[ad_1]
Supporting hybrid work as threats and attacks continue to escalate has required collective resilience. No matter how strong your cyber defenses are, you still have to contain any disruptions that arise—whether from security issues, crises, or even good challenges like exponential business growth—so that your organization can keep operating while you recover as quickly as possible.
As your partner, we’re making investments in Azure AD to help your organization stay protected and productive. These investments, which span underlying platform capabilities, security, and multi-cloud, are the topic of my session this week at Microsoft Ignite: we’re building a more resilient identity service, tools that detect and respond to hard-to-identify attacks, and systems that strengthen the security posture of your entire digital estate.
A more resilient identity service
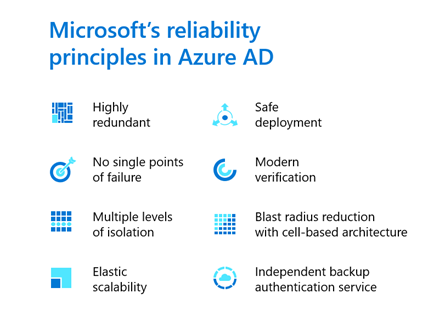
We understand how crucial Azure AD is to your organization. After all, if people can’t sign in, they can’t get anything done. We know we have to continuously re-earn your trust, so we’re continuously investing in service reliability based on eight core principles.
Our work includes unique innovations to ensure we can deliver on our 99.99% SLA commitment. For example, we’ve adopted a cell-based architecture for the entire Azure AD service. We’ve divided the service across cells so that if an unexpected fault occurs in one part of the service, we can contain it and avoid distressing other parts of the service. As of today, Azure AD is split across 107 cells. Since even the largest cell can reach at most 1.7% of system users at any given time, a fault incident won’t have any effect on the vast majority of customers.
We’ve also invested in a backup authentication service, a secondary system that keeps sessions alive even if the primary authentication system is down. While this system also runs within the Microsoft cloud, it’s completely separate from the primary Azure AD service. Behaving much like a generator during a power outage, it takes over active sessions to give users an identical experience when accessing apps. It also maintains security settings and access compliance, for example, applying Conditional Access policies or modifying access based on role changes. The backup service is active today for Exchange and SharePoint workloads, as well as for all native desktop and mobile apps. By the end of this year, it’ll work with all web apps as well.
|
Announcements: · Azure AD backup authentication service supporting web application workloads by end of 2021 |
Tools that detect and respond to hard-to-identify attacks
Attacks against identities are intensifying. In fact, identity has become the new cybersecurity battleground, making tools for prevention and detection more critical than ever.
To strengthen prevention, we’re adding several enhancement to Azure AD Conditional Access, the access policy engine at the heart of Microsoft’s Zero Trust architecture.
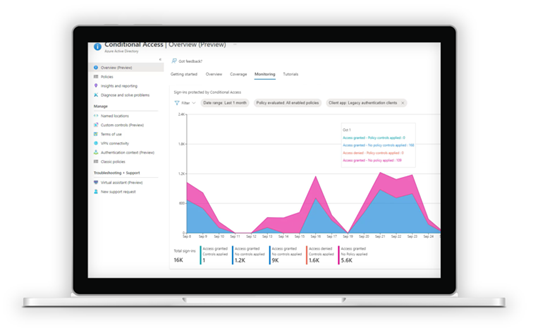
- A new Conditional Access overview dashboard identifies opportunities to strengthen policies based on analysis of your organization’s sign in patterns. You can quickly deploy additional protection via pre-built templates constructed from Azure AD security best practices. Both the dashboard and templates are in public preview.
- You can hone policies to your specific needs with more granular policy targeting, including Conditional Access filters for applications and devices. Applied dynamically to new apps or devices, these filters allow you to build policies that, for example, only allow access to sensitive apps on devices that are compliant, hybrid domain joined, and defined as a secure access workstation. Filters for devices are now generally available, while filters for apps will be in public preview by the end of the year.
- Non-human identities (workload identities for apps and services) are gaining more access privileges and more attention from bad actors. You can now design policies to target these types of identities using Conditional Access for workload identities, which will be in public preview later this month.
- Continuous Access Evaluation extends Conditional Access into each individual session and enforces policies in near real time whenever a new risk arises. This feature will be generally available by the end of the year.
Even with strong prevention capabilities at play, a Zero Trust approach always assumes breach. In Azure AD, Identity Protection provides real-time intelligent risk assessment to detect and remediate threats and attacks. We’ve strengthened Identity Protection with several new features, now generally available:
- We’re adding new proactive detections to stay ahead of both common and emerging attack vectors, such as detections for anomalous tokens and unfamiliar sign-in properties for session cookies.
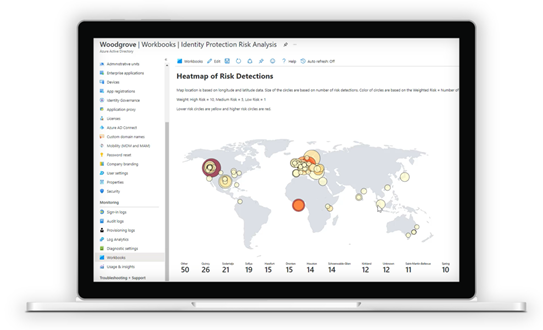
- By continuously analyzing user and access activity across your environment, Identity Protection generates significant data you can use to identify risks and fortify weaknesses. Identity Protection diagnostic settings let you export risk data to the SIEM of your choice with one click and easily customize the data retention period. A new Identity Protection risk analysis workbook, built on Azure Monitor, helps you visualize your risk data and the effectiveness of your response.
Keep in mind that staying resilient also means preserving the ability of your workforce and extended team members to collaborate in the face of disruption. Azure AD supports a secure and boundaryless collaboration experience in Microsoft Teams.
|
Announcements: · General availability of Identity Protection token theft detections · General availability of Identity Protection diagnostic settings · General availability of Identity Protection risk analysis workbook · General availability of Conditional Access filters for devices · General availability of Continuous Access Evaluation by end of 2021 · Preview of Conditional Access overview dashboard · Preview of Conditional Access templates · Preview of Conditional Access for workload identities later in November 2021 · Preview of Conditional Access filters for applications by end of 2021 |
Systems that strengthen the security posture of your entire digital estate
Not only are attacks becoming more sophisticated, but with the adoption of hybrid and multi-cloud strategies and the explosion of human and workload identities, so is your environment. Ensuring the Zero Trust principle of least privilege in complex environments is challenging, because cloud providers follow different operating models for governing access.
Most organizations are adopting a multi-cloud strategy so they can choose the apps and solutions that best fit their business. We want to ensure we protect your entire environment—not just the parts that run in the Microsoft cloud. To that end, we acquired CloudKnox earlier this year. The CloudKnox technology helps organizations discover permissions, assess and remediate risk, and detect anomalous activity for all identities and all resources across all major clouds. We’ll share more in the comping year as we work to integrate these powerful capabilities with Azure AD and the broader Microsoft ecosystem.
We’re working to deliver a unified multi-cloud solution that spans identity provisioning, lifecycle management, workflow automation, permissions management, and analytics. To advance this strategy, we’ve extended Azure AD Identity Governance to include provisioning to apps hosted on-premises or in private clouds, or to those with separate governance systems (i.e., apps relying on an underlying SQL database or third-party LDAP directory). Now you can provision access consistently across all your applications.
We’re also making it easier to manage user provisioning and lifecycle with custom entitlement workflows based on Azure Logic Apps, which has connectors to hundreds of existing systems—including Salesforce, Office 365, and SQL—that don’t require custom coding.
|
Announcements: · Preview of on-premises application provisioning from Azure AD · Preview of Azure AD entitlement management custom approval workflows |
Modernizing your authentication infrastructure
So that you can benefit from all the security advancements only available in the cloud, our teams are continuously working on new ways to help you shift more workloads to the cloud. For example, you can accelerate migration of your app authentication path from on-premises Active Directory Federation Services (AD FS) to Azure AD with previews of new claims, claim transforms, token filtering, and additional SAML configuration settings.
You can also adopt more secure practices that make secrets, especially those of workload identities, less vulnerable. Many application developers still use password secrets on their app registrations, some with long lifetimes. With the preview of new authentication method policies available in Microsoft Graph, you can do things like block the use of password secrets, limit their lifetime, or enforce a maximum lifetime on workload identity key credentials. Also in preview is GitHub Actions support for workload identity federation with Azure AD. This will give app developers an alternative to creating and storing Azure AD credentials in the GitHub repo when they deploy applications to Azure.
|
Announcements: · Preview of new claims, claims transformations, token filtering, and SAML configuration settings in Azure AD · Preview of new authentication method policies for apps and workload identities · Preview of GitHub integration with workload identity federation |
To see these features live on on-demand, register for free at Microsoft Ignite and watch my session Strengthen resilience with identity innovations in Azure AD starting at 1:30 PM Pacific Time today. And stay tuned to this blog space in the coming weeks for deeper dives on these capabilities and best practices for deploying them in your organization.
Learn more about Microsoft identity:
Source link