[ad_1]
Howdy folks,
I’m excited to announce the General Availability of Azure AD My Sign-Ins—a new feature that allows enterprise users to review their sign-in history to check for any unusual activity. As we discussed in the Public Preview blog post, the My Sign-Ins page empowers users to see:
- If anyone is trying to guess their password.
- If an attacker successfully signed in to their account from a strange location.
- What apps the attacker accessed.
The newest addition to this page allows end users to report “This wasn’t me” or “This was me” on unusual activities. Robyn Hicock, who managed this feature, wrote a guest blog post where she dives into the details on this update. You’ll find her blog post below.
As always, we’d love to hear any feedback or suggestions you may have. Please let us know what you think in the comments below or on the Azure AD feedback forum.
Best regards,
Alex Simons (@Alex_A_Simons)
Corporate VP of Program Management
Microsoft Identity Division
—————————————————–
Hi everyone!
I’m super excited to share details about the updates we’ve made to the My Sign-Ins page. We heard your feedback during the Public Preview and learned that users want to easily determine whether a sign-in was theirs or not.
Unusual activity
We now highlight suspicious activities that we’ve detected with Identity Protection at the top. For example, if a risky sign-in was automatically detected, it would get bubbled up to the top under a new section for “Unusual activity”:
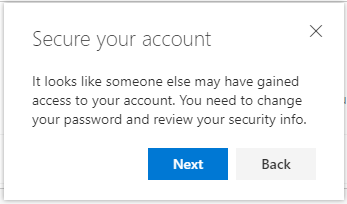
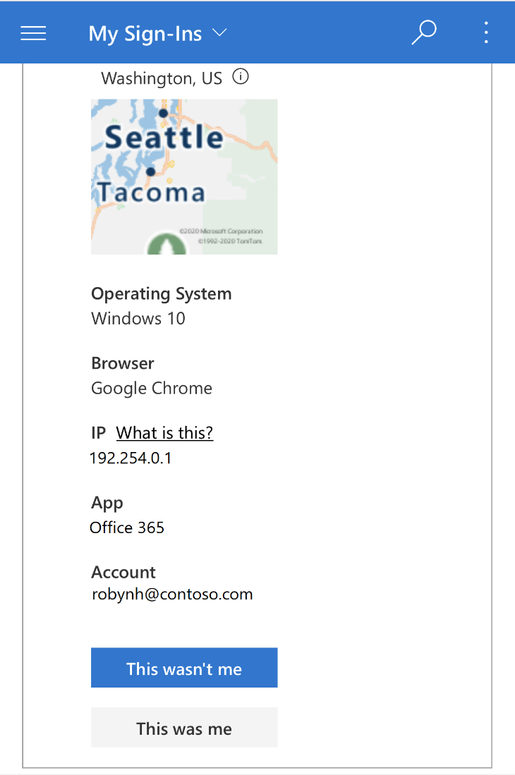
We also added “This wasn’t me” and “This was me” buttons for unusual activities. If a user chooses “This wasn’t me”, then they would see this dialog:
They would then be taken to the Security info page to review and update their authentication methods. To learn more about managing security info, check out the blog post for Combined MFA and password reset registration.
If a user chooses “This was me”, then they would see this dialog:
The end user feedback will help improve the accuracy of our risk detection systems. We will study the user feedback before allowing user reporting to change the risk states in Identity Protection. You can monitor what your users are choosing by checking the audit logs, and use that information to help you decide whether to confirm or dismiss the risk.
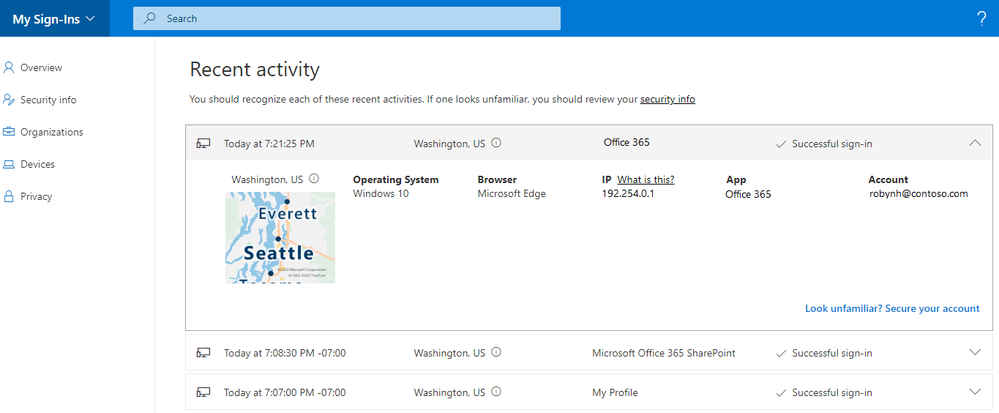
Recent activity
If a user doesn’t have any suspicious sign-ins, then they’ll just see the “Recent activity” section. Users can also review their normal sign-ins and report if anything looks strange by clicking “Look unfamiliar? Secure your account”.
Users can also see if anyone else is trying to guess their password. In that case, they’d see an “Unsuccessful sign-in” like this:
Searching and Filtering
We also heard your feedback about better filtering to sort through all the noise. Now you can use the Search bar at the top to look at only the “Unsuccessful” sign-ins.
You can also use the Search bar to filter for other details like the app, browser, location, operating system, etc.
Finally, we made My Sign-Ins more mobile-friendly too!
If you’re curious about your personal email too, we have similar features in the Recent Activity page for consumer Microsoft Accounts at: https://account.live.com/activity – Check it out!
Feedback
As always, we’d love to hear your feedback and suggestions. Please let us know what you think in the comments below or on the Azure AD feedback forum.
Thanks!
Robyn Hicock (@Robyn.Hicock)
Senior Program Manager
Microsoft Identity Security and Protection Team
Learn more about Microsoft identity:
[ad_2]
Source link