[ad_1]
I have been building Windows 10 images based on the Windows 10 20H2 media and seeing repeated failures on the “Security Intelligence Update for Microsoft Defender Antivirus – KB2267602” installation. When doing this as part of an MDT image creation task sequence, that failure ends up happening over and over again, as MDT detects the failure, reboots the computer, and then tries it again, only for it to fail again. The same error occurs even after all other updates have successfully installed (e.g. the latest cumulative update, servicing stack, etc.).
Looking at the WindowsUpdate.log, you can see three distinct error codes:
2021/04/03 22:09:22.3989998 9200 8576 Handler * START * Command Line Install Updates to install = 1
2021/04/03 22:09:27.7566112 9200 8576 Handler Command line install completed. Return code = 0x8050800c, Result = Failed, Reboot required = false
2021/04/03 22:09:27.7567234 5752 1012 UDP Deployment job Id 8F66F51F-0CD4-448A-8B43-578B63A9D92E : Update 3449C0BE-3FD1-4AC1-812A-E11A6C9E014E.200 failure delegate invoked.
2021/04/03 22:09:27.7567557 9200 8576 Handler * END * Command Line Install 0x8024200b
2021/04/03 22:09:27.7579882 5752 4652 UDP FAILED [80070643] Deployment job Id 8F66F51F-0CD4-448A-8B43-578B63A9D92E : Installing for Top level update id 3449C0BE-3FD1-4AC1-812A-E11A6C9E014E.200, bundled update id DA7FBA23-069E-4244-87B4-58C56B57DD54.200 [CUpdateDeploymentJob::DeploySingleUpdateInternal:2790]
The 80070643 error code is what gets logged by MDT and shown on the Windows Update settings page. By itself, that code isn’t very useful since it just means “error 1603, fatal error during installation.” But the original 8050800C error code finds a variety of instances over the years. One approach suggested was to follow this Microsoft page:
https://www.microsoft.com/en-us/wdsi/defenderupdates
That includes a section called “Trigger an update” that lets you update the Defender definitions using some simple commands. I built my own PowerShell equivalent:
& “$($ENV:ProgramFiles)Windows DefenderMpCmdRun.exe” -removedefinitions -dynamicsignatures | Out-Host
& “$($ENV:ProgramFiles)Windows DefenderMpCmdRun.exe” -SignatureUpdate | Out-Host
Pretty simple. I then inserted that into my MDT task sequence prior to the Windows Update step:
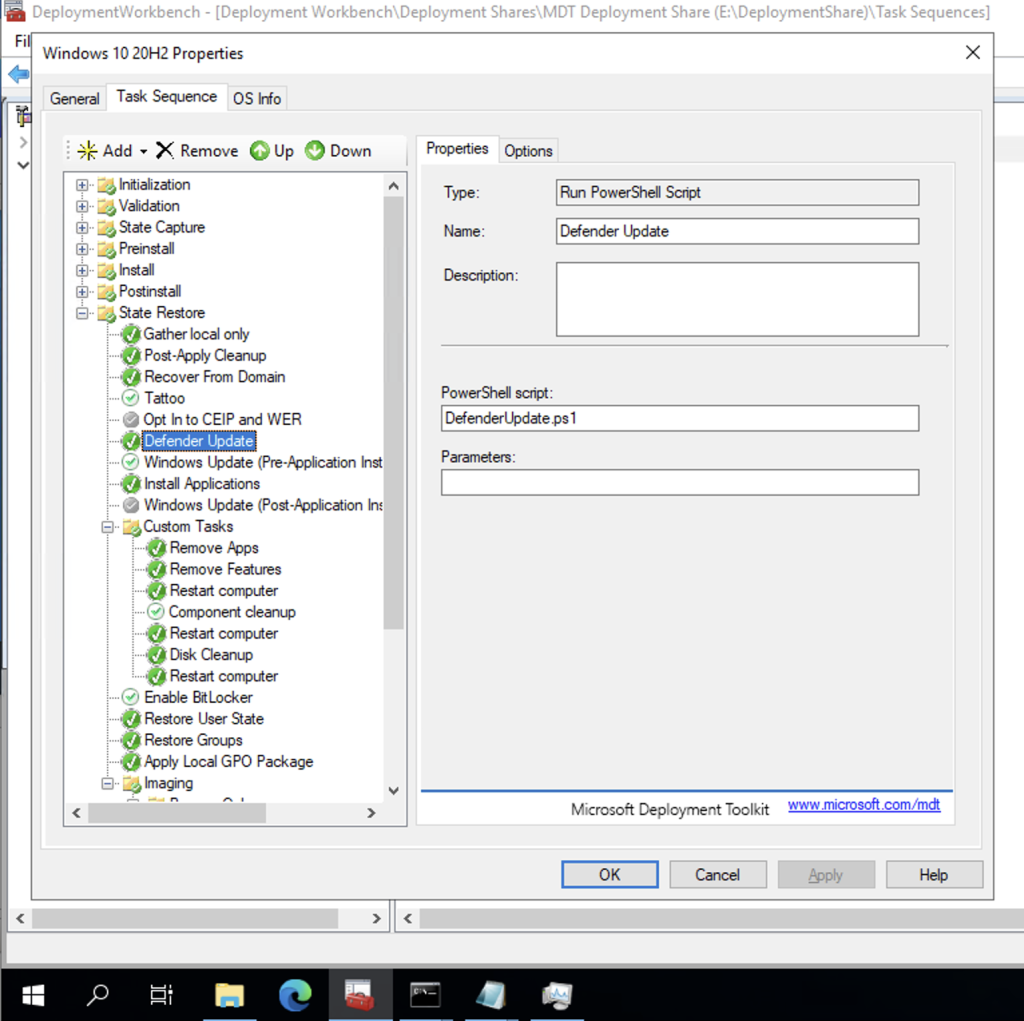
With that done, the latest definition updates were installed prior to Windows Update. Windows Update then detected that it didn’t need to install the Defender update at all, and the Windows Update step completed after a single pass with no errors.
Now it’s quite possible that the “next” definition update from WU causes an error again, so check the machine a week or so later to make sure that it is still installing definition updates without any errors.
I did check the server after the next definition update was published and it did successfully install, so it’s quite likely the commands are enough to “clean up” the problem.
[ad_2]
Source link




