[ad_1]
Howdy folks,
I’m excited to share the latest Active Azure Directory capabilities that will streamline your hybrid identity, monitoring, and B2B user experiences. These updates help you achieve a more unified identity management from a single control plane and enrich experiences to help provide seamless and secure collaboration with guest users.
Unified identity management
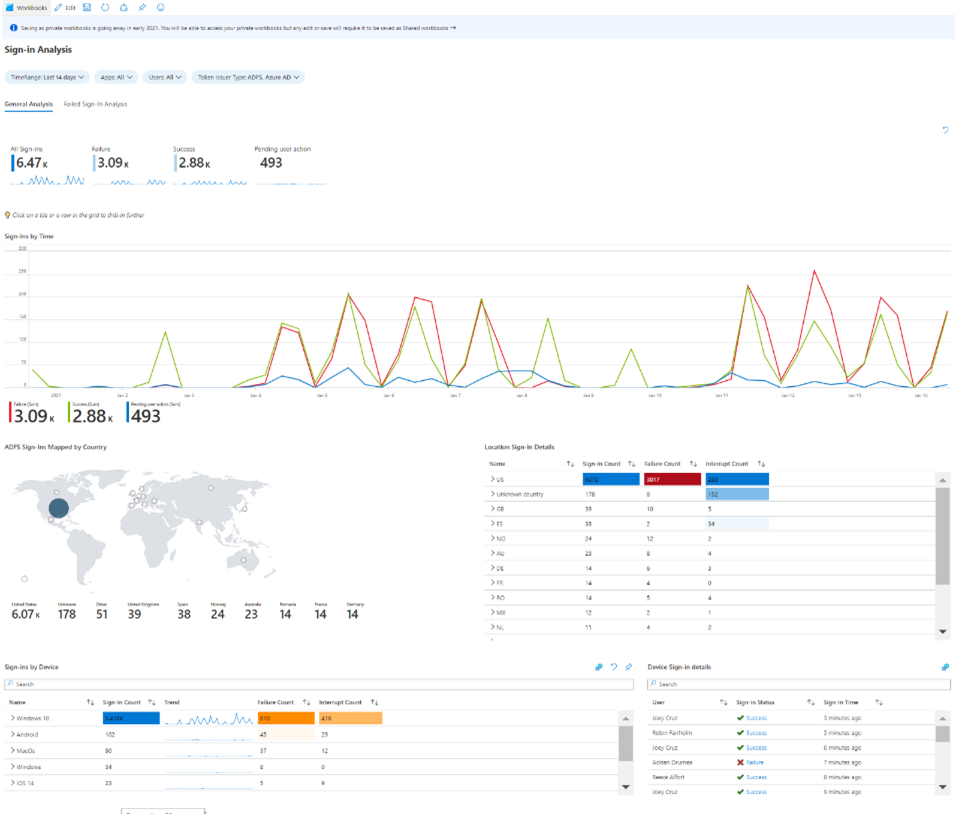
- Public preview of AD FS sign-ins in Azure AD reporting – AD FS sign-ins can now be added to Azure AD activity reporting, giving organizations a unified view of their hybrid identity infrastructure and helping them along their identity modernization journey. This sign-in activity appears in the “Federated” column of Azure AD sign-in reports for customers using the latest version of Azure AD Connect Health. Customers can stream this activity and analyze in their own SIEM tools like Azure Sentinel, or they can use the Azure AD integration with Azure Monitor and Log Analytics to unlock insights and build dashboarding within the Azure portal. Log Analytics now has a stream called “ADFS SignIns”, which contains the same schema as the sign-in data in the logs, and Azure Monitor has a new pre-built “Sign-In Report” workbook.
- General availability of tenant creation activity in Azure AD audit logs – Whenever a user creates a new Azure AD tenant, that activity is now recorded in the Azure AD audit logs of the tenant the user was signed into with the Azure portal, not just the logs of the newly created tenant. The log activity includes the new tenant ID, the UPN and Object ID of the user that created the tenant, and the tenant creation time and date. Admins can use this to more effectively monitor their entire organization and better maintain an inventory of all their tenants.
Azure Monitor workbook for Azure AD and AD FS sign-in reporting
External Identities
- Email one-time passcode for B2B collaboration in Arlington/Government Cloud – Organizations in the Microsoft Azure Government cloud can now enable guests to redeem invitations with email one-time passcode (email OTP). Guest users can still collaborate with partners in the Azure Government cloud by requesting and entering a temporary code to sign-in to shared resources.
As always, we’d love to hear your feedback or suggestions in the comments or on Twitter (@AzureAD).
Alex Simons (@Alex_A_Simons)
Corporate VP of Program Management
Microsoft Identity Division
Learn more about Microsoft identity:
[ad_2]
Source link