[ad_1]
I’m excited to announce the integration of Entra Identity Governance Entitlement Management with a very cool technology we recently introduced, Microsoft Entra Verified ID!
If you think about what you need to onboard new users including employees, contractors, partners, or other business guests, it often includes verifying identity information and credentials. This process can be tedious and time-consuming, requiring users to fill out redundant online forms or paperwork, ultimately delaying hiring timelines and ramp-up periods.
To ease this friction, we previously introduced custom questions and attribute collection in Microsoft Entra Identity Governance Entitlement Managem…. Today, we’re simplifying this onboarding process even further, with the integration of Microsoft Entra Verified ID checks in entitlement management.
Let’s explore this new feature and understand how it fits into the access request management process.
Scenario: Require independently verified credentials before approving access to confidential resources
Imagine you’re working with an external marketing agency on a project for a new customer. Your organization requires consultants to complete a Verified Vendor certification before they can be onboarded to new projects. For this to be completed, consultants must email a notarized copy of their certificate before they can even begin the onboarding process. How inconvenient and time consuming!
You recently learned that the agency issuing this required Verified Vendor certification has started issuing verified IDs. Today, you rely on access packages containing resources needed for your projects. You decide to incorporate verified ID checks into the already existing onboarding process for these consultants when they request access to these access packages.
Here is how you can do it.
Configure automatic access to access packages with Verified ID in just 3 steps!
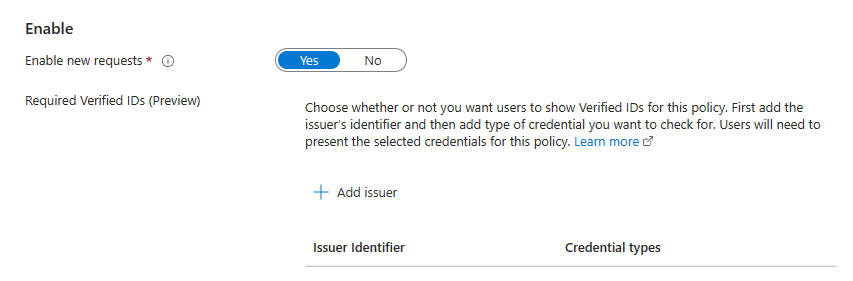
1) Add verified ID requirement in your access package: You go to Entra Identity Governance, Access Packages and choose the access package you want to protect. They add a new policy by going to the Policies section and clicking on + Add policy. On the Requests tab, you find the Required Verified IDs section.
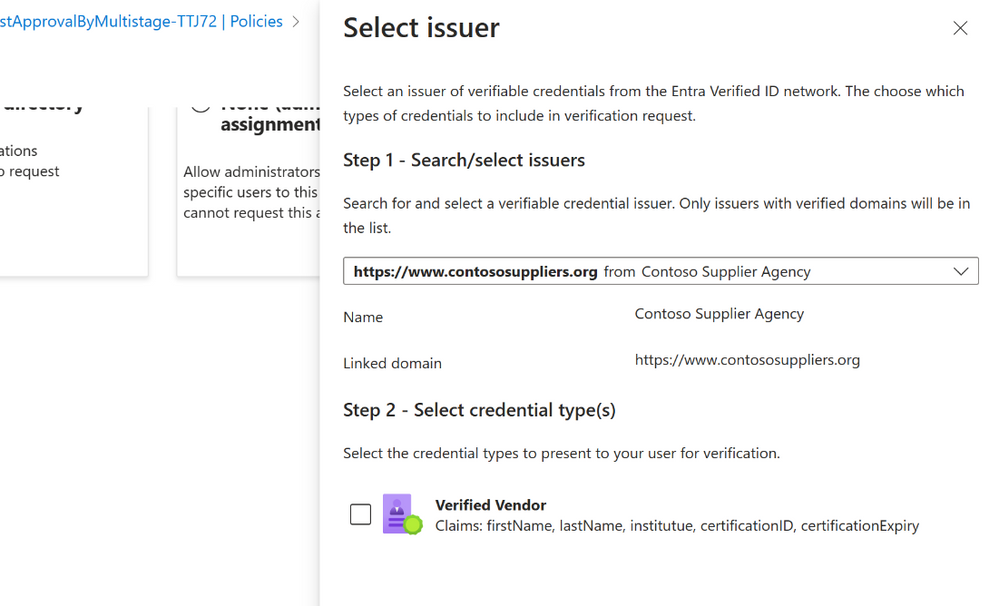
You click on + Add issuer. Search for Contoso Supplier Agency in the Entra Verified ID network using the dropdown and select the Verified Vendor credential type.
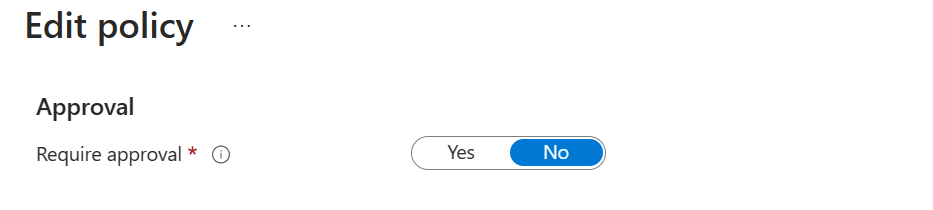
2) Remove manual approvals: Since the Verified Vendor credential is the verified proof of the user’s certification from a trusted issuer, you can opt out of having approvers review requests and make onboarding even more seamless.
When a consultant being onboarded to the project requests access to the access package from the My Access portal, they’ll be asked to present their Verified Vendor credential from Microsoft Authenticator.
All they need to do is scan the QR code on the screen. This will allow them to present the credentials and, since the access package policy does not require manual review by an approver, the consultant will receive automatic access after their credentials have been verified by the issuing agency. For instance:
3) Check audit logs for request activity: You can navigate to Entra Identity Governance, Audit Logs and check that access to the access package has only been granted when a verified ID has been presented.
What customers and partners are already telling us
Swiss IT is a Microsoft partner that works with customers who have an in-person manual process for identity proofing when users need to access sensitive data. Swiss IT issues verified IDs containing necessary digital proofs. Using this integration, those customers can automatically validate a user’s citizenship status when the individual submits their access request.
“With the integration of Entra Verified ID into Entra Identity Governance, we can automate identity validation and approval in our entitlement management flow. This helps us secure collaboration environments for highly sensitive data, like pharmaceutical development, while staying compliant with company regulations and contractual obligations.”
– Jens Lorenz (Strategic Consultant, CISSP, CCSP, CIPT at Swiss IT)
Similarly, some customers have a manual review process for external user access, even for non-privileged productivity applications. These customers would like to collaborate with people outside their organization by setting up scoped access packages that can automatically be assigned to guests if they provide the required verified ID.
“Many large enterprises have several service providers, where they do not necessarily know which individual is coming for the maintenance, but rather just trust the employer. A lengthy pre-onboarding is in those cases not possible. Verified ID together with Entitlement Management allows us to request access for those individuals on the fly by verifying their identity during an on-demand access request process.”
– Erik Siebler (IAM Lead, DXC)
Protect access to your resources with Entra Identity Governance entitlement management and incorporate Entra Verified ID in your access request flows!
To start with Entra Identity Governance entitlement management, click here for a step-by-step guide on how to set up an access package. Once you’ve set up your access package, check out this guide on how to configure your access package with a verified ID requirement.
To use a verified ID check during the entitlement management request process, you’ll need to onboard your tenant to the Verified ID service. Check out this tutorial on how to configure your tenant for Microsoft Entra Verified ID.
Go today and issue a verified ID to your users and configure an access package with a verified ID requirement to test out this feature!
We’d love to hear your feedback and are excited to continue evolving user identity together!
Joseph Dadzie, Partner Director of Product Management
LinkedIn: @joedadzie
Twitter: @joe_dadzie
Learn more about Microsoft identity:
[ad_2]
Source link