[ad_1]
Greetings,
This is Sue Bohn, Director of Program Management for Identity and Access Management. In this Voice of the Partner blog post, we’ve invited Ajith Alexander, Head of Product Management at WhoIAM, a leading identity and access management (IAM) company, to share his experience around providing a more accessible, secure authentication and identity management solution leveraging Microsoft Azure Active Directory platform for big-brand consumer businesses across the world.
Enabling inclusive security with Azure Active Directory
by Ajith Alexander, Head of Product Management at WhoIAM
WhoIAM is headquartered in Bellevue, Washington, with engineering teams in the United Kingdom, South America, India, and here in the Pacific Northwest. Our team is focused on addressing the evolving challenges of identity security, working with clients to provide customized biometric and hardware-based authentication methods that fit their unique business needs.
WhoIAM operates simultaneously as both a systems integrator and an independent software vendor (ISV). As a systems integrator, we rely heavily on the Microsoft Identity Platform, including Microsoft Azure Active Directory (Azure AD) and External Identities. We mostly work with government clients and large consumer brands, helping them critically evaluate their current customer identity and access management (CIAM) architecture to better secure their end users’ identities, as well as upgrade the company’s digital ID solutions. As an ISV, we build customized CIAM extensibility apps that fill critical gaps for our clients.
The market landscape per WhoIAM
The global CIAM software market is projected to grow from USD 7.5 billion in 2020 to 15.3 billion by 2025. Today’s consumers expect companies to protect their personal information, and to do so in a way that won’t inconvenience or frustrate them. Our clients come to us because they have a brand that needs protecting, and part of their brand value hinges on providing seamless security. We help them deliver on their brand promise by using a carefully orchestrated combination of Azure AD External Identities for their CIAM needs, Dynamics Fraud Protection for account/payment protection and network penetration testing, and our own biometric and hardware-based authentication methods using WhoIAM’s Branded Identity Management System (BRIMS).
We work across multiple industries. In the government space, we work with agencies who need to protect their services from fraudulent use, such as during enrollment for health or unemployment insurance. In the private sector, we work with clients in the airline industry, big restaurant chains, and other big brands. Typically, these companies have millions of end users and many B2B relationships as well; therefore, they need support around preventing fraudulent transactions as well as secure payment processing.
The challenge: Inclusive security
IT decision-makers are usually quite tuned in to the challenges around the cost of acquiring new customers, keeping user data secure, and managing infrastructure costs. However, large groups of users are often left behind because of an inherent set of biases in identity security.
For instance, authenticator apps, while secure, require a reasonably tech-savvy user. On-device biometrics such as a fingerprint sensor or retina scan create a dependency on newer, more powerful hardware. SMS-based MFA, while more readily available, is expensive both to our client and their end customers and is considered less secure than other authentication factors. Even onscreen identity verification challenges tend to be biased towards English speakers who don’t have visual impairments. Asking a non-native speaker to solve a CAPTCHA that identifies all “sidewalks” or “stop lights” often does not translate well, and CAPTCHAs are historically a poor option for the visually impaired.
While these are important factors to solve for, consumer brands still have to strike the right balance between security, cost, and usability. Here are some of the important litmus-test questions we ask our clients as they adapt their user-identity strategy to be more inclusive:
- What are the added costs of implementing a new authentication factor?
- How disruptive—how many users do you risk losing because of changes to your existing sign-up or sign-in process?
- Is there a specific group of users who are unfairly impacted by your current set of authentication factors? Are there alternative authentication factors you can present to such users?
Solution: Azure AD B2C, Dynamics Fraud Protection, and BRIMS
We use a layered approach of Azure AD B2C, Dynamics Fraud Protection, and BRIMS to learn as much as we can about the user and their specific scenario or situation up front. We then make in-flight decisions on authentication factors as they sign-up or sign-in to an app or site.
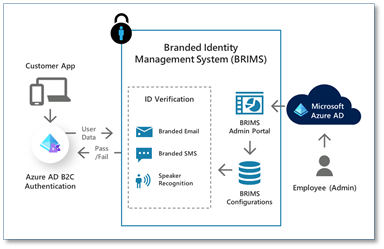
Figure 2: WhoIAM BRIMS (Branded Identity Management System) runs on Azure AD
To begin, we use Dynamics Fraud Protection’s device fingerprinting and risk detection, which works by embedding a small piece of JavaScript on an app’s pages. We use Fraud Protection’s scores to get two broad categories of assessments even before a user begins an authentication journey:
- Per-transaction assessments: These help us examine each access request individually; evaluating the likelihood of the transaction being a bot, as well as determining the type of device and the location from which the connection originates.
- Macro-trends-based assessments: We’re also able to keep track of metrics, such as users experiencing low completion rates for authentication.
Subsequently during authentication, Azure AD B2C calls an intermediate API that checks Fraud Protection’s rules engine, as well as the individual user’s risk scoring, and then responds back. Combined with Azure AD Identity Protection, this information enables us to configure rules so that Azure AD B2C can present authentication journeys that are aware of the user’s specific scenarios as they attempt to interact with an application. Being able to identify a user as being low-risk for being a bot allows us to bypass an unnecessary human-or-not check that may have inclusivity challenges. Similarly, being able to spot groups of users with low authentication completion rates can be used to identify issues such as an inability to understand the on-screen instructions, or not knowing how to interact with complex hardware capabilities on their device.
Using voice biometrics for verification is also a powerful tool for implementing inclusive security. Human voices are readily available, can be recorded in a contactless way, and do not require specialized hardware. Our voice carries an imprint of our identity that comes through regardless of what we’re saying, what language we’re speaking, or where we’re speaking from. This makes voice biometrics an ideal choice for catering to users who are visually impaired, have difficulty reading or understanding a language, don’t have access to a dedicated personal device (residents at assisted-living communities, shift-workers), or live in less developed areas that rely on fixed phone lines.
For such users, we enable BRIMS voice biometrics, which relies on Deep Neural Networks (DNN)-based speaker recognition technologies developed by our partner, Oxford Wave Research. For voice biometrics to work accurately, we need a short recording of a person’s speech. BRIMS uses a combination of speaker recognition (who said it), as well as automatic speech recognition (What did they say?) to accurately identify a user. For the visually impaired, we prompt the user to respond to a knowledge-based question, such as their name, employee ID, or their favorite city. For other users who have difficulty reading an onscreen prompt due to a language barrier, we present an image for them to describe instead. Creatively solving for flexible, inclusive user verification ensures we can log in previously marginalized customers securely without identity verification being a frustrating experience.
Results: Azure AD and Dynamics Fraud Protection help us compete
For WhoIAM, betting on the Microsoft Identity Platform makes a lot of sense, and we’re looking to expand our footprint in Azure to achieve our goal of inclusive security. Because of Azure AD B2C’s design flexibility with its policy engine, and Dynamics Fraud Protection’s customer signaling from sign-in to sign-out; we’re able to weave in full-circle alerting and real-time decision making. This enables us to present our clients with strong security that’s both inclusive and affordable. Additionally, the availability of the entire Azure stack across Azure Key Vault, Azure App Service, Azure Cosmos DB and a whole slew of complementary products on the same Azure subscription is invaluable. This makes it easy for us to put together highly customized identity architectures for our clients while using Azure as a one-stop shop.
Learn more about Microsoft identity:
Source link