
[ad_1]
Howdy!
We’re delighted to share that the public preview of Azure Active Directory Identity Protection in Microsoft 365 Defender (M365D) is now rolling out, further empowering security professionals to detect and respond to identity compromise. You may already be familiar with investigating Identity Protection detections in the Microsoft Entra or Azure portal, and that’s not going away. What’s new is that these detections will now also be available as alerts in the Microsoft 365 Defender portal! If you use Microsoft 365 Defender to investigate endpoint, application, and email alerts, you no longer need to switch portals to see your Identity Protection alerts! Tracy Shi, product manager of Identity Protection, will take you through what this means for you.
Best regards,
Alex Weinert (@Alex_T_Weinert)
Director of Identity Security
Microsoft Identity and Network Access Security Team
Hi folks!
Azure Active Directory (Azure AD) Identity Protection alerts are now available in the Microsoft 365 Defender portal. We’re excited about the efficiency and simplicity this integration brings to security teams.
Azure AD Identity Protection leverages trillions of signals to detect compromised identities, provides insights into risky users and detections, and offers mechanisms to automatically remediate risks. Including Identity Protection detections as part of a larger incident in Microsoft 365 Defender now helps security teams identify the end-to-end attack story more efficiently and respond to compromised identities more quickly.
Identity compromise is the most common starting point for breach, so Identity Protection detections are often the first alarm that goes off. Now that these crucial early indicators are included in Microsoft 365 Defender incidents, they provide greater clarity on how identities were leveraged in the attack. If you’re interested in seeing just the Identity Protection alerts, you can filter by the service source. High-impact alerts are shown by default in Microsoft 365 Defender, and you can change the Alert service setting to view all or no Identity Protection alerts.
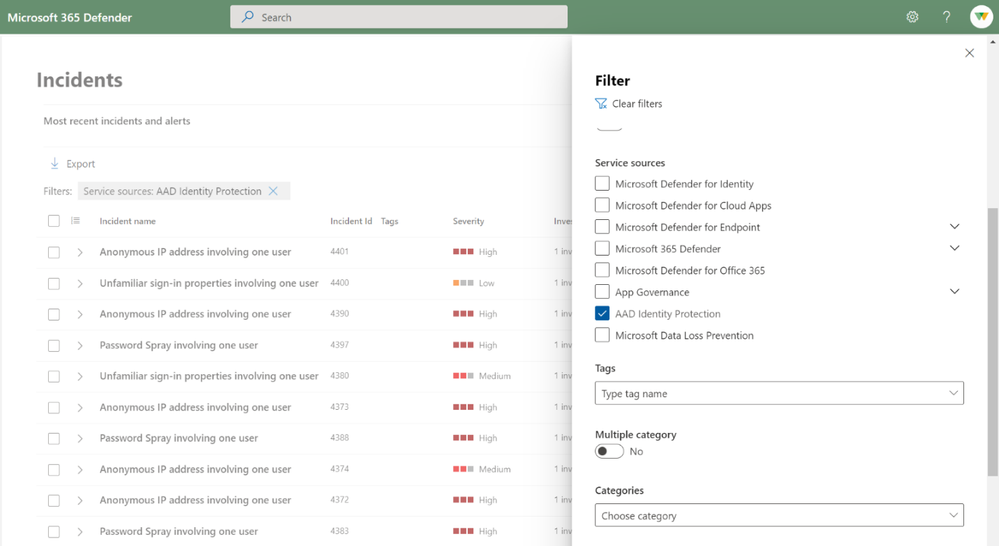
Once you’re finished with the investigation, you can update the status of the incident and the Identity Protection alert, and it will sync back to Azure AD Identity Protection. Alert status syncing between our first-party partners has been a long time ask, and we’re thrilled that it’s launching with this public preview! All Azure AD Identity Protection alerts within Microsoft 365 Defender are also available via Incidents API .
Additionally, the Microsoft 365 Defender User Page provides you the ability to see the user’s current risk score generated by Identity Protection and give feedback on potentially compromised risky users. You can confirm them as compromised to move them to high risk or dismiss them to resolve the risk. To best leverage these signals and the other wealth of identity threat intelligence in Identity Protection, we recommend enabling the risky user and risky sign-in policies for access control and automatic risk remediation.
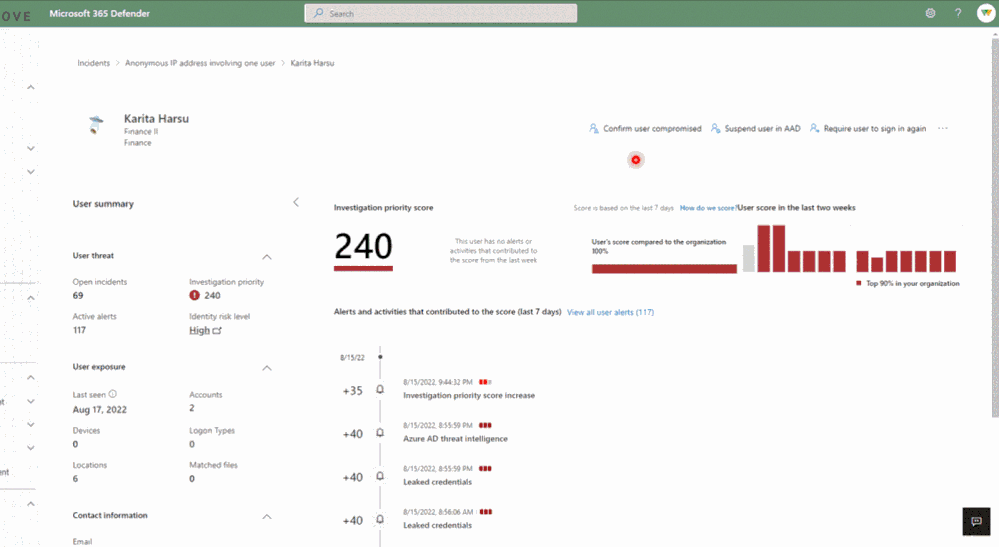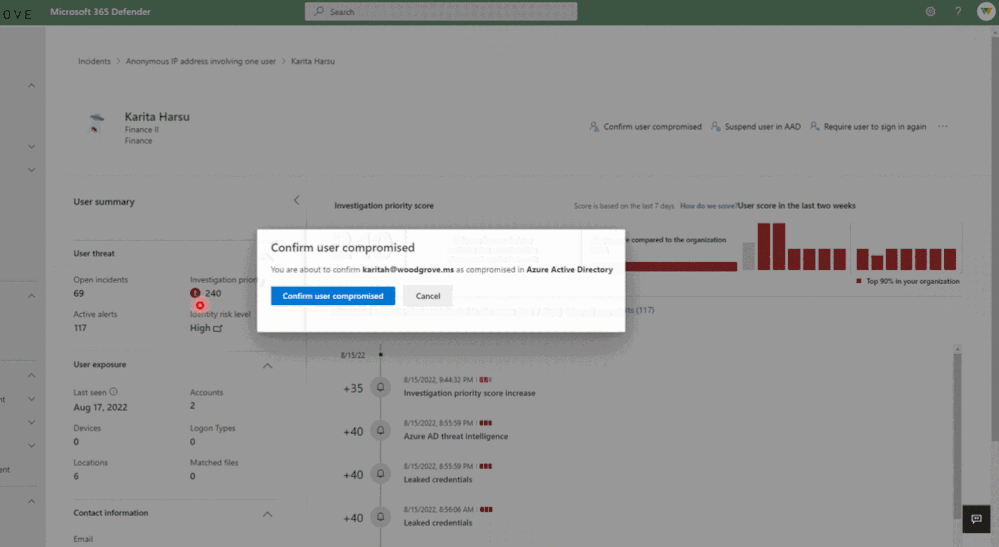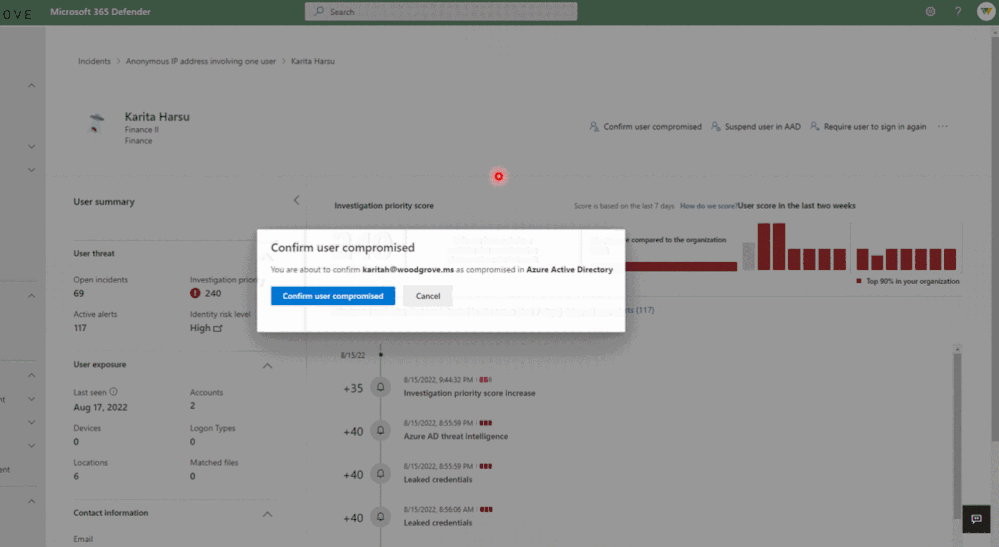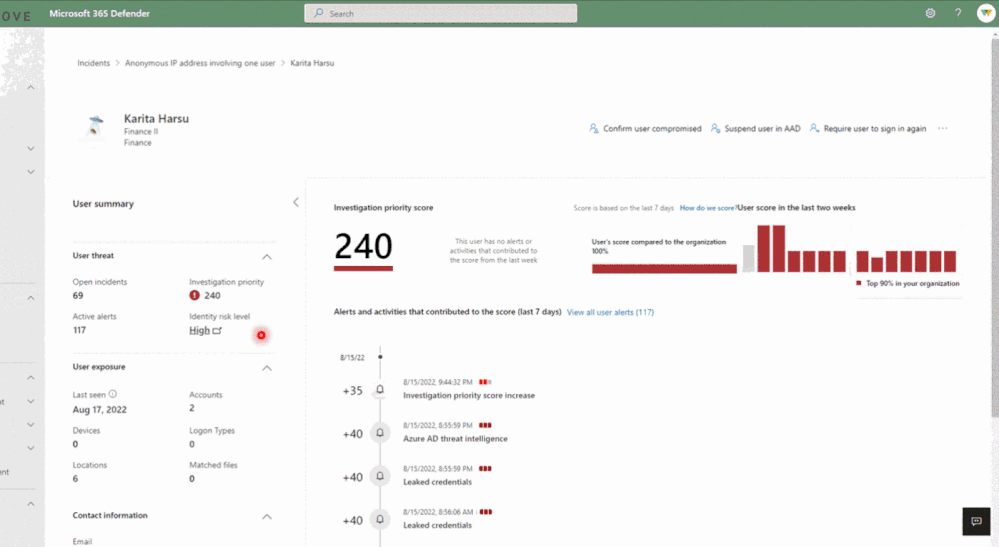
We can’t wait for you to try it out and invite you to get started today by visiting security.microsoft.com and reviewing the documentation.
Stay Secure!
Tracy Shi
Product Manager II
Microsoft Identity and Network Access Security Team
Learn more about Microsoft identity:
Source link




