[ad_1]
Hi everyone,
I’m Sue, the VP of Identity’s Customer & Partner Success team, and I love having the opportunity to share stories from real customers via this blog series. We’ve designed this collection of stories from real customers that have been able to solve their identity and security challenges using Microsoft Azure Active Directory (Azure AD), part of Microsoft Entra. I hope you find valuable insights and best practices that you can apply to your own projects.
Check out more from the blog series here: Voice of the Customer
In today’s spotlight, we’ll be focusing on the journey of one of our largest partners, Accenture, as they adopted passwordless authentication and reduced their exposure to phishing attacks.
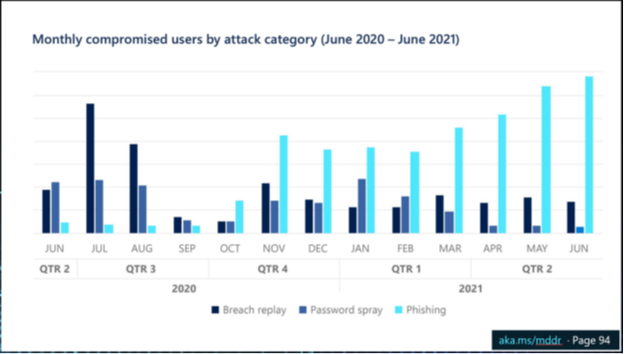
With the rise of cyber-attacks, phishing is among the primary methods that attackers use to compromise your organization’s users. In Microsoft’s latest Digital Defense report, we see it as the highest attack vector on users’ credentials.
Passwords have long been a weak credential and now attackers are increasing their focus on getting your users to just surrender the clear text password to them. As Simon Gooch, Accenture’s Director for Global IT, Enterprise Technology and Security notes, “In the future, people will look back and wonder why we ever used passwords.”
Now, even though multifactor authentication (MFA) defeats over 90% of password breaches, it isn’t immune to phishing. Therefore, we see the recent emphasis on “phishing resistant” MFA methods in the Executive Order issued by the US president in 2021 to strengthen the nation’s cybersecurity. Microsoft’s vision for a passwordless world emphasizes FIDO 2.0-powered inherently phish-resistant credentials like Windows Hello for Business and FIDO 2.0 External Security Keys. For more on how FIDO 2.0 credentials are inherently phishing resistant, check out this blog by my colleague Pamela Dingle, our Director of Identity Standards, and this video explaining the technical flow. These modern credentials are not only more secure but they also create a more seamless and natural user experience. As Accenture notes, “We’ve proven the benefits. The adoption of passwordless has led to faster login times, more reliable experiences, fewer failed authentications, and improved overall security posture.”
The most impressive aspect for me throughout Accenture’s journey was the speed and efficiency with which it was executed. As we’ve shared in our passwordless journey blog, getting to passwordless means getting your apps ready, your devices ready, and your registration campaigns thought out. Accenture moved thousands of applications to Azure AD so that the passwordless sign ins would accrue to MFA login for all these apps without requiring any further devices or gestures beyond the user’s natural sign in. They emphasized readiness on multiple devices, as you’ll be able to use the right passwordless form (Windows Hello For Business, FIDO2 Keys, or Phone Sign in) that matches the user’s experiences.
The end result is over 500,000 users primarily using Windows Hello For Business, 200,000 Phone Sign in users, over 10,000 FIDO2 key users, and an 80% drop in day–to–day usage of passwords across the enterprise.
For an alternative perspective on the implementation, I’d like to draw your attention to the detailed passwordless journey blog authored by our partners at Accenture. I trust you will agree with Accenture’s dual goals of improving security and the user experience.
Until next time,
Sue
Learn more about Microsoft identity:
Source link