[ad_1]
Howdy folks,
I’m excited to share the latest Active Azure Directory provisioning capabilities to help you with your user lifecycle and directory management needs.
Automate provisioning users from Azure AD into on-premises applications
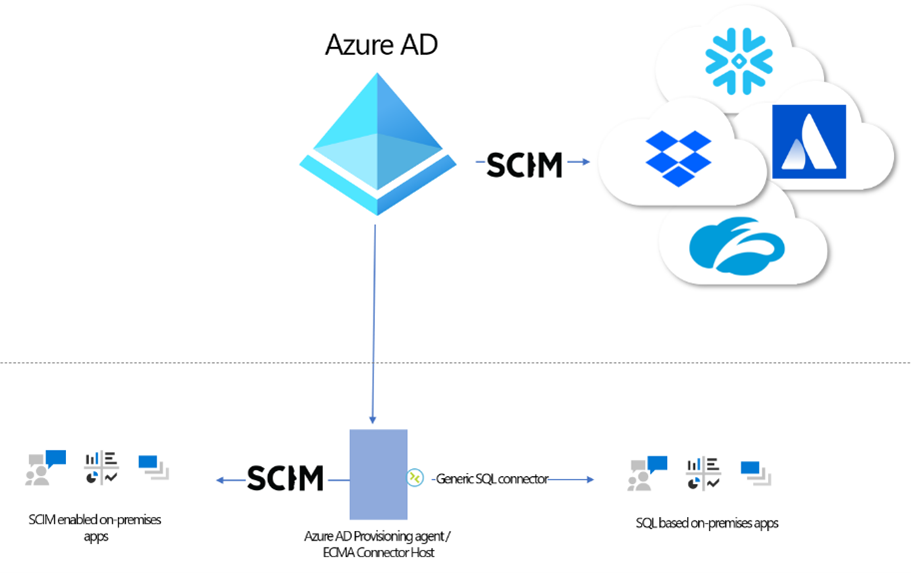
Azure AD now supports provisioning into on-premises applications, and we have a preview that we’re excited for you to deploy and share your feedback.
You must have an Azure AD Premium P1 or P2 tenant and an on-premises application that uses SQL as a data store or supports SCIM. You can request an invitation to the preview here. We plan to remove the invitation requirement in the coming months and add support for provisioning users into LDAP directories (excluding AD DS).
For those customers who have previously deployed Microsoft Identity Manager (MIM), you can reuse your existing connectors and configuration without needing a full MIM deployment. And for those customers building new applications, you can use our SCIM reference code to stand up a SCIM endpoint and easily provision users into your application, whether it’s on-premises or in the cloud.
More apps with pre-built user provisioning connectors
Azure AD service now supports more than 200 provisioning connectors! Checkout the growing list of applications here. Don’t see an app you’re looking for? Request your application vendors to support the SCIM standard and onboard to the Azure AD application gallery. We’ll work with the ISV to quickly onboard.
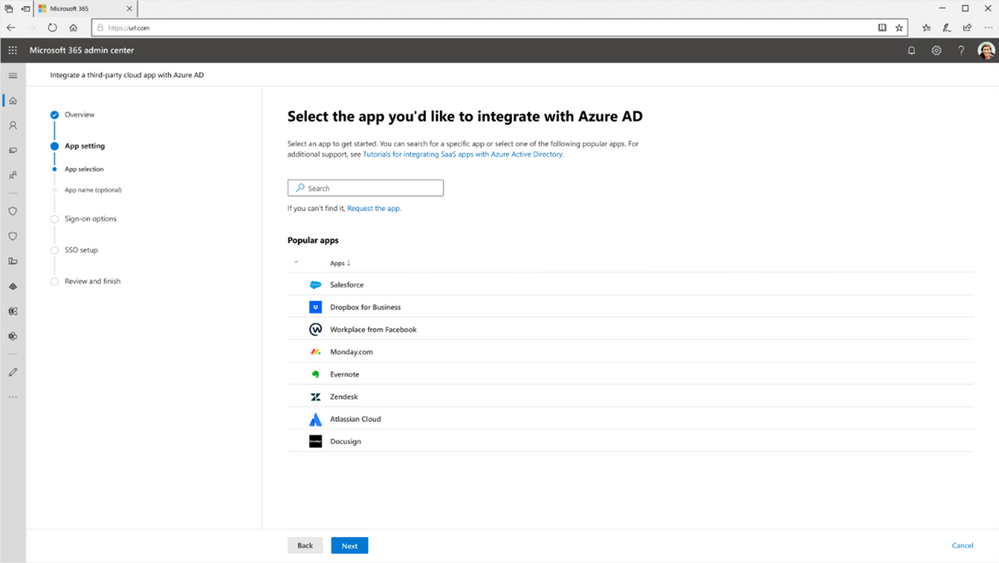
New app integration wizard available in the Microsoft 365 admin center
To help more admins connect third party apps to Azure AD, we’ve launched a new app integration wizard in the Microsoft 365 admin center. The app integration wizard makes it easier to connect apps in our app gallery to Azure AD by taking admins through a guided configuration experience in setting up single sign-on. Once applications have been setup for single sign-on, admins can then automate user provisioning using the hundreds of pre-built provisioning connectors.
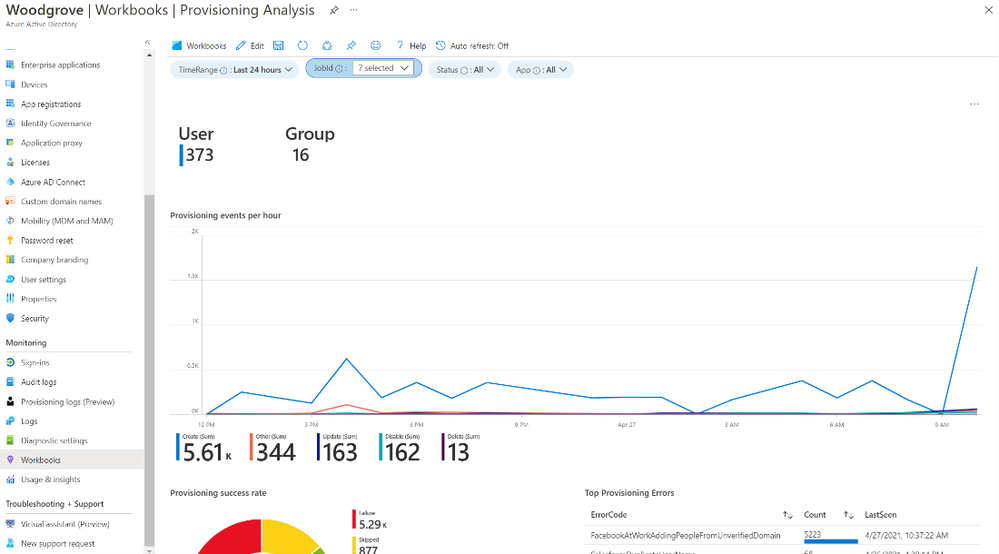
Provisioning logs are now generally available
Monitor and troubleshoot your provisioning deployment with the provisioning logs using the UI, API, or by exporting the data as a CSV. You can also build custom dashboards, alerts, and queries on the data using our Azure Monitor integration.
Simplify building and testing expressions
Azure AD’s provisioning service allows you to transform data prior to exporting it into a target system. In order to make it easier to build and test the expressions used to transform data, we’ve built an expression builder that is now available in public preview. Learn more about it here, or visit our tips for general guidance on writing expressions.
HR-driven provision updates for international assignments, gig economy workers, and cross-domain manager references
- In large multi-national corporations, employees may temporarily work in international locations and return to their home base after the assignment is over. Typically HR creates a new user profile corresponding to this assignment, so we have updated our user provisioning integrations with Workday and SuccessFactors to support retrieval of international assignment data.
- In today’s gig economy, we see a rise in conversion scenarios, wherein a full-time worker converts to a contingent worker or vice versa. When this happens, HR teams that use Workday deactivates the previous employment record and creates a new employment record that usually retains the previous employee ID. Classically, handling this scenario required manual intervention or creation of two separate Workday provisioning jobs to process full-time employees and contingent workers. With a recent update to our Workday integration, you can seamlessly handle this scenario so that the active employment record in Workday always takes over the ownership of the corresponding identity.
- If you are integrating HR provisioning with multiple on-premises Active Directory (AD) domains, you may come across scenarios where the user is part of one AD domain and the user’s manager is part of another AD domain. Such cross-domain manager references can now be resolved with a recent update and you can also search for duplicate UPNs / samAccountName values across multiple domains. Learn more in our cloud HR planning guide.
A new version of Azure AD Connect sync is available
The latest version of Azure AD Connect sync has added the following capabilities:
- Now supporting Selective Password hash Synchronization
- A new Single Object Sync cmdlet helps you troubleshoot your Azure AD Connect sync configuration
- Default to the V2 endpoint, which provides improved performance and allows for syncing of groups with more than 50,000 members.
- A new built-in role, the Hybrid Identity Administrator, can be used for admins that are responsible for configuring the service.
Azure AD Connect cloud sync updated agent
With agent version # 1.1.359, Azure AD Connect cloud sync admins can now use GMSA cmdlets to set and reset their gMSA permission at a granular level. In addition, the limit of syncing members using group scope filtering has increased to 50,000 members. For more details on agent updates, including bug fixes, check out the version history.
As always, we’d love to hear your feedback or suggestions in the comments or on Twitter (@AzureAD).
Best regards,
Alex Simons (@Alex_A_Simons)
Corporate VP of Program Management
Microsoft Identity Division
Learn more about Microsoft identity:
[ad_2]
Source link