[ad_1]
Howdy folks!
With the growing trend of more applications and services moving to the cloud, there’s an increasing need to improve the governance of identities used by these workloads. Today, we’re announcing the public preview of access reviews for service principals in Azure AD. Many of you are already using Azure AD access reviews for governing the access of your user accounts and have expressed the desire for extending this capability to your service principals and applications.
With this public preview, you can require a review of service principals and applications that are assigned to privileged directory roles in Azure AD. In addition, you can also create reviews of roles in your Azure subscriptions to which a service principal is assigned. This ensures a periodic check to make sure that service principals are only assigned to roles they need and helps you improve the security posture of your environment.
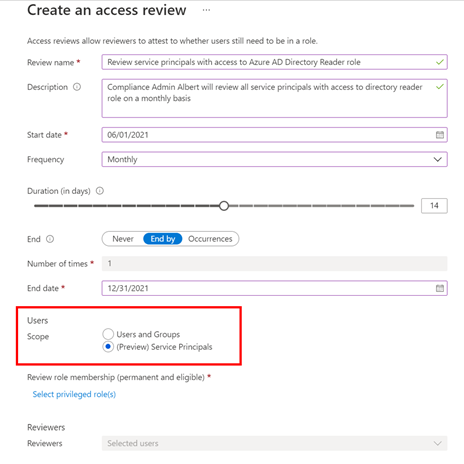
Setting up an access review for service principals in your tenant or Azure subscriptions is easy -select “service principals” during the access review creation experience, and the rest is the same as any other access review!
To set up this new Azure AD capability in the Azure portal:
- Navigate to Identity Governance.
- Choose Azure AD roles or Azure resources followed by the resource name.
- Locate the Access Reviews blade to create a new access review.
- Set the Scope to Service Principals.
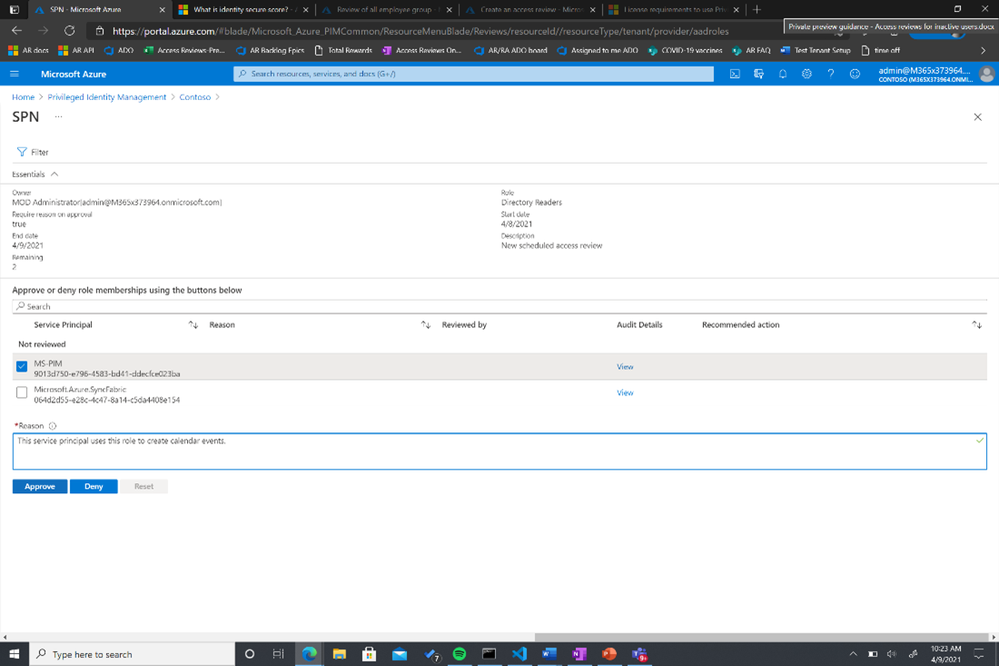
The selected reviewers will receive an email directing them to review access from the Azure portal.
You can also use MS Graph APIs and ARM (Azure Resource Manager) APIs to create this access review for Azure AD roles and Azure AD resource roles, respectively. To learn more about this feature, visit our documentation on reviewing Azure AD roles and assigning Azure resource roles.
As we work on the expanding the set of identity capabilities for workloads, we will use this preview to collect customer feedback for identifying the optimal way of making these capabilities commercially available.
Learn more about Microsoft identity:
Source link