
[ad_1]
In our previous blog, we introduced Microsoft’s identity-centric security service edge (SSE) solution and two new services: Microsoft Entra Private Access and Microsoft Entra Internet Access. This blog continues the series around Microsoft’s new SSE solution, where we’ll take a deeper look into the Microsoft Entra Internet Access, currently in public preview for Microsoft 365 scenarios, and soon-to-be available in public preview for all internet traffic.
As digital transformation and the rise of hybrid work drive broad adoption of modern software-as-a-service (SaaS) applications, and work-from-anywhere arrangements, organizations increasingly need to protect their environments against the threats of open internet. Traditional network security tools just don’t scale to the needs of modern work and lack the protections against the emerging sophisticated attack patterns.
Microsoft Entra Internet Access
Microsoft Entra Internet Access is an identity-centric Secure Web Gateway (SWG) for SaaS apps and internet traffic that protects against malicious internet traffic, unsafe or non-compliant content, and other threats from the open internet. Working alongside Microsoft Entra Private Access and the rest of Microsoft Entra identity stack it unifies your access policies across all internet resources and SaaS apps, including Microsoft 365 with Microsoft Entra Conditional Access.
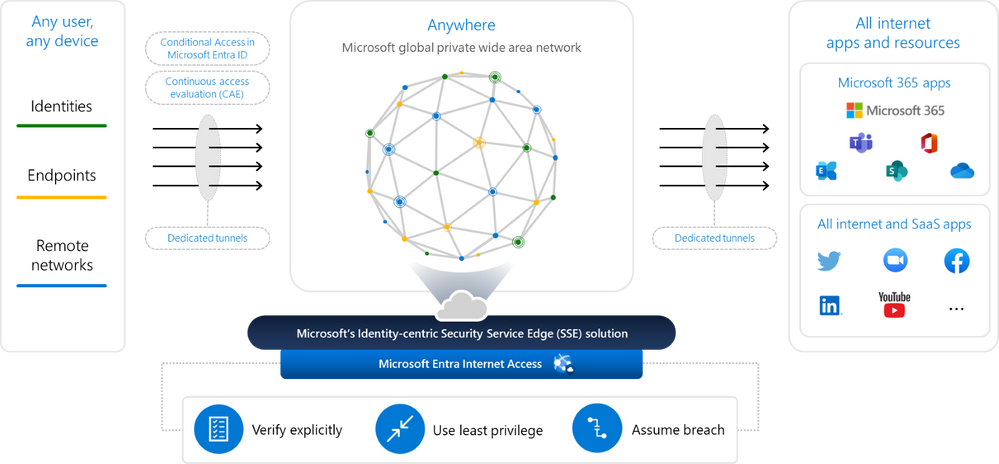
Security Professionals can use Internet Access to extend adaptive, granular access controls for any remote user, device endpoint, or branch network as they connect to any internet destination and SaaS app without these destinations requiring native federation with identity providers. Internet Access simplifies and modernizes traditional network security to protect users, apps, and resources with advanced capabilities across web filtering, cross-tenant protection, data loss prevention, and deep packet inspection. Plus, it offers best-in-class security and optimized access for Microsoft 365 apps.
What makes Microsoft Entra Internet Access unique
Seamless integration with identity-centric access controls: Our deep integration with Microsoft Entra ID enables Conditional Access to be extended to any external destination, internet resource, and cloud application, even if they’re not integrated or federated with Microsoft Entra ID. Soon this will include continuous access evaluation that can instantaneously revoke access if conditions change, for example if an identity attack was detected. This integration with Conditional Access enables you to leverage granular device, user, location, and risk conditions while applying various SWG, CASB, and Firewall policies to model contextual security requirements of their enterprise. Last but certainly not least, we bring in new network conditions to extend Conditional Access policies for your SaaS apps.
Best-in-class performance and resiliency: Our globally distributed proxy, powered by Microsoft’s private wide-area network, Microsoft global network, with Points of Presence (PoPs) closest to the user eliminates extra hops to optimize traffic routing to apps and resources, giving them a fast, consistent hybrid work experience. You can now connect your remote workers and branch offices seamlessly through our global secure edge that’s only milliseconds away from the users’ location. This helps avoid traffic hairpins and single point of failures for egress/ingress to and from the internet.
Enhanced security and visibility for Microsoft 365 applications: We offer a host of unique security and visibility provisions for Microsoft 365. Our data path security provisions for Microsoft 365 include – granular adaptive access controls as well as protection against token theft and data exfiltration. We also provide enhanced visibility of security sensitive activities through near-real time logs enriched with user, device, and location metadata for advanced threat correlation.
Side-by-side support with 3rd party SSE solutions: Microsoft Entra Internet Access can be deployed as a main solution to protect access to all internet resources, SaaS, and Microsoft 365 destinations or side-by-side with other SSE solutions. So, you can choose to rely on Microsoft Entra Internet Access for the unique security and visibility capabilities for Microsoft 365, while keeping all your other internet traffic and SaaS apps protected by another SSE solution of your choice. Traffic can be acquired using either a client-based approach from end user devices or by running IPsec tunnels from remote networks. You can easily enable secure access to Microsoft 365 traffic throughout-of-box profiles in Microsoft Entra admin center.
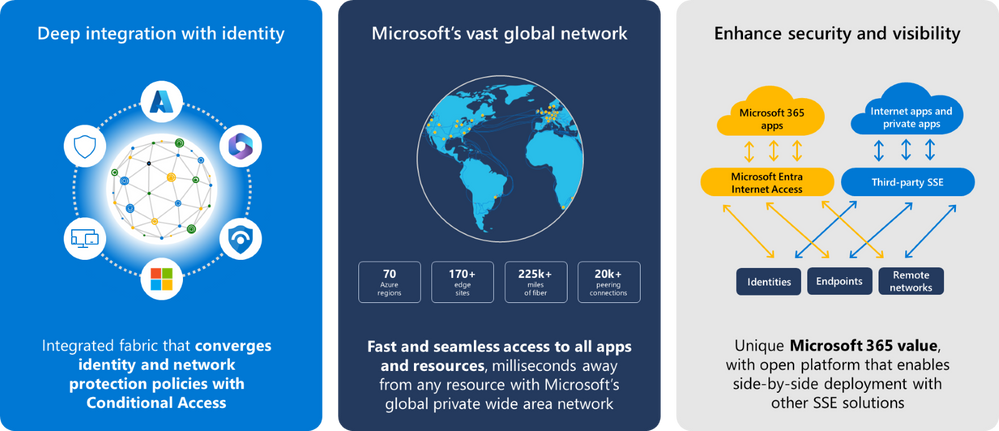
Internet Access key capabilities
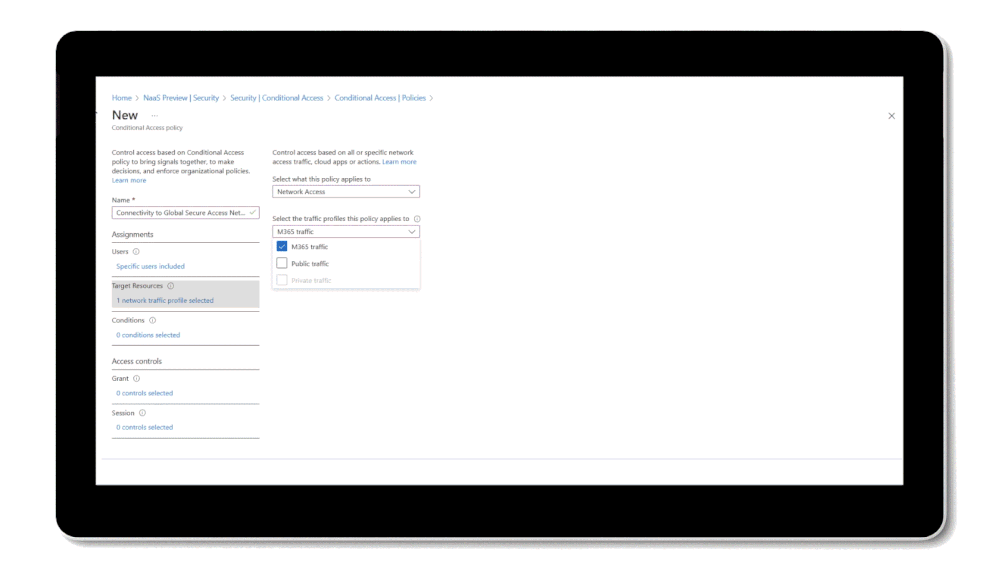
Extend Conditional Access universally to all Internet endpoints: Control access to all Internet destinations leveraging Microsoft Entra Conditional Access policies. The convergence between identity and network access policies helps eliminate the gaps in defenses and strengthen organizational security posture. By managing all access policies in one place, you can now then extend adaptive access controls universally to rely on Conditional Access and, soon also on continuous access evaluation to any network destination like an external website, or non-federated SaaS applications – without the need to change these applications.
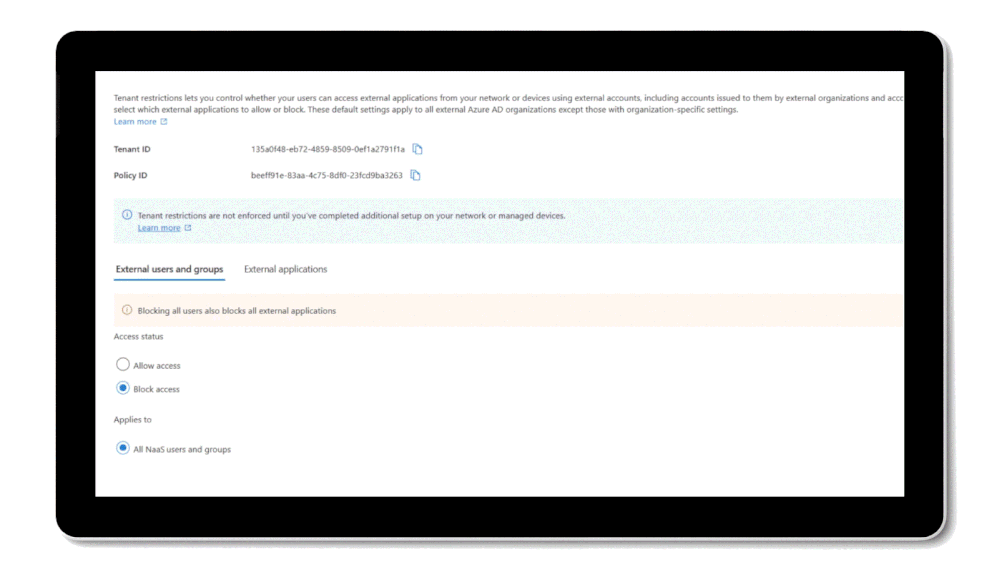
Protect against data exfiltration: Tenant Restriction v2 is a strong data exfiltration control enabling you to manage external access risks from your managed devices and networks by curating a granular allow or deny list of foreign identities and applications that can or cannot be accessed. Internet Access enables you to enforce tenant restriction signal universally across all OS and browser platforms, without the need for corporate proxy, reducing overhead and providing more flexible, granular controls.
Protect against token theft and prevent users from bypassing the secure network edge: Internet Access introduces Compliant Network as an integrated and easy-to-manage construct within Conditional Access. With this control, you can protect Microsoft Entra-integrated cloud applications against token theft and ensure users do not bypass network security policies specific to their tenant while accessing critical cloud services. It’s also enforced in data paths using continuous access evaluation to instantly deny access to Microsoft 365 apps and resources in case of detected token theft. In our SSE model, user productivity is improved compared to traditional network security approaches, since the Compliant Network check allows remote users to be verified without having to hairpin them from a handful of egress locations.
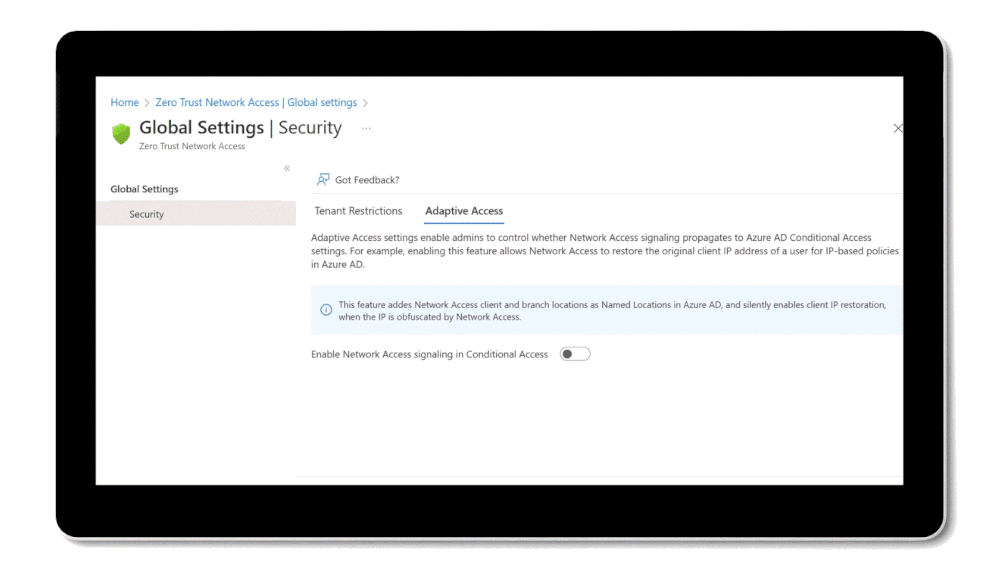
Restore original user source IP context for all traffic: Typical proxies obfuscate users’ original source IP, breaking location policies in Conditional Access as well as impact the accuracy of risk detections and activity logs. Microsoft Entra Internet Access offers differentiated backward compatibility of your trusted location checks in Conditional Access and continuous access evaluation, Identity risk detection and logging, by ensuring the users’ original source IP is maintained.

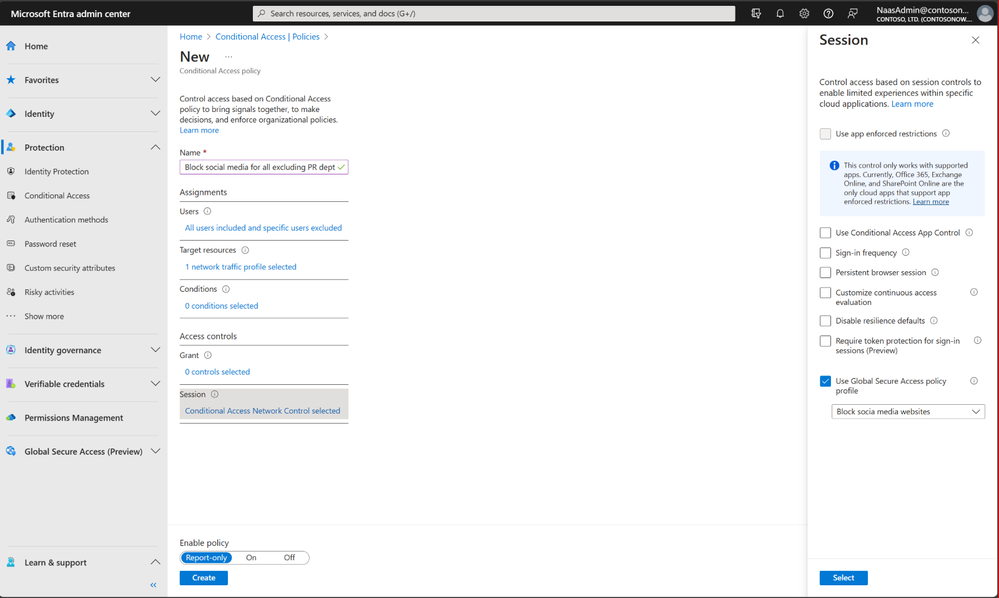
Unify network access controls with Conditional Access to extend granular Conditional Access policies to your SWG policies. This means that you can now apply network security policies on any internet destination based on the rich conditions available in Conditional Access, including user, device, location, and risk constructs.
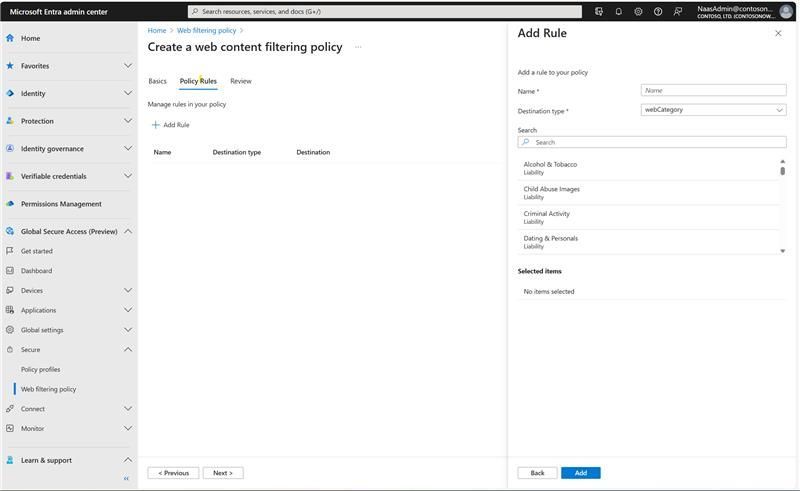
Restrict end user access to unsafe and non-compliant content with web content filtering (URL, FQDN, web category) and make internet filtering policies more succinct, readable, and comprehensive, by leveraging the rich user, device, and location awareness of Conditional Access. Helping to reduce the attack surface and simplify the administrative experience for network security.
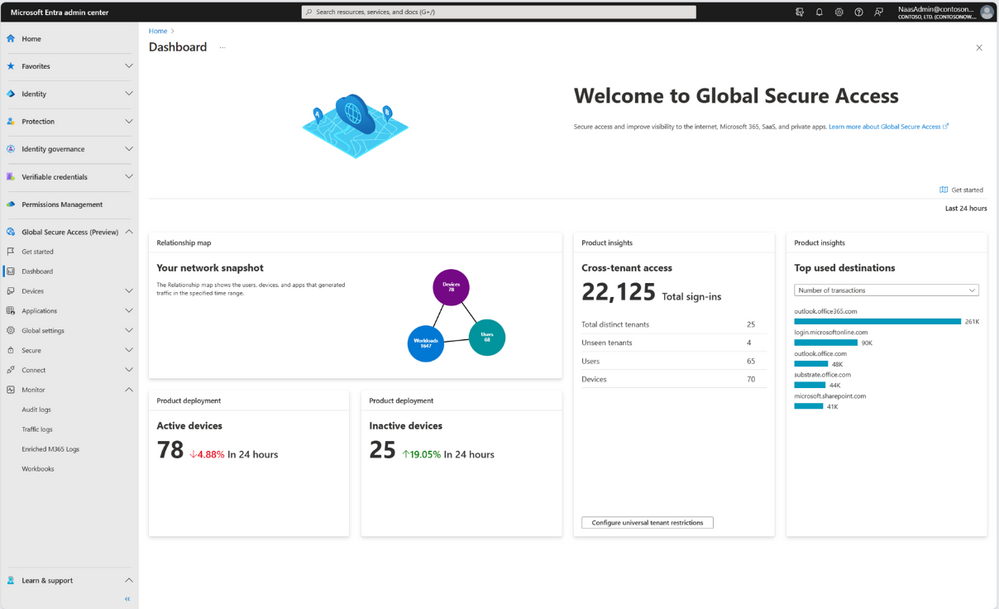
Attain deep insights and network analytics using in-product dashboards: Our insightful in-product reports and dashboards make it easy to digest and share a holistic view of your entire environment with your organization. You can look at deployment status, detect new risks, and quickly remediate issues. Our dashboard provides a snapshot of the users, devices, and destinations connected through Microsoft’s SSE solution. We show cross-tenant access undergoing in your enterprise, as well as top network destinations in use. Early next year, we’ll provide enhanced policy insights and recommendations and offer advanced app and network discovery capabilities.
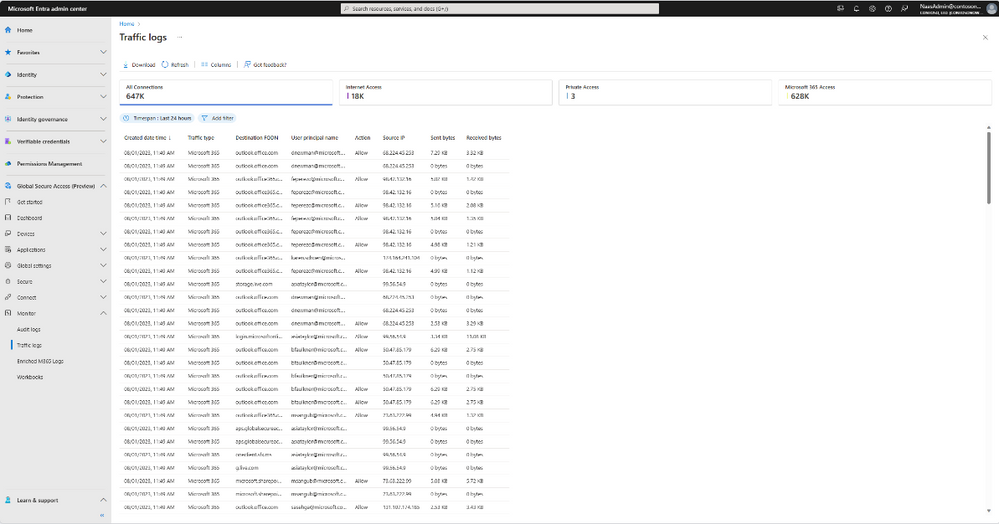
Create custom views and dashboards based on rich insights into network logs: On our traffic logs page, you can visualize every request and response transaction happening through Microsoft’s SSE solution. In these logs, you can also view valuable information collected from the device, like device ID and operating system name and version. You can also see relevant packet information like source IP and port, destination IP and port, and FQDN.
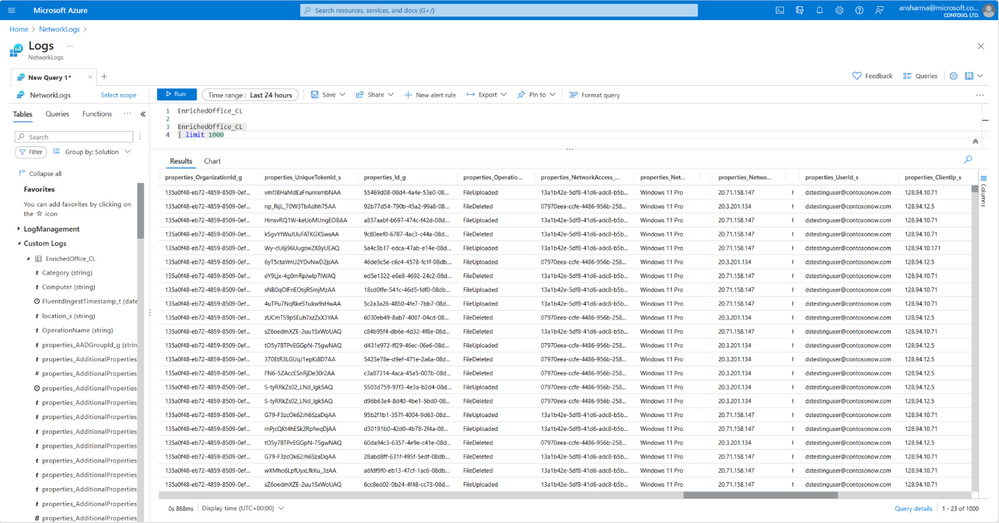
Enriched real-time visibility for Microsoft 365 security events: Facilitate easy and fast threat detection for Microsoft 365 apps and resources through enriched logs. Internet Access solution extends the Microsoft 365 log schema with rich user, location, and device context while providing near real-time SLAs without the need to break and inspect the traffic.
Upcoming capabilities are in advanced development and will be released early next year:
- Restrict outgoing and incoming traffic based on IP addresses, port, and protocol using granular policy conditions leveraging context aware cloud firewall.
- Identify and block malicious network activity with Intrusion Detection and Protection System (IDPS) and threat intelligence to target known malicious IPs/FQDNs/URLs.
- Inspect encrypted traffic with granular TLS inspection across all TCP/UDP traffic.
Getting started with Entra Internet Access
Global Secure Access (preview) is the centralized location in the Microsoft Entra admin center where you can configure and manage Microsoft Entra Internet Access. Internet Access isolates the traffic for Microsoft 365 applications and resources, such as Exchange Online and SharePoint Online. Users can access these resources by connecting to the Global Secure Access Client or through a remote network, such as in a branch office location. The most current version of the client can be downloaded from the Microsoft Entra admin center. You can install the client interactively, silently with the /quiet switch, or use mobile device management platforms like Microsoft Intune to deploy it to their devices.
To learn about different use cases and scenarios, configuration prerequisites and how to enable secure access to your Microsoft 365 apps and resources go to the Global Secure Access documentation page.
You can learn more about Internet Access in action via our on-demand Tech Accelerator product deep dive sessions.
Learn more about Microsoft’s SSE solution:
Get started with previews
Learn more about Microsoft Entra:
[ad_2]
Source link




