[ad_1]
Howdy folks!
At Microsoft Ignite 2021, we shared how Microsoft has been collaborating with the cybersecurity community to defend against intensifying identity attacks. In this blog post, I‘ll dive deeper into the identity security features announced for Azure Active Directory (AD) identity protection and Conditional Access. These identity security features:
- Provide visibility into emerging threats (token theft detections in identity protection)
- Enable near real-time protection (Continuous Access evaluation)
- Extend protection to workload identities (Conditional Access for workload identities)
Detecting emerging attack vectors: token theft detections
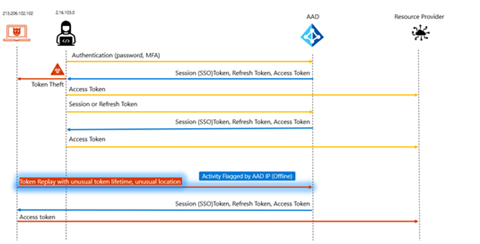
Bad actors increasingly use token theft and replay to gain ongoing access to victim resources and elevated access to existing multifactor authentication claims. We have primarily seen token theft occur via malware and Machine-In-The-Middle (MITM) phishing attacks. Once the bad actor has stolen a token from an identity (like a user or app), they can use it to impersonate identity and steal data.

At Ignite, we announced the general availability of two new detections that can alert admins to token replay: anomalous token and unfamiliar sign-in properties for session cookies. These new detections look for anomalies in the token claims, token age, and other authentication attributes. First, you need to block users’ access until you can revoke users’ active tokens, assess how the tokens were stolen, and remove malware if present. We then recommend revoking active tokens with Revoke-AzureADUserAllRefreshToken PowerShell cmdlet.

In addition to detection and prevention for token replay, we’re developing features to detect and respond to token theft. Our next detection, token issuer anomaly, is a first step in identifying a compromised on-premises SAML identity provider that enables attackers to mint tokens. If you conclude there’s been an attack after investigating this detection, we recommend doing the following:
Near real-time enforcement: Continuous Access evaluation
The new detection capabilities help detect maliciously played sessions and refresh tokens. However, authentication protocols only check tokens when they refresh (typically every hour or so for access tokens). That means that detecting changes in user or policy conditions lag for as long as the time of the refresh interval. Continuous Access evaluation (CAE) is a mechanism which lets Azure AD maintain a dialogue with the app to close that gap. CAE enables us to revoke access in real-time when changes in conditions trigger risks, such as when a user is terminated or moves to an untrusted location or user risk is detected.
For example, you can enable CAE and configure the Conditional Access policy to block non-trusted IP ranges or malware infected devices. Once enabled, a token stolen from an infected device in your trusted IP ranges will be rejected if it’s replayed outside the trusted ranges because malicious intent is assumed. Even before this happens, tokens can be invalidated when the malware that is stealing the tokens is detected. CAE and identity protection work together to block token replay outside the conditions you define—detecting and automatically remediating token replay when attempted. CAE will be Generally Available by the end of 2021. After that, CAE will be enabled by default if you have not configured any CAE settings (if you have configured something, your setting will be honored). Until then, you can change CAE settings under Conditional Access.
Extending coverage further: Conditional Access for workload identities
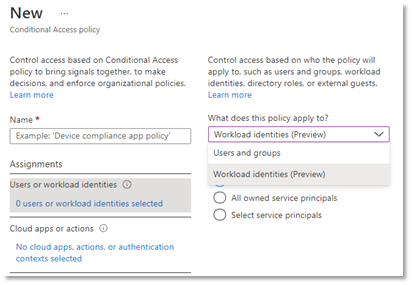
Sophisticated, orchestrated, multi-vector attacks are increasing. This makes a Zero Trust strategy imperative for every business and organization. At the heart of Zero Trust is Azure AD Conditional Access, which verifies explicitly on every identity. Besides protecting human identities, we’re extending Conditional Access capabilities to cover app-only authentications from workload identities, such as apps and service principals. Securing workload identities in your environment is critical to prevent bad actors from compromising and using these identities to access your environment.
Conditional Access for workload identities enables admins to prevent unauthorized use of service principals by blocking authentications from outside trusted networks. Conditional Access for workload identities is now in Public Preview.
We hope you enjoyed Microsoft Ignite 2021. If you have questions or comments, please reach out—we would love to hear your feedback!
Learn more about Microsoft identity:
Source link




