[ad_1]
In this increasingly digital world, identity is the most attacked surface area, and the sophistication and frequency of attacks continue to rise. Manual investigations and responses can’t keep pace. We need to think differently about how we protect identities from compromise and respond rapidly to emerging threats.
Microsoft Entra ID Protection (recently renamed from Azure AD Identity Protection) helps stop attacks before they happen. ID Protection blocks identity takeovers in real-time and automates attack mitigation by providing advanced machine learning (ML)-based detections, risk-based access policies, and comprehensive risk reports and insights. To protect customers with our latest innovations, we’re excited to announce key enhancements to Microsoft Entra ID Protection: a brand-new dashboard to provide key insights, new detections to block existing attacks, a new mechanism for Microsoft to rapidly protect users from emerging threats, and the integration with Microsoft 365 Defender. Read below to learn more about these exciting new features.
New dashboard
We’re thrilled to present a brand-new dashboard in Entra ID Protection, a central hub designed to help identity admins and IT practitioners better understand their security posture and enable effective protections against identity compromises.
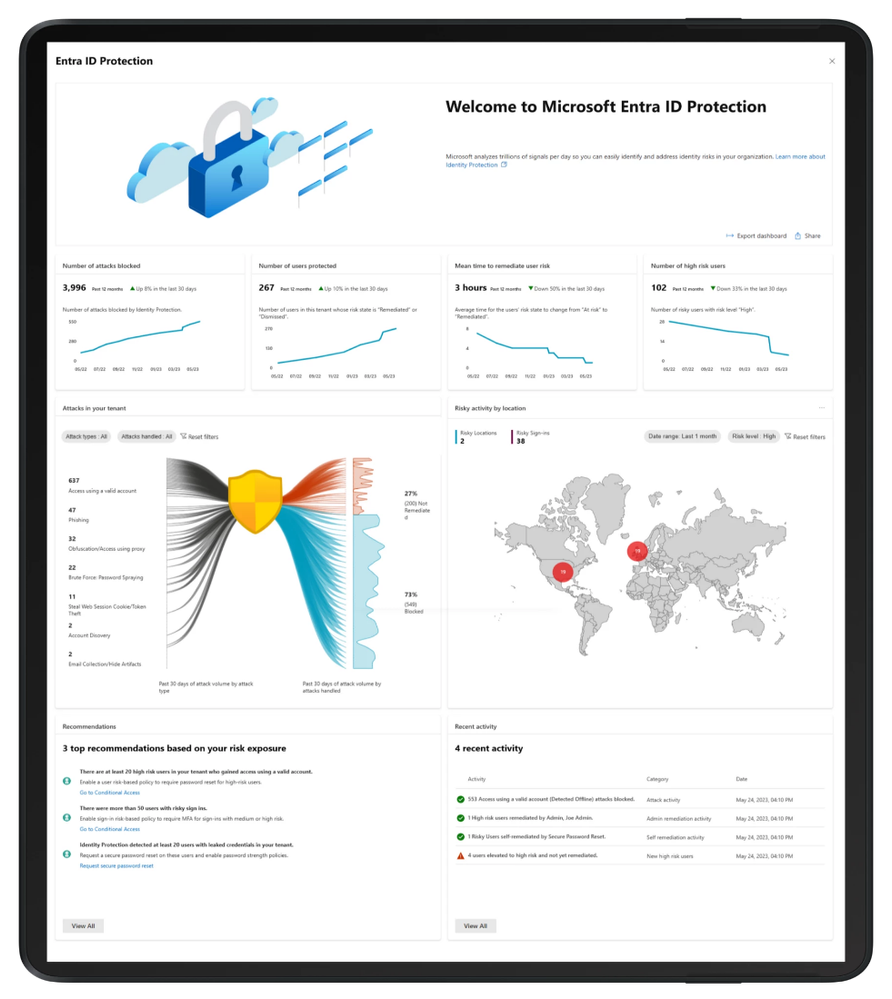
The new dashboard surfaces in-depth insights with compelling visualizations and actionable recommendations. These will help you and your identity teams answer questions like “How well is my organization protected?” “What kinds of attacks are targeting my organization right now?” and “What should I do to address those attacks?”
As you increase security measures by using risk-based conditional access policies and modern strong authentication policies, the protection of your tenant is gradually strengthened. You’ve asked for better insight into how well you’re protected over time, so we now provide four key metrics with monthly trends to demonstrate the effectiveness of your deployed protections. The number of attacks blocked and users protected metrics can demonstrate the effectiveness of your security measures, and mean time to remediate highlights how quickly your organization is able to respond to and recover from possible compromises. By adopting automated capabilities like risk-based policies and self-service password resets, you can significantly boost your recovery speed, enhancing security and operational efficiency. Finally, high risk users gives insight into how much account compromise risk you are carrying over time.

To illustrate your risk exposure and where vulnerabilities lie, we’re thrilled to introduce our cool new attack graphic to help you visualize common identity-based attack patterns detected within the past 30 days for your tenant, and – more importantly – how many were successfully blocked, and how many still need to be remediated. These attack patterns are identified based on our advanced ML detections such as leaked credentials, anomalous token, password spray, and more.
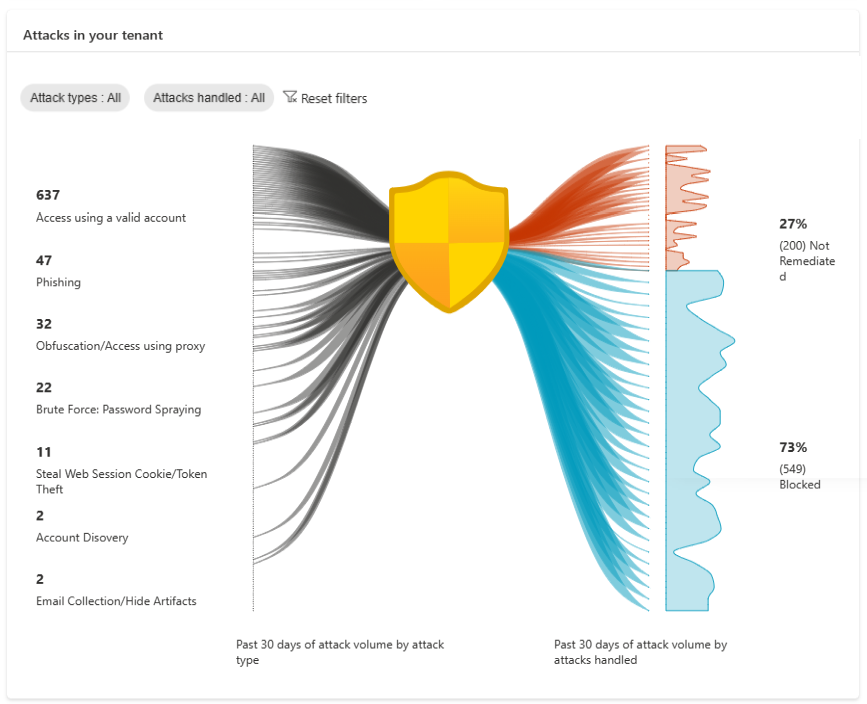
To help you take effective action, we’re offering tailored recommendations based on your risk exposure. For example, when we find that at least 20 high risk users in your tenant have gained access using valid accounts, suggesting possible compromises, a recommendation will be surfaced to suggest protecting these users with a user risk policy to bring these users back to a safe state effectively and efficiently. The attack graphic, alongside our recommendations, will equip you with targeted strategies to improve your security posture.
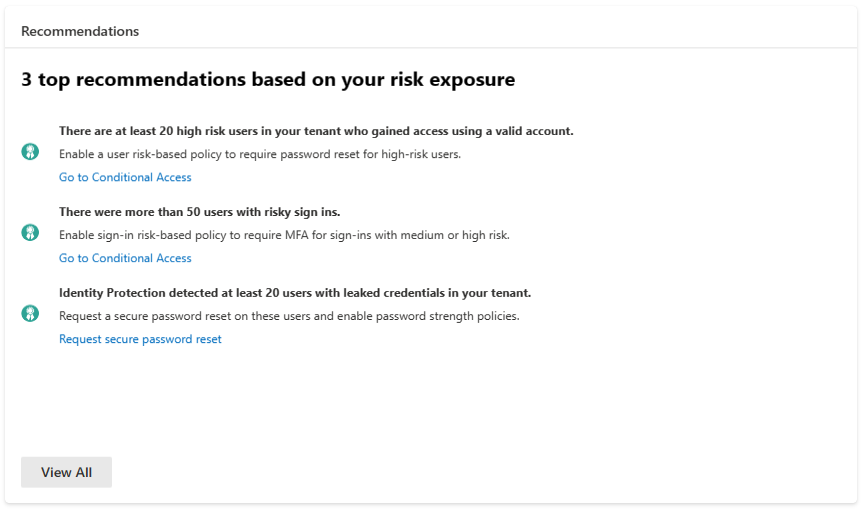
We’ve also integrated a map to shed light on the geographical origins of risky events. This interactive map gives a global perspective on the threats your organization faces.
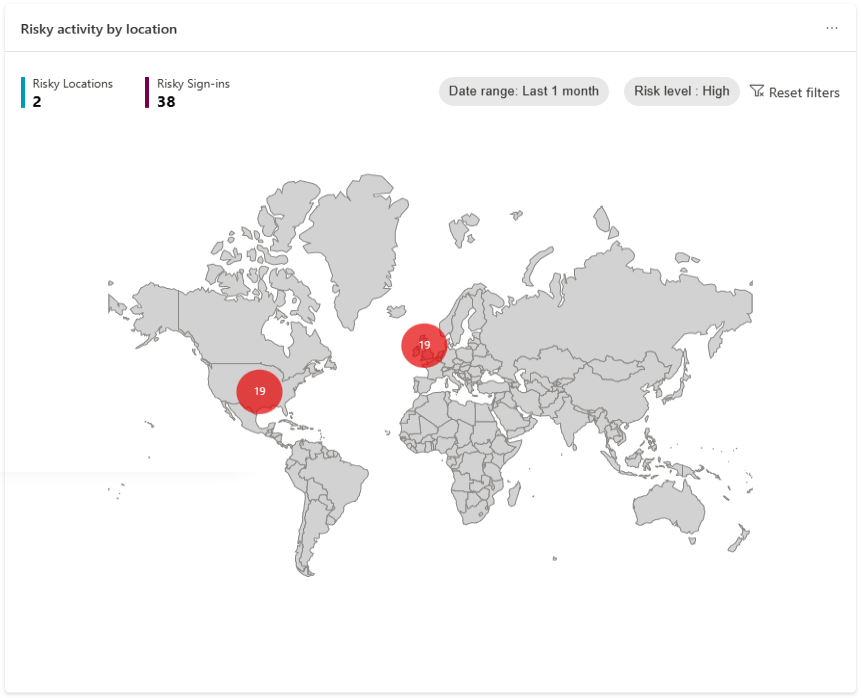
Lastly, our recent activity function gives you a summary of recent risk-related activities in your tenant. You will be able to see events such as what remediations have been done by admins or by users to catch any suspicious behavior.
The new dashboard will be an invaluable assistant to your identity teams, deriving accessible and digestible insights from complex data to enhance your understanding of your organization’s security landscape. Admins and SOC teams will be able to use it on a daily basis as well as share it with their business leaders to illustrate business impact.
The dashboard is currently in preview, and we can’t wait for you to try it out!
New advanced detections
When working on Microsoft Entra ID Protection, we always strive to provide our customers with new detections that can help protect their environment from malicious actors and activities. By leveraging the vast database of threat intelligence across Microsoft, we’ve now released two high fidelity detections that, in conjunction with risk-based conditional access policies, provide our customers with an opportunity to disrupt attacks at a very early stage.
The first detection is verified threat actor ID. In the past couple of years, a lot of the major security incidents have been initiated by known nation state actors and cyber-crime groups. By utilizing the research carried out by the various security teams at Microsoft, we’ve created a comprehensive knowledge base of these actors, which we now use to assign real-time sign-in risk to sign-ins performed by them.
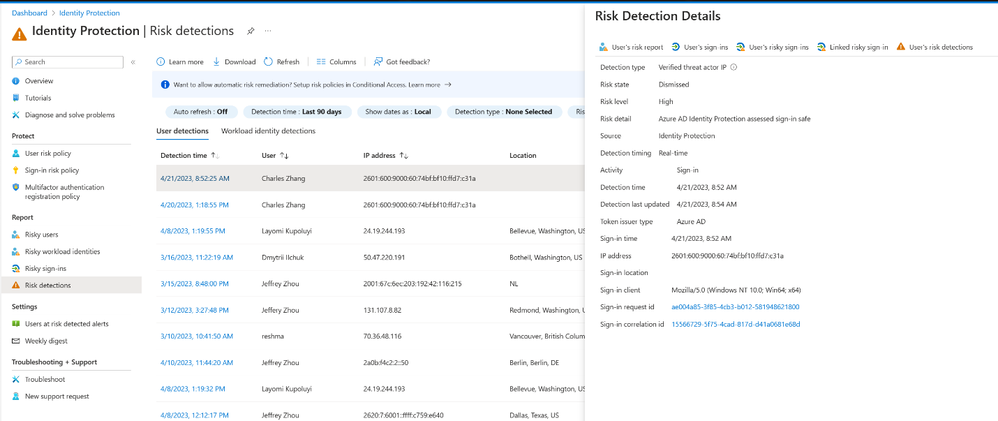
The second is attacker in the middle. One of the common scenarios used to gain access and compromise users is to use phishing, usually by way of a fake login experience, to get the user to enter their credentials and then proxy those credentials to a real session in Entra ID. Even if the user is prompted for multifactor authentication (MFA), since they are going through the expected login experience, it’s likely that they will successfully complete the login, thus providing the attacker with a working session and with the credentials to be used in future attempts.
We use signals provided by Microsoft 365 Defender, together with data from Entra ID, to accurately detect this type of attack and apply risk to both the affected sign-in and the user via the Azure AD threat intelligence detection, allowing customers to revoke the session by requiring a password reset and preventing future use of the credentials.
Both detections are now available to all ID Protection customers.
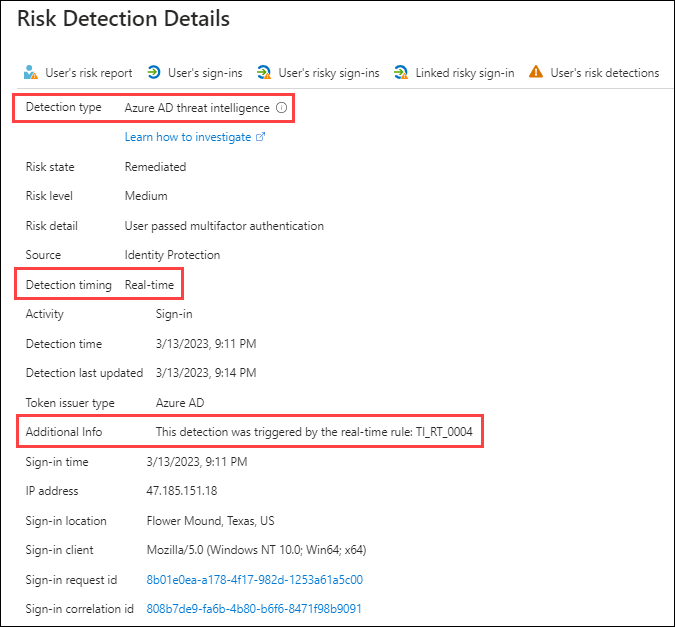
Real-time Azure AD threat intelligence
To protect customers from emerging identity-based attacks, Entra ID Protection now offers real-time Azure AD threat intelligence detections. When new attack patterns are identified, ID Protection can now rapidly issue new, real-time detections in response to these attacks. These detections will utilize Microsoft’s threat intelligence in real-time – meaning ID Protection will detect identified patterns of compromise during sign in, and customers will be able to leverage risk-based conditional access policies to protect their identities.
During a user sign-in, if the properties of that sign-in match the signatures of a real-time threat intelligence detection, the real-time risk evaluation engine in ID Protection will report the detection, elevating the risk level of the sign-in and the user, and enforce the access control configured in your risk-based conditional access policies to block or challenge the user, protecting your organization from malicious actors.
Customers will be able to investigate this detection in the risk detections report in ID Protection. The specific detection rule will be noted in the Additional Info field of the existing Azure AD threat intelligence detection.
For more information on real-time threat intelligence detections, click here.
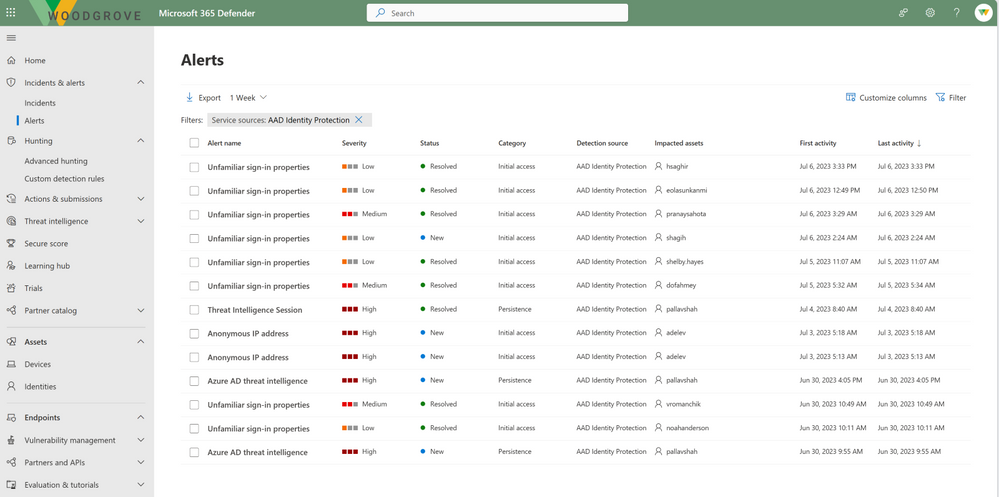
Generally available: Integration of Entra ID Protection with Microsoft 365 Defender
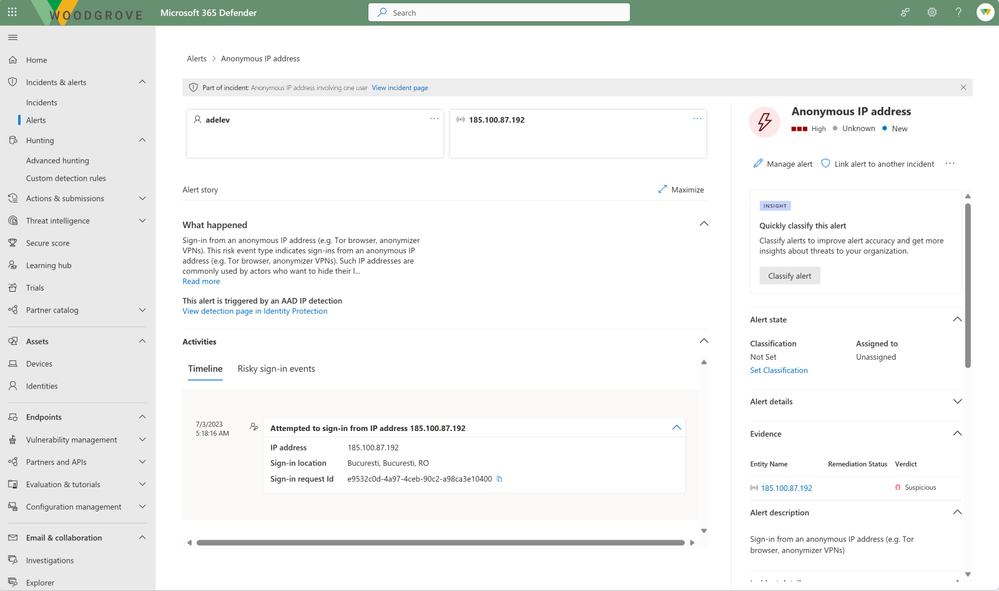
We’re also excited to announce that the integration of Entra ID Protection with Microsoft 365 Defender is now generally available. Entra ID Protection alerts are critical indicators of identity compromises and are generated by advanced detection algorithms. They’re now surfaced in Microsoft 365 Defender and are correlated into incidents along with alerts from the other security domains. Security teams will be able to investigate incidents efficiently and effectively, gaining a comprehensive understanding of end-to-end attacks and facilitating a quicker response to identity compromises.
These alerts are also available via the Microsoft 365 Defender Incident API, allowing you to track incidents involving Entra ID Protection alerts in Microsoft Sentinel or any other solutions.
On the Microsoft 365 Defender user page, you can now view a user’s risk score and provide feedback on potentially compromised risky users. When an investigation is concluded, the status of the incident and the alert can be updated and will automatically sync back to Entra ID Protection.
This seamless integration empowers customers to disrupt security attacks early on when identities are at risk of being compromised. Get started today by visiting security.microsoft.com and reviewing our documentation. We look forward to your feedback on this integration!
Conclusion
These exciting updates are another significant step towards our goal of providing customers with best-in-class identity security, with additional features and enhancements to be added as we continue to improve Microsoft Entra ID Protection.
To get the most value out of our product offering, customers are highly encouraged to follow the best practices and recommendations provided in the new dashboard, deploy risk-based conditional access policies, and utilize the new detections for automatic protection and remediation.
Stay safe out there,
Alex Weinert (@Alex_T_Weinert)
VP Director of Identity Security, Microsoft
Learn more about Microsoft Entra:
[ad_2]
Source link