[ad_1]
Hello friends,
I wanted to share that cross-tenant access settings for external collaboration is now generally available! I’m proud of the work the team has done to bring secure collaboration policies to life, and excited to share what we’ve learned from those who’ve implemented the public preview.
To tell us more about the adoption and mainline scenarios we’ve heard from customers, I’d like to welcome Josh Douglas, Senior Product Manager, to take over from here!
Thanks, Robin! I’m excited to tell all of you more about cross-tenant access settings and our journey to general availability! During public preview, we saw many customers adopt cross-tenant access settings to meet scenarios and requirements that previously weren’t possible. To help illustrate this, here are some stats:
- Over 5,000 tenants have configured an MFA trust for another organization
- Over 2,000 tenants have configured either a compliant or hybrid Azure AD joined device trust
These stats align with the great feedback we’ve heard from you that this capability will help secure collaboration beyond your own organization in ways not previously possible!
Reduce friction for external users while ensuring secure collaboration
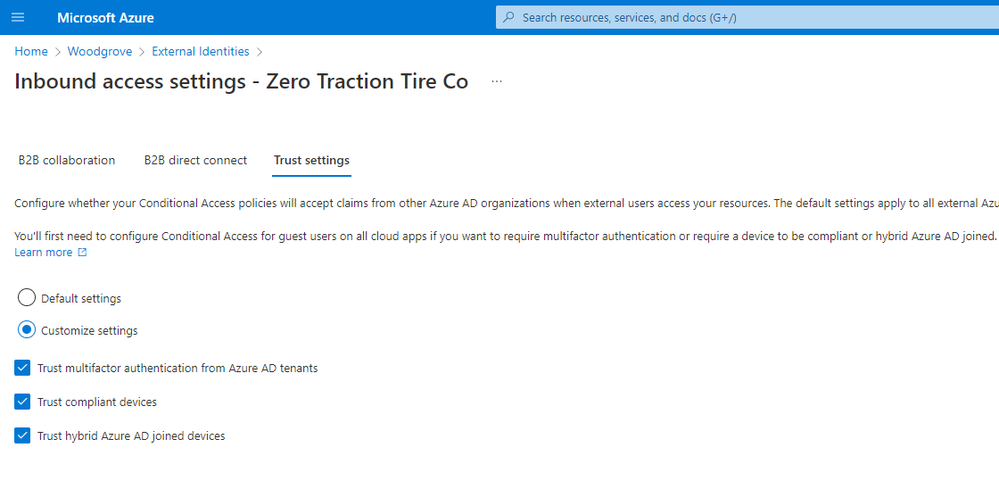
We heard from you that managing MFA registrations for external users adds overhead and increases your support costs. Additionally, your users are frustrated when they must register and perform MFA, sometimes multiple times, across the different organizations that they collaborate with. With inbound cross-tenant access settings, more of you are trusting security claims from external Azure AD organizations for MFA to ensure external users perform MFA in their home tenant when required by Conditional Access polices. This eliminates the need for users to complete a second MFA when accessing resources in another tenant, which significantly reduces friction for them. This enables you to keep the security posture required by your organization while not having to manage MFA registrations for your external users, thereby reducing your support costs. You also save on the MFA costs incurred by your organization.
You have also said that you are concerned about the types of devices external users access your apps and resources on. Enforcing Conditional Access policies to require that external users access your resources on complaint devices or hybrid Azure AD joined domain is now possible with inbound cross-tenant access settings. By trusting device claims from external AD organizations, you know that external users access your apps and resources on managed devices and further protects your data.
Learn how inbound trust settings work with Conditional Access.
Trust multifactor authentication, compliant, and hybrid Azure AD joined devices from specific external organizations.
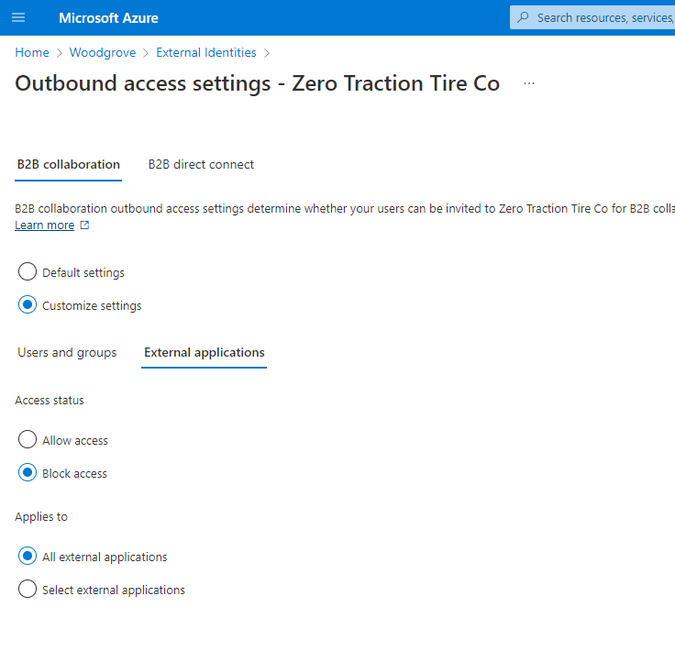
Ensure your users only collaborate with external organizations that you approve of
As much as it is important to secure your apps and resources from unauthorized external access, it may be important for you to ensure that your users are only collaborating with organizations that you approve of. Your organization could belong to a highly regulated industry and be paranoid about data exfiltration. Your organization could be an educational institution where students chat with unauthorized external organizations on Teams using their school accounts. In these scenarios, you could deploy outbound cross-tenant access settings that block your users from accessing unauthorized external tenants. It took one customer in the education industry less than 5 minutes to test and deploy the policies. Security with simplicity is the way to go!
Learn how to implement outbound controls with cross-tenant access settings.
Target a group of users to block them going outbound to a specific organization.
Block that same group of users from accessing any application when going outbound.
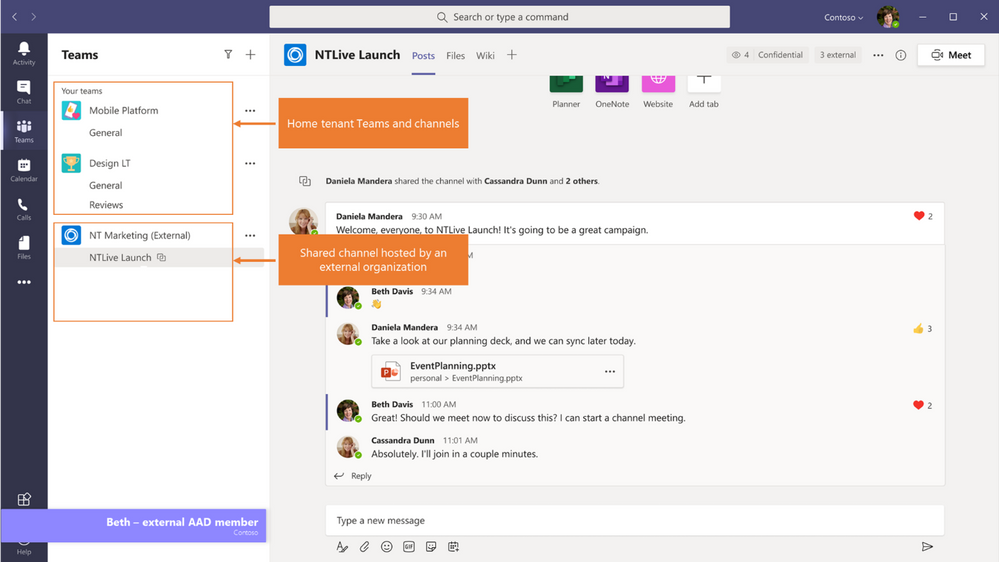
Collaborate seamlessly on Teams shared channels
If you mainly collaborate with external users on Teams and SharePoint, Teams shared channels enables seamless collaboration where you can chat, share files and collaborate with users from multiple organizations simultaneously. The inbound and outbound cross-tenant access policies that we discussed above apply to B2B direct connect users of Teams shared channels as well.
Shared channels provide seamless collaboration without the user having to switch tenants.
What customers are saying
During public preview, many customers have tested the above capabilities and have said:
“Cross-tenant access settings provides needed controls for securing collaboration with external organizations that supports us on our ‘zero trust’ journey beyond our own estates.”
-Customer in insurance industry
“Azure AD B2B has transformed how our business integrates with our partners and clients and how we offer access to services and products. Cross-tenant access settings take this to the next level by providing the capabilities to implement more granular and mutually agreeable level controls. This has been a critical requirement from many of our clients and will enable both parties to implement the controls necessary to satisfy data protection requirements without compromise.”
-Customer in professional services industry
“We are very excited about Cross Tenant Access as these features will offer enhanced security controls and very importantly enable us to force login to external tenants from our managed endpoints. Cross Tenant Access will help us greatly reduce risks, increase security, and enable us to better support our business in regard to their external tenant access and collaboration needs. Happy security department, happy business, and importantly happy auditors and regulators”
-Customer in financial services industry
This is just the beginning…
We are excited for you to start using cross-tenant access settings! Before you get started, we recommend that you evaluate how you collaborate with external organizations so that you do not inadvertently block needed collaboration. We have tried to make this simple by publishing this workbook to help you understand all your inbound and outbound collaborations.
We love hearing feedback on how you’re using the product or how we could make it better going forward. Please share your feedback through the Azure forum or by tagging @AzureAD on Twitter!
Robin and Josh
Twitter: @RobinGo_MS, @joshkdouglas
Learn more about Microsoft identity:
Source link