[ad_1]
2020-08-01 quick note: This blog post is resurrected from a January 2018 blog on the old blogs.technet.microsoft.com site (RIP), posted here with minimal edits.
If you do lots of Windows deployments, you likely create USB media fairly frequently. But if you are using Windows Information Protection (WIP), you could run into problems if that USB key is used on a Windows 10 device with WIP policies applied to automatically encrypt files based on their file type, you might find that your USB media no longer works – either it won’t boot, won’t run setup, generates odd errors (“access denied” is the one I’ve seen the most of), etc.
Obviously this happens when files on the USB media are encrypted – once that happens, they can’t be used on another machine or in Windows PE.
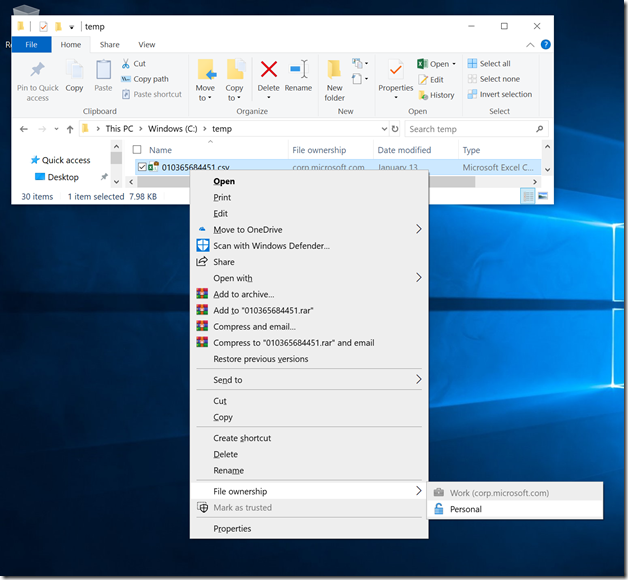
So, if you can’t convince your security team to leave your USB media alone, hopefully they at least let you override the files and change them to “personal” so that they are decrypted. That’s not too hard to do from File Explorer by right-clicking on one or more of the files and choosing “Personal” under “File ownership”:

But there’s no simple way to do this for lots of subfolders in File Explorer. Fortunately, there is a command-line tool that can help you out, and it’s really simple. Here’s the command you need to make sure all the files on a USB device (D: in this case) are personal and not encrypted:
cipher.exe /d /s:D: *.*
That’s all it takes, it should finish in a minute or two.
[ad_2]
Source link




