also save on the MFA costs incurred by your organization.
Inbound trust settings also let you trust devices that are compliant, or hybrid Azure AD joined in their home directories. Previously, you were not able to enforce device-based Conditional Access policies such as requiring compliant devices or hybrid Azure AD joined devices for external users. Using inbound trust settings to accept device claims from external Azure AD organizations, you can now protect access to your apps and resources by requiring that external users use compliant, or hybrid Azure AD joined devices. Learn how inbound trust settings work with Conditional Access.
Know who’s accessing your organization’s resources
Through the sign-in logs, you can see which external apps your users are accessing, as well as the external users who are accessing your resources. documentation
Start by evaluating how you collaborate
Before you customize cross-tenant access settings, it’s important to understand which external organizations need access to your apps and resources and which of your users need to access external apps and resources so that you don’t inadvertently block ongoing collaboration. We recommend that you use this workbook to understand how your organization is collaborating with external organizations to avoid any business interruption.
What customers are saying
Bupa is an international health insurance and healthcare group with over 31 million customers worldwide. As they have been testing this feature, they’ve said:
“This feature lays the bedrock for increased collaboration and most importantly security for our large and complex organization.”
In addition, we have enabled customers in the most regulated industries to open collaboration for the first time and recently received this feedback:
“Cross-tenant access settings will help us greatly reduce risks, increase security, and enable us to better support our business in external tenant access and collaboration needs. Happy security department, happy business, and importantly happy auditors and regulators.”
We love hearing from you, so share your feedback on these new features through the Azure forum or by tagging @AzureAD on Twitter.
Robin Goldstein
Twitter: @RobinGo_MS
Learn more about Microsoft identity:
[ad_2]
Source link