[ad_1]
Hello friends,
Happy new year everyone! With the new year come new possibilities. Today I’m excited to announce two Azure AD External Identities updates including the public preview of multi-factor authentication (MFA) with time-based one-time passcode (time-based OTP) for B2C users and an important change to our support for data residency in Azure AD B2C directories.
Strengthen MFA for B2C users with time-based OTP
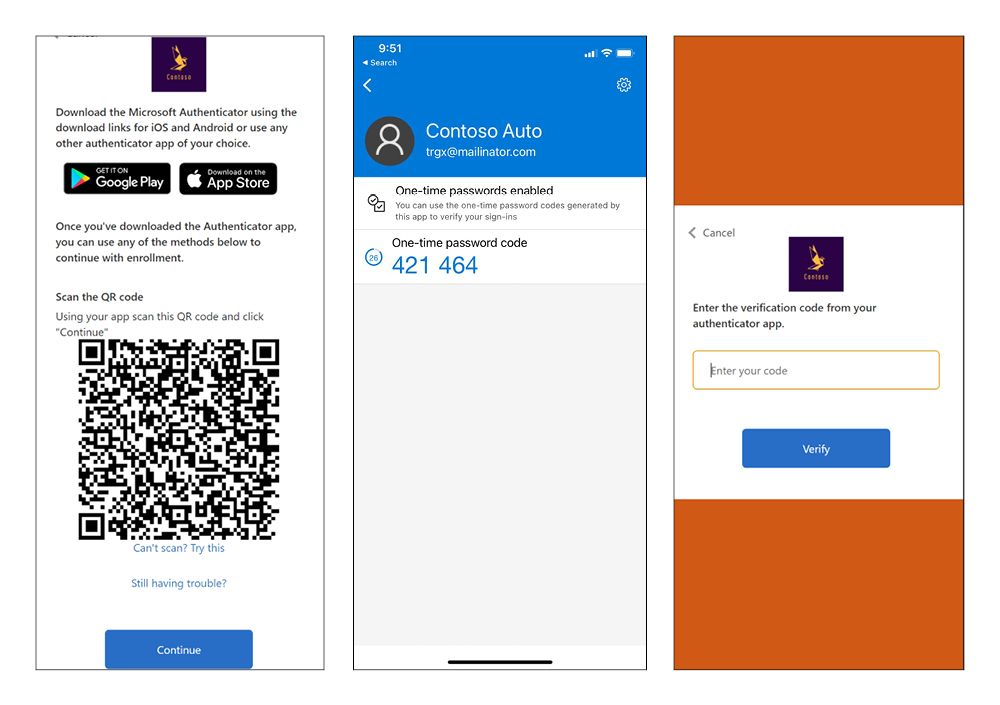
Rising fraud and security attacks make it critical to protect consumer accounts with more secure forms of MFA. By incorporating time-based OTP through an authenticator app in your B2C user flows, you can provide a higher level of security compared to existing email and phone factors, without incurring additional telephony charges. Learn more from my colleague, Alex Weinert, about why we believe app-based MFA is more secure than email and phone MFA alone.
Time-based OTP for your user accounts can be configured with any authentication application. We recommend setting up your time-based OTP with Microsoft Authenticator, which uses encrypted bi-directional communication for authentication status and supports additional context and control that make it easier for your users to help protect themselves.

Read the documentation to learn how to set up time-based OTP for Azure AD B2C.
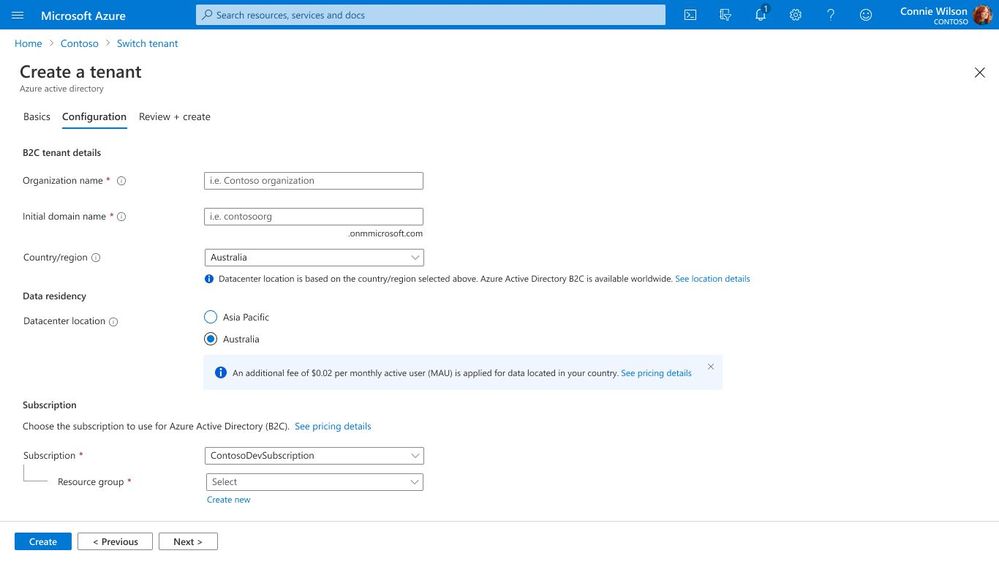
Data residency pricing update
We understand how important it is for our customers to have control over their data and to comply with local data residency requirements. As a first step in supporting this business-critical need, earlier this year we announced the general availability of Azure AD B2C data residency in Australia. To support increased demand for this support, beginning mid-2022, current and new customers who have data residency configured for Australia or other specific countries/regions will incur an add-on charge of $0.02 per monthly active user (MAU).
Based on your feedback, we are continuing to grow our data residency offerings so that you can target selection of the country/region needed to meet data storage requirements.
We love hearing from you, so please share your feedback on these updates through the Azure forum or by tagging @AzureAD on Twitter.
Robin Goldstein
Twitter: @RobinGo_MS
Learn more about Microsoft identity:
[ad_2]
Source link