[ad_1]
Microsoft has released Security Updates (SUs) for vulnerabilities found in:
- Exchange Server 2013
- Exchange Server 2016
- Exchange Server 2019
SUs are available in a self-extracting auto-elevating .exe package, as well as the original update packages (.msp files), which can be downloaded from the Microsoft Update Catalog.
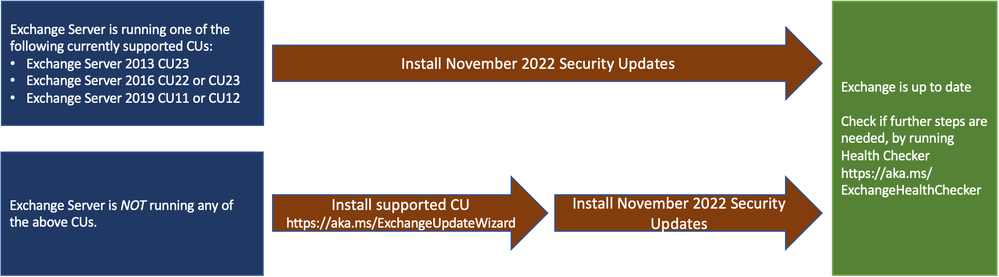
The November 2022 SUs are available for the following specific versions of Exchange Server:
Because we are aware of active exploits of related vulnerabilities (limited targeted attacks), our recommendation is to install these updates immediately to be protected against these attacks.
The November 2022 SUs contain fixes for the zero-day vulnerabilities reported publicly on September 29, 2022 (CVE-2022-41040 and CVE-2022-41082).
These vulnerabilities affect Exchange Server. Exchange Online customers are already protected from the vulnerabilities addressed in these SUs and do not need to take any action other than updating any Exchange servers in their environment.
More details about specific CVEs can be found in the Security Update Guide (filter on Exchange Server under Product Family).
The following update paths are available:
Known issues with this release
There are no known issues with this release.
Issues resolved by this release
- Delivery Report search from ECP might fail with IIS logs showing SEC_E_BAD_BINDINGS in a cross-site scenario after enabling Extended Protection
- Export-UMPrompt could fail with InvalidResponseException
We already applied mitigations for CVE-2022-41040 and CVE-2022-41082. Do we need to install this SU?
Mitigations are not actual code fixes of specific vulnerabilities. Please install the November 2022 (or later) SU on your Exchange servers to address CVE-2022-41040 and CVE-2022-41082.
Do we have to remove mitigation for CVE-2022-41040 after installing the November 2022 (or later) SU?
It is not necessary to remove mitigation already applied to your servers. Please note that if you are removing a mitigation, do it after Nov 2022 (or later) SU is installed and you have verified your server is fully up to date using the Health Checker script. To address different types of mitigations:
- Applied by EEMS – if mitigation is manually removed, it will be re-applied again until we update the mitigation XML file in our service. We will update the list of mitigations released as soon as we start excluding the security fixed Exchange Server builds for this particular mitigation. We will update when this is done.
- Applied manually – you could remove the mitigation manually by modifying IIS settings.
- Applied using the EOMTv2 script – you could remove the mitigation using .EOMTv2.ps1 -RollbackMitigation.
How does this SU relate to Extended Protection feature?
If you already enabled Extended Protection on your servers, install the SU as usual. If you did not enable Extended Protection yet, our recommendation is to enable it after installing November (or any later) SU. Running Health Checker script will always help you validate exactly what you might need to do after SU installation.
My organization is in Hybrid mode with Exchange Online. Do I need to do anything?
Exchange Online is already protected, but the November 2022 SU needs to be installed on your Exchange servers, even if they are used only for management purposes. You do not need to re-run the Hybrid Configuration Wizard after installing these updates.
Do I need to install the updates on ‘Exchange Management Tools only’ workstations?
Servers and workstations running only the management tools (no Exchange services) do not need these updates.
This post might receive future updates; they will be listed here (if available).
The Exchange Server Team
Source link