[ad_1]
Today we’re excited to announce the public preview of filters for apps! Filters for apps provides a new way to manage Conditional Access (CA) assignment for apps and workload identities at scale.
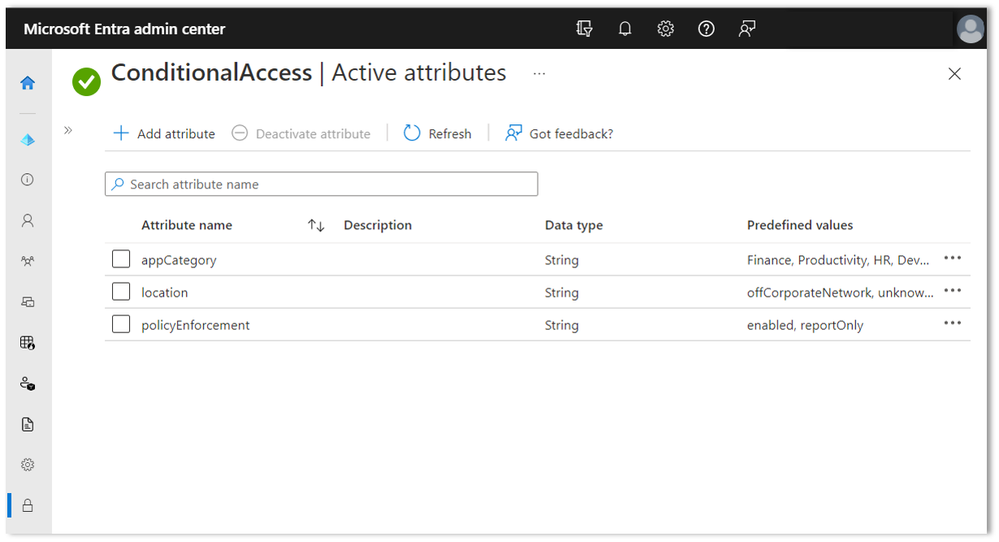
Protecting all apps is key to achieving a Zero Trust security posture. Currently, policies explicitly list apps. With filters for apps, admins can tag applications with custom security attributes and apply Conditional Access policies based on those tags, rather than individually selecting apps. With this approach there is no limit on the number of apps covered, and new apps you add with the attributes are automatically included in the policies! Attribute assignment builds on top of custom security attributes, delivering attribute customization and a rich delegation model.
“Legacy conditional access policies presented numerous challenges due to sizing limitations and management of policies. The advent of filters for apps allowed us to immediately reduce the number of Conditional Access Policies by half and allows us to easily view in one location which policies are applied to an application. Filters for Apps is efficient by allowing applications to be tagged quickly and easily and is much easier to manage via MS Graph APIs.”
– Large private preview customer
Filters for apps use the same expressions as Conditional Access filters for devices, providing a rich and familiar experience.
Filter for Cloud app assignments
Cloud app assignment supports filters for apps. You can configure filter expression rules that get evaluated when an app is accessed. When a new app is onboarded, you only need to tag it with an attribute to bring it into scope of the desired policy.
For example, you can create a custom security attribute to tag apps with an app category, like HR or Finance. Apps with one of these tags will then immediately have policy enforced.
Policy assignment using app attributes eliminates the chance of accidentally editing a policy when adding new apps, because only the app is updated. Additionally, custom security attribute management can be delegated to specific users. An admin can be given permission to tag apps with attributes without needing unnecessary policy management permissions. This further reduces the chance of policies being accidentally updated.
Filters for workload identity assignment
Attributes can also be applied to service principals and used with filters for apps. This is especially useful for organizations rolling out policy enforcement to hundreds or even thousands of service principals. One approach is to use custom security attributes to tag service principals authenticating from corporate network IP ranges. You can then create a policy that will block tagged service principals from authenticating from outside the corporate network.
Try the public preview
We’ve been working with our private preview customers – now it’s your turn to try it out and let us know what you think. Our aim is to help you more easily secure access to more of your apps and we look forward to hearing your feedback. One way to reach us is with the “Got feedback?” link on the Conditional Access policy view.
Conditional Access Filters for Apps
Learn more about Microsoft identity:
Source link