
[ad_1]
At our latest Microsoft Ignite event, we announced and demonstrated new capabilities within Microsoft Entra Internet Access, an identity-centric Secure Web Gateway (SWG) solution capable of converging all enterprise access governance in one place. These capabilities unify identity and network access controls to help eliminate the security loopholes and manageability created by using multiple security solutions. This helps protect enterprises against malicious internet traffic and other threats from the open internet.
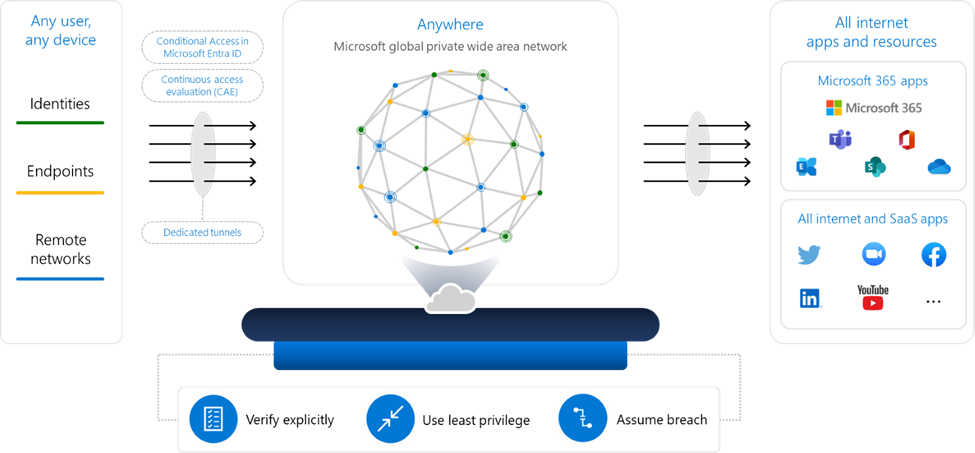
In this blog, we highlight the advantages of Entra Internet Access’ web content filtering capabilities that work across all web-based internet resources and SaaS applications by leveraging the unified policy engine: Entra ID Conditional Access.
Extend Conditional Access policies to the internet
Microsoft Entra Internet Access extends the contextual sophistication of Conditional Access policies to enterprise SWG filtering. This enables you to apply granular web filtering for any internet destination based on user, device, location, and risk conditions. The ability to apply different filtering policies (and in the future, threat protection policies, DLP policies, and more) based on various contexts and conditions is critical to address the complex demands of today’s enterprise. Bringing identity and network context together to enforce granular policy through Conditional Access is what makes Microsoft Entra Internet Access the first identity-centric SWG solution.
Filter web content to reduce attack surface
Microsoft Entra Internet Access offers extensive web content filtering to prevent access to unwanted web content for enterprise users, using our client connectivity model, available for both Windows and Android platforms. We’ll soon add support for other OS platforms and branch connectivity.
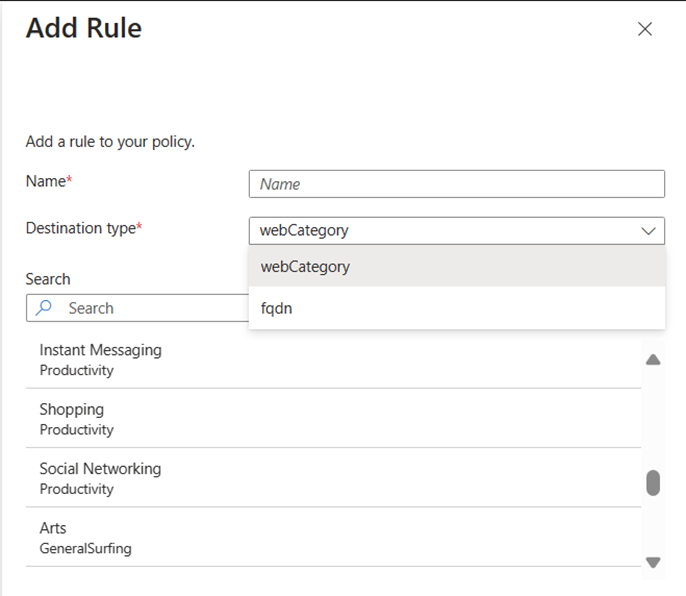
For example, with web category filtering, you can create policies using an extensive repository of web content categorization to easily allow or block internet endpoints across categories. Category examples include liability, high bandwidth, business use, productivity loss, general surfing, and security, which includes malware, compromised sites, spam sites, and more.
To provide even more granular application layer access control, you can create policies with fully qualified domain name (FQDN) filtering to identify specific endpoints to allow or block through standalone policy configuration or add exceptions to web category policies with ease.
With Microsoft Entra Internet Access, internet filtering policies are more succinct, readable, and comprehensive, helping to reduce the attack surface and simplifying the administrative experience.
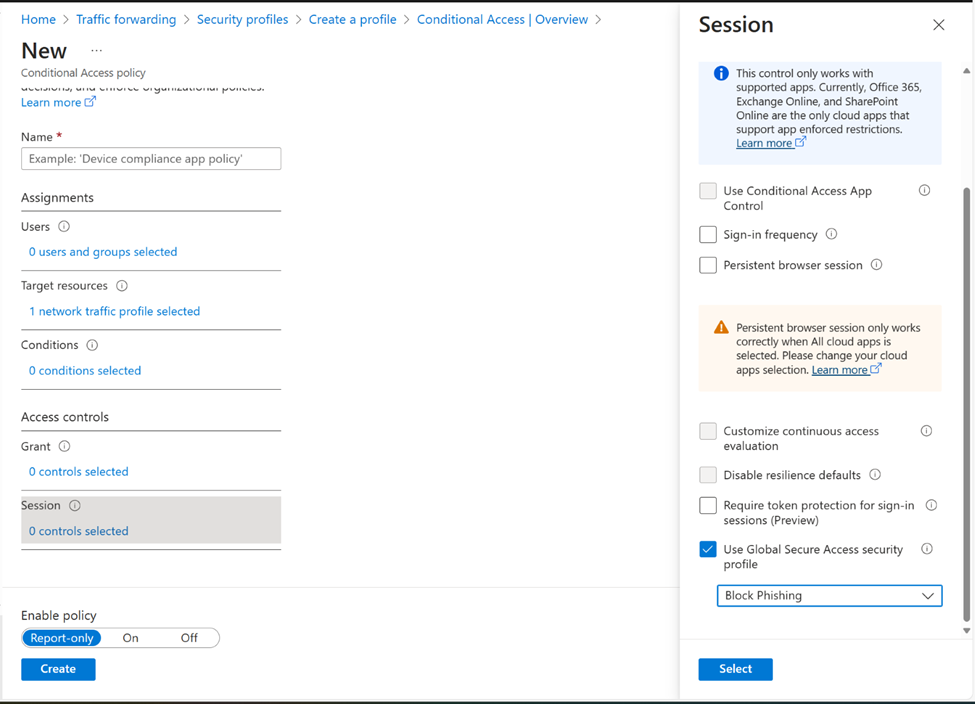
Proactively set conditional security profiles
Security profiles make it easy to create logical groupings of your web content filtering policies (and in the future, treat protection policies, DLP policies, and more) and assign them to Conditional Access policies. Additionally, security profiles can also be organized with priority ordering, allowing imperative control over which users are affected by web content filtering policies.
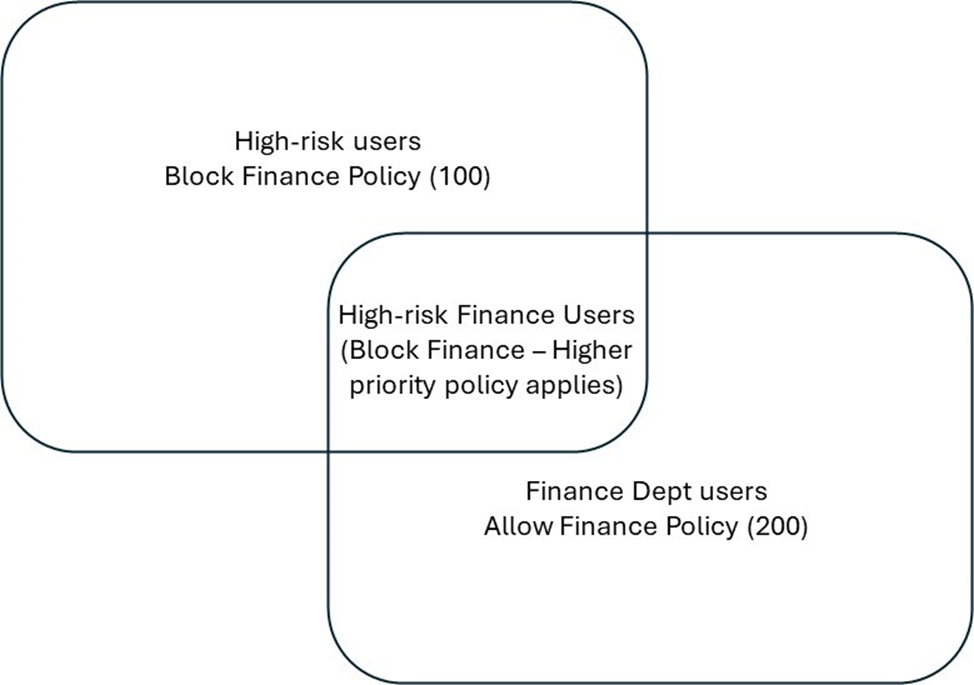
Here’s how that works. Let’s say only your finance department should have access to finance applications. You can add a block finance web category policy to your baseline profile (priority 65000) which is applied to all users. For the finance department, you can create a security profile (priority 200) that allows the finance web category and attach it to a Conditional Access policy enforced to the finance group. Because the security profile for allow finance is a higher priority than the baseline profile, the finance department will have access to finance apps. However, if a finance department user risk is high then their access should be denied. So, we create an additional security profile at a higher priority (priority 100) that blocks the finance web category and attach it to a Conditional Access policy enforced to users with high user risk.
Conclusion
Our 2023 Ignite release reflects Microsoft’s desire to make your job easier by offering you a fully integrated security service edge (SSE) solution, including SWG, Transport Layer Security (TLS) inspection, Cloud Firewall, Network Data Loss Prevention (DLP) and Microsoft Threat Protection capabilities. This is the first of many incremental milestones on our journey to help you protect your enterprise and your people.
Start testing Microsoft Entra Internet Access Public Preview capabilities and stay tuned for more updates on Internet Access–to be released soon.
Anupma Sharma
Principal Group Product Manager, Microsoft
Learn more about Microsoft Entra:
[ad_2]
Source link




