[ad_1]
Howdy folks,
Azure AD Conditional Access can ensure that the right people have the access to resources they need from wherever they are. We’ve had a ton of requests for Conditional Access APIs to manage policy at scale. That’s why it is so cool that at Microsoft Ignite, we announced that Conditional Access APIs and named location APIs has reached general availability in Microsoft Graph!
As you progress on your journey with Conditional Access policy governance, you’ll want to shift from manually managing each policy definition in the Azure portal to something more manageable and repeatable at enterprise scale.
Vikas Deora, one of our Identity team program managers, has written a guest blog post with information about the new APIs and how to get started.
As always, we’d love to hear any feedback or suggestions you may have. Please let us know what you think in the comments below or on the Azure Active Directory (Azure AD) feedback forum.
Best Regards,
Alex Simons
Corporate Vice President Program Management
Microsoft Identity Division
——-
Hi everyone,
My name is Vikas Deora. I’m a program manager on the identity team at Microsoft, focused on Azure AD Conditional Access.
At Microsoft Ignite, we announced that Azure AD Conditional Access APIs and named location APIs are now generally available. We have updated the APIs based on your feedback from the private and public previews with:
- Inclusion in the Azure AD PowerShell module
- enabled app-only permissions
- improved error messages
The APIs are documented here. As part of the Microsoft graph, the interactions will be familiar to you – the core policy object lets you specify the conditions, controls, naming data and state for policies.
Get started
Here are some examples for you to get started using these APIs:
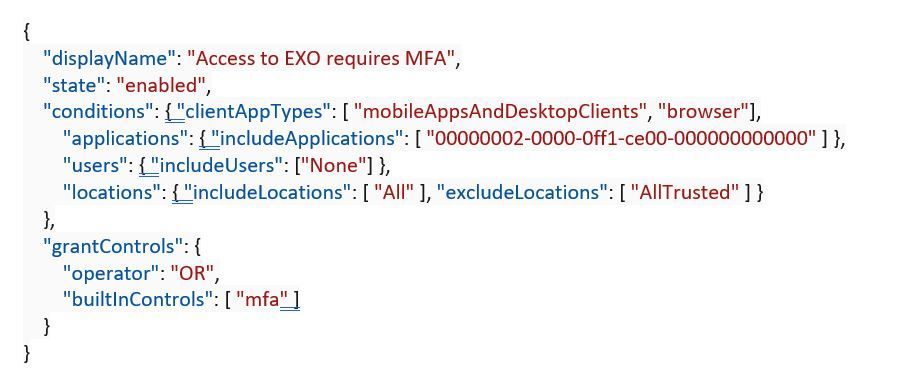
If you want to create a new policy to require MFA when accessing Exchange Online from an un-trusted network:
POST https://graph.microsoft.com/v1.0/identity/conditionalAccess/policies
Content-type: application/json
To list all policies:
GET https://graph.microsoft.com/v1.0/identity/conditionalAccess/policies
Or delete a policy:
DELETE https://graph.microsoft.com/v1.0/identity/conditionalAccess/policies/{id}
Pretty straightforward – but where it gets fun is with the automation you can pull together – read on!
Conditional Access API samples – treating policy just like code
Many of you told us you wanted to be able to treat Conditional Access policies just like code, so we have put together several scripts and tutorials for you to do just that. Here are the steps you can follow:
- Configure policies in your environment using templates like those offered by your favorite IDEs. Check out this tutorial to get you started with some quick-start API templates, and to learn more, check out the conditional access API overview.
- Test the changes in a safe environment before starting an automated safe rollout to production. Try this script that allows you to perform safe rollout of policies from pre-production to production with approval workflow!
- Deploy policies gradually to your user population, allowing you to manage support impact and spot issues early. Start with this script for one-click policy deployment with approval workflow!
- Monitor policy configuration and the usage of policies in your environment. You can use this script to trigger alerts when someone edits key Conditional Access policies. You can choose to update Teams channels, get notifications in email that you can respond to or sign-up for notifications on other channels you prefer.
- Manage: Policies may change over time. Safely make changes to the policy and rollout in your environment. Use this script to back up your policies in Azure or other cloud solutions or even on-premises. Here are a few bonuses – we have published a script that will manage emergency accounts for you, and you can try this script to help you manage resilient security policies that will fail-over in the case of a service issue .
These are just a few key things customers have told us they want to do with the Conditional Access APIs, but we’d love to see a community around this where you can share your best ideas and scripts with each other! We’ve created a for Azure AD conditional access where these conversations can happen.
If you have an interesting scenario and would like to request a sample script to do this, please share on the Azure AD feedback forum.
All the best,
Vikas Deora
Program Manager
Microsoft Identity Division
Source link